Single Sign-On (SSO) for Appspace Cloud
Introduction
Appspace 5.6 introduces the Single Sign-On (SSO) integration feature for cloud deployments allowing an Appspace Cloud user access to multiple apps in Appspace with a single user credential.
With SSO, Appspace Cloud accounts can now be configured to integrate with Security Assertion Markup Language (SAML) 2.0 compliant identity providers, allowing for seamless and secure connections using a single set of credentials, simplifying username and password management.
A user starts by logging in to Appspace. The user will then have to authenticate his or her login credentials against the Identity Provider. Upon successful authentication, the Identity Provider will send a SAML assertion to Appspace via the web browser to allow the user to login to Appspace.
This guide is based on the Active Directory Federation Services (AD FS) being the Identity provider, while Appspace is the Service Provider.
Prerequisites
- An Identity Provider that is SAML 2.0 compliant.
- IdP metadata, or the SSO Url and x.509 certificate.
- You must be an Account Owner.
Section 1: Installing the AD FS server
Note
This can be performed on the AD server or on a separate server.
Download the Active Directory Federation Services 2.0 software, by navigating to ‘http://www.microsoft.com/en-in/download/details.aspx?id=10909‘, and clicking the Continue button.
Select the Windows Server version used, and click Next to start the download.
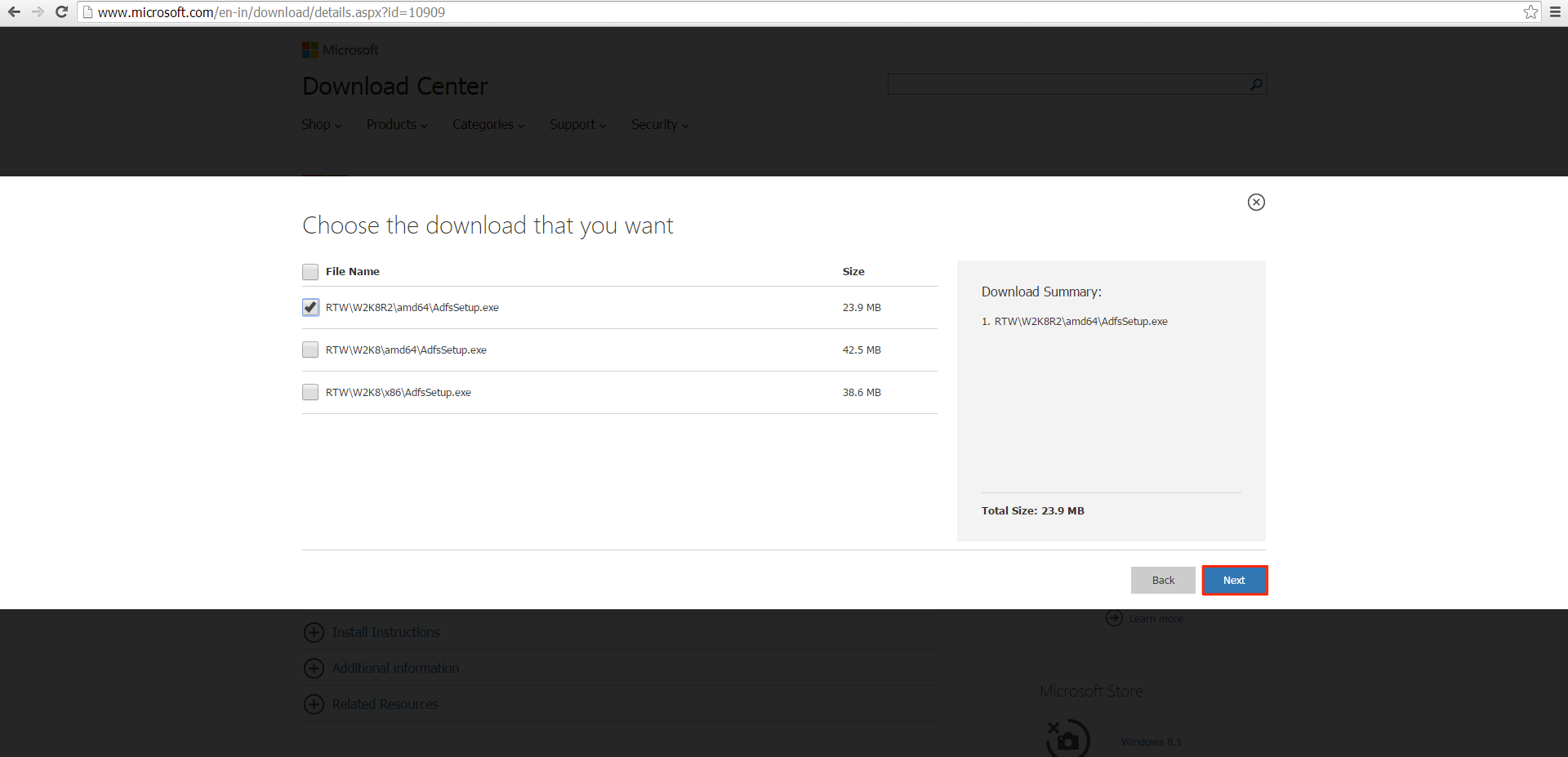
Note
RTW/W2K8R2/amd64/AdfsSetup.exe – This is for Windows Server 2008 R2 SP1
RTW/W2K8/amd64/AdfsSetup.exe – This is for Windows Server 2008 R1 SP2 64bit
RTW/W2K8/x86/AdfsSetup.exe – This is for Windows Server R1 SP2 32bit
Once the download is complete, locate the .exe file and double click it.
Click Run.
In the Active Directory Federation Services 2.0 Setup Wizard, click Next.
Check the checkbox to agree to the EULA, and click Next.
Select the “Federation server” option, and click Next.
Click Next.
Check the “Start the AD FS 2.0 Management snap-in when this wizard closes” checkbox, and click Finish.
In the AD FS 2.0 Federation Server Configuration Wizard window, select the Create a new Federation Service option, and click Next.
Select the “Stand-alone federation server” option, and click Next.
The wizard automatically detects the SSL certification used. The details of the SSL certificate, and the Federation Service name will be populated automatically if your SSL certificate is valid. Click Next to proceed.
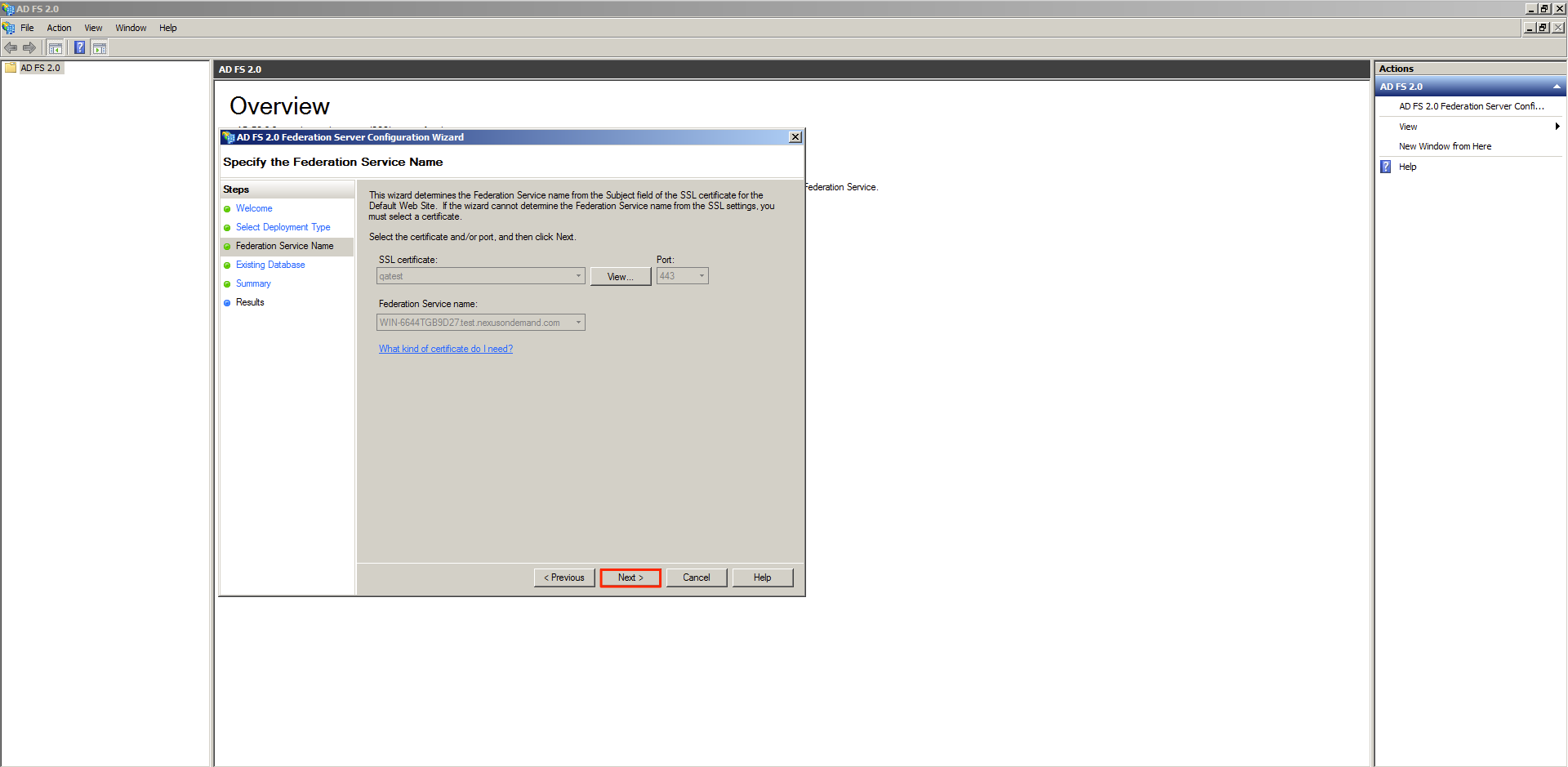
Click Next.
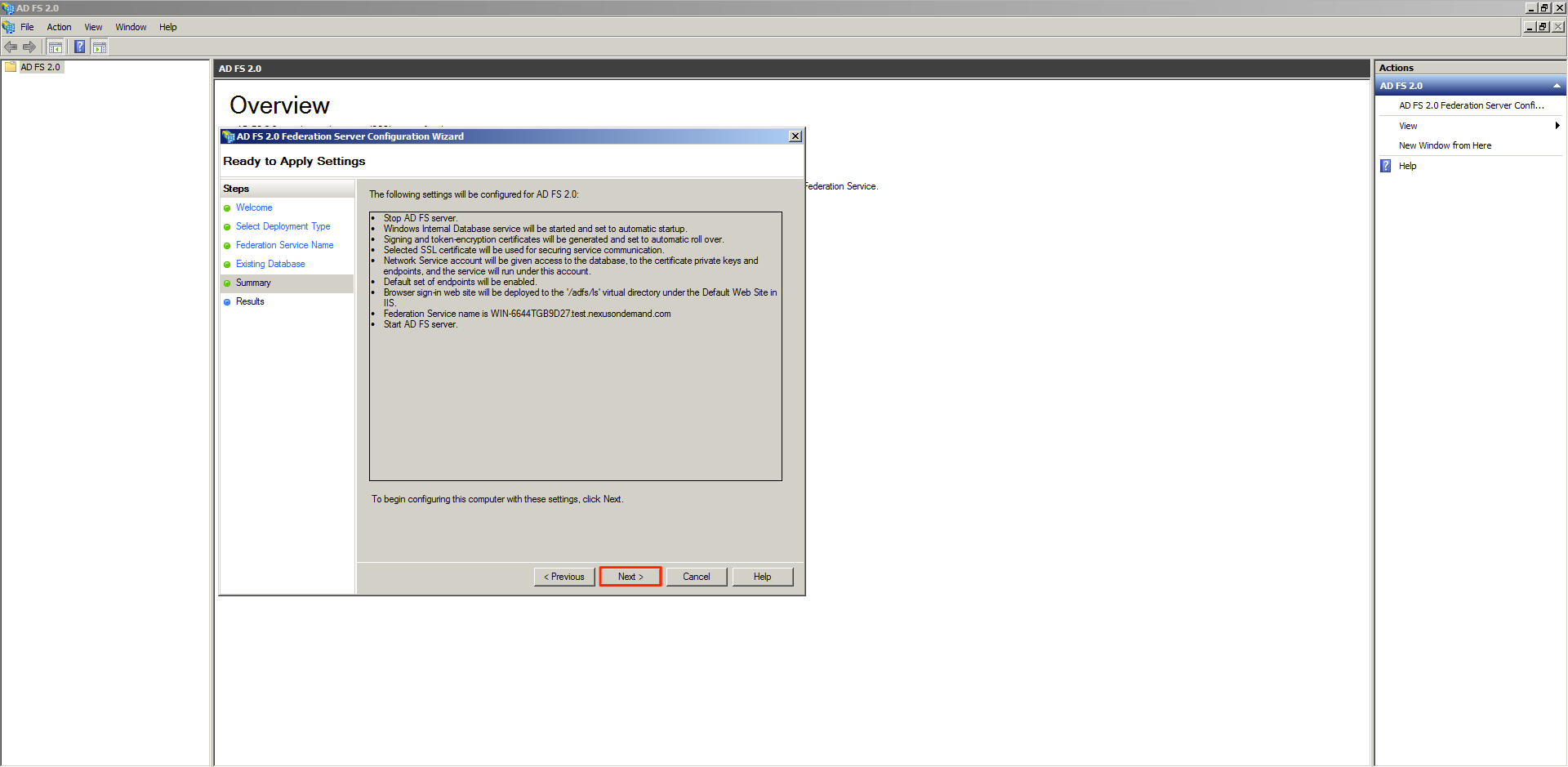
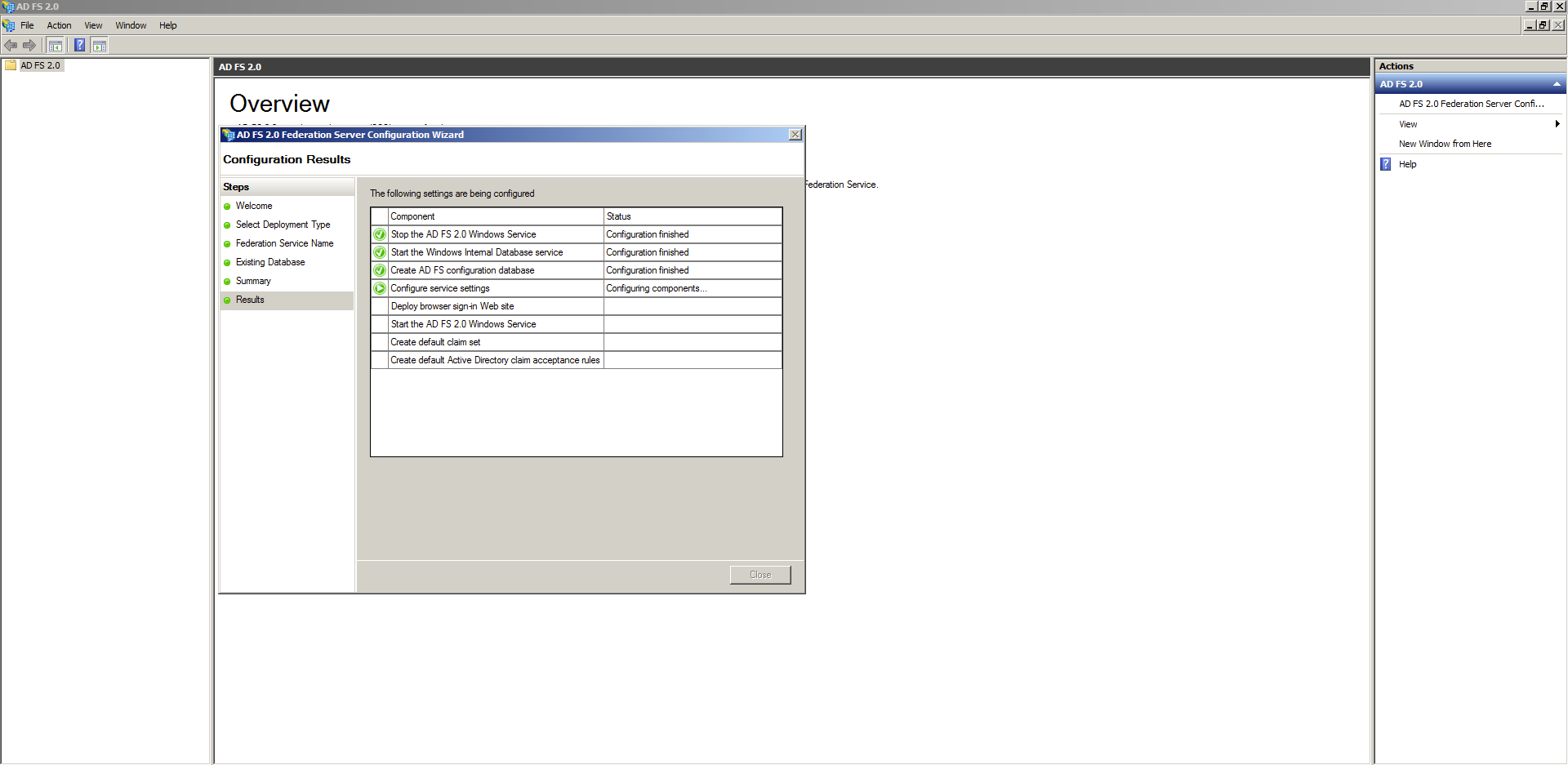
Once configuration has been completed, click close.
Section 2: Enabling and Configuring SSO
To enable SSO Authentication, follow the instructions below:
Download the Idp metadata by navigating to the following URL: https:// <ADFSFQDN or IP>/FederationMetadata/2007-06/FederationMetadata.xml
Note
This metadata is used by the Identity Provider (AD FS) to recognise the Service Provider (Appspace). This process involves downloading the metadata in xml format, uploading to and re-downloading from Appspace and finally re-uploading it to the Identity Provider (ADFS).
Log on to Appspace cloud, click the Appspace extensions drop-down menu, and select System > Account.
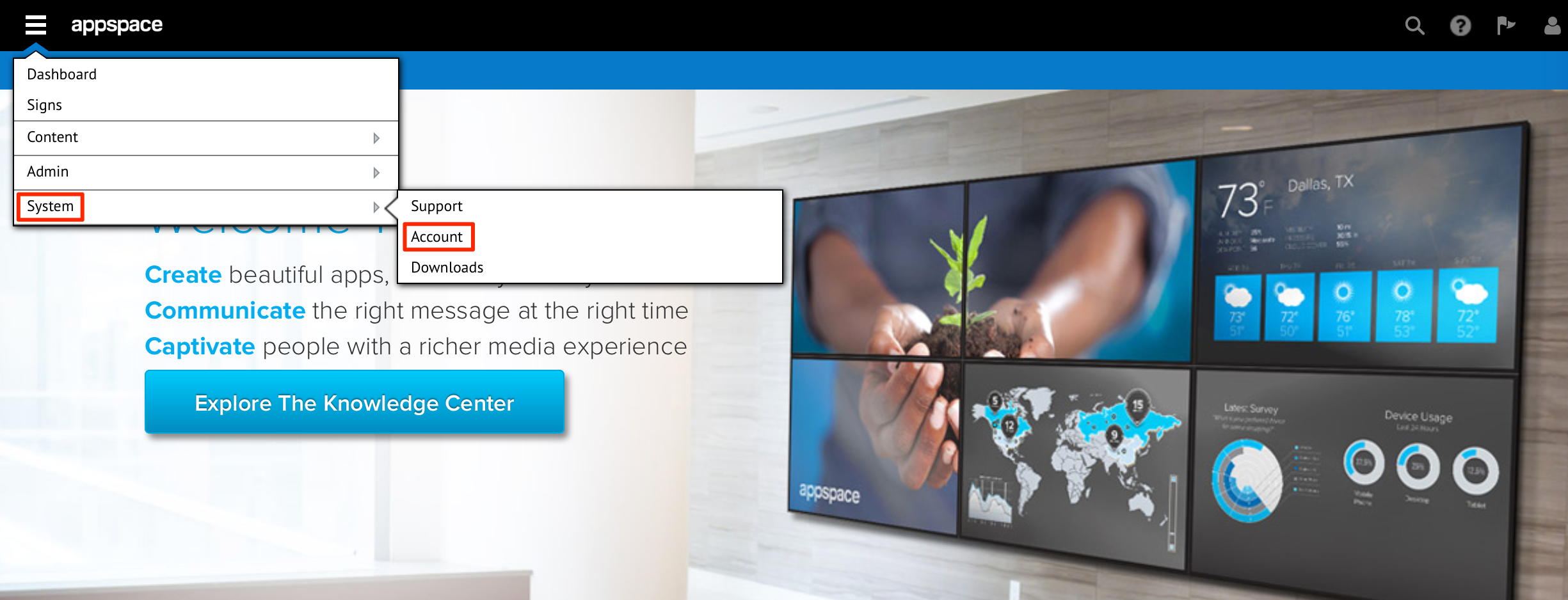
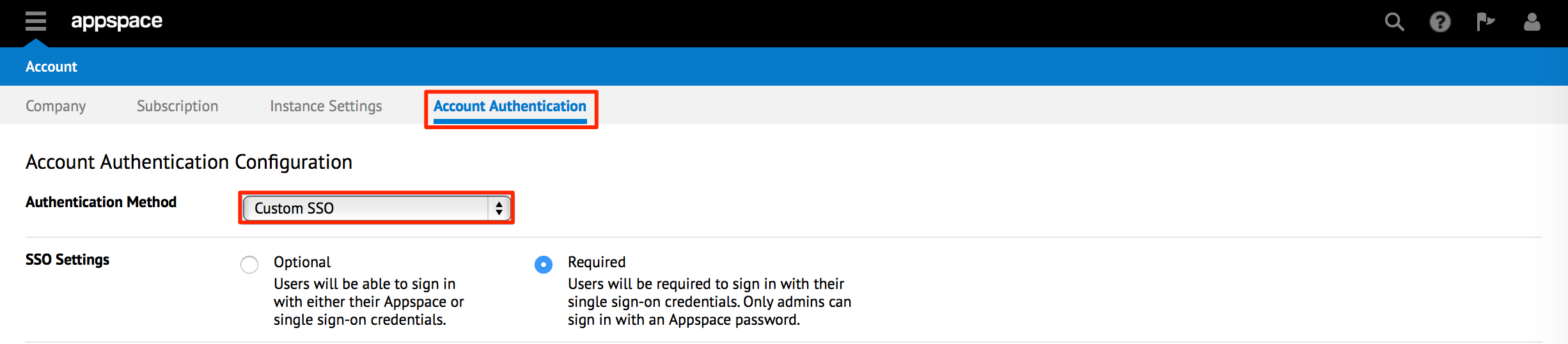
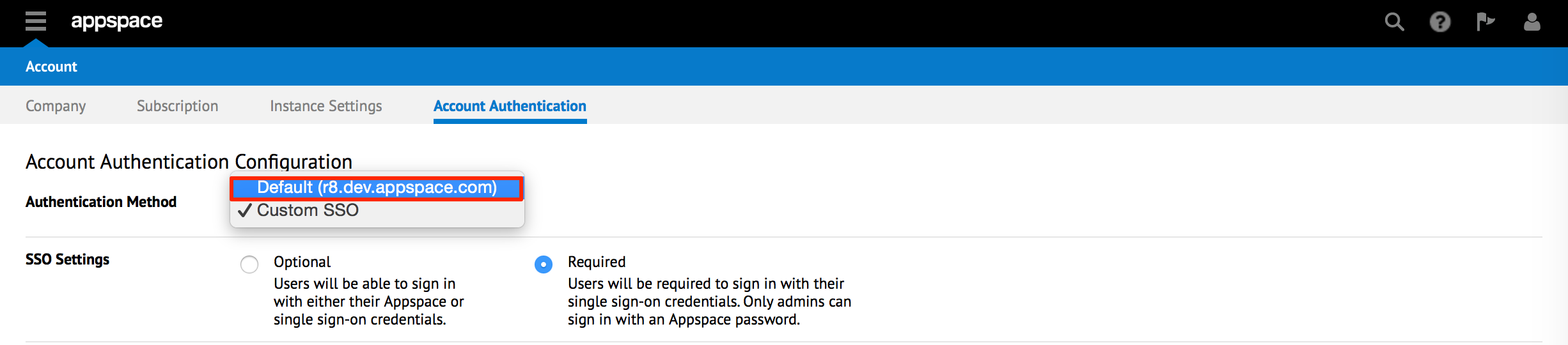
Click the Account Authentication tab.
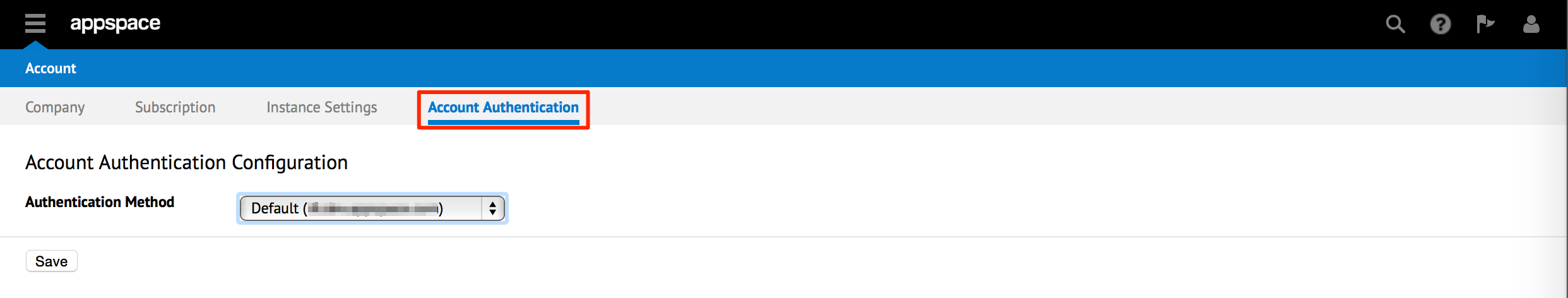
Set the Authentication Method to Custom SSO via the drop-down menu.
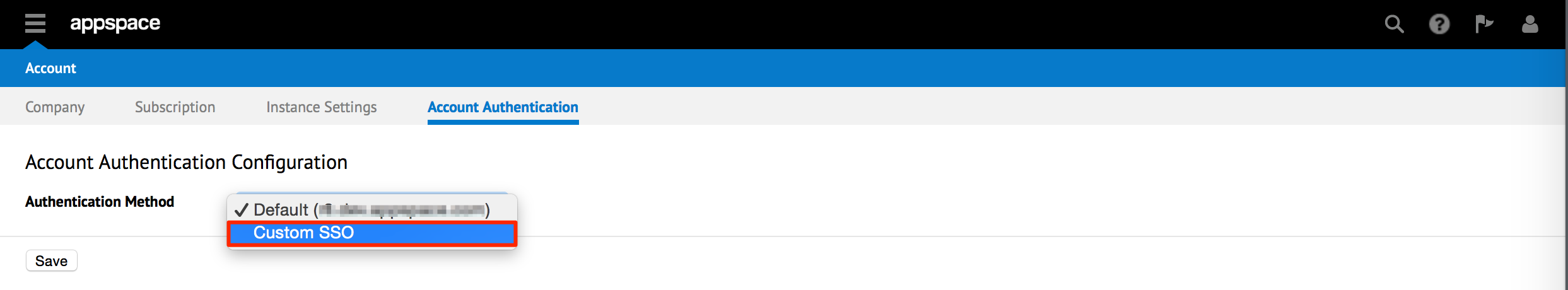
Set the desired SSO Settings to either Optional or Required, depending on the authentication implementation.
- Optional - Users can login with their Appspace credentials, or Single Sign-On credentials (AD credentials).
- Required - Users can only login with Single Sign-On credentials (AD credentials). Only admins are able to login using an Appspace credential.
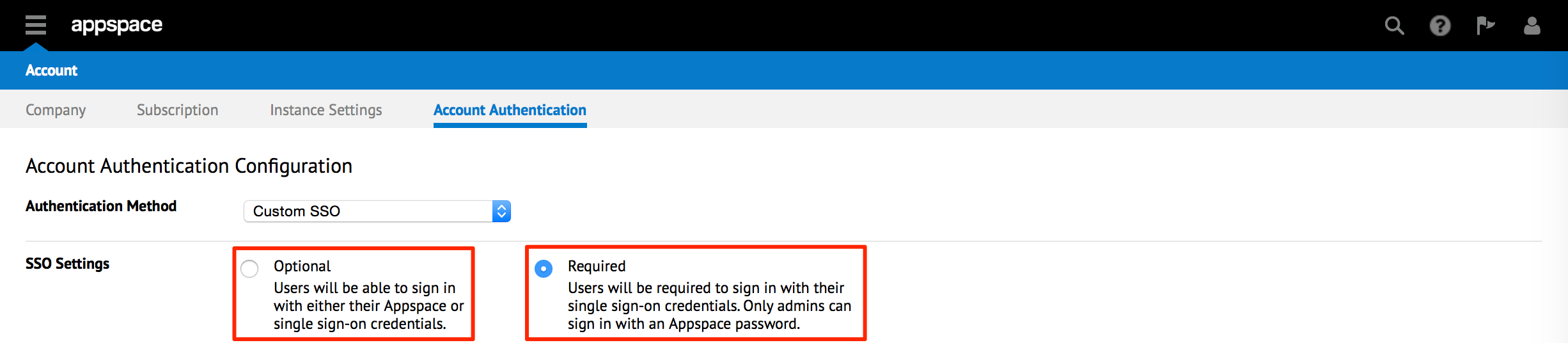
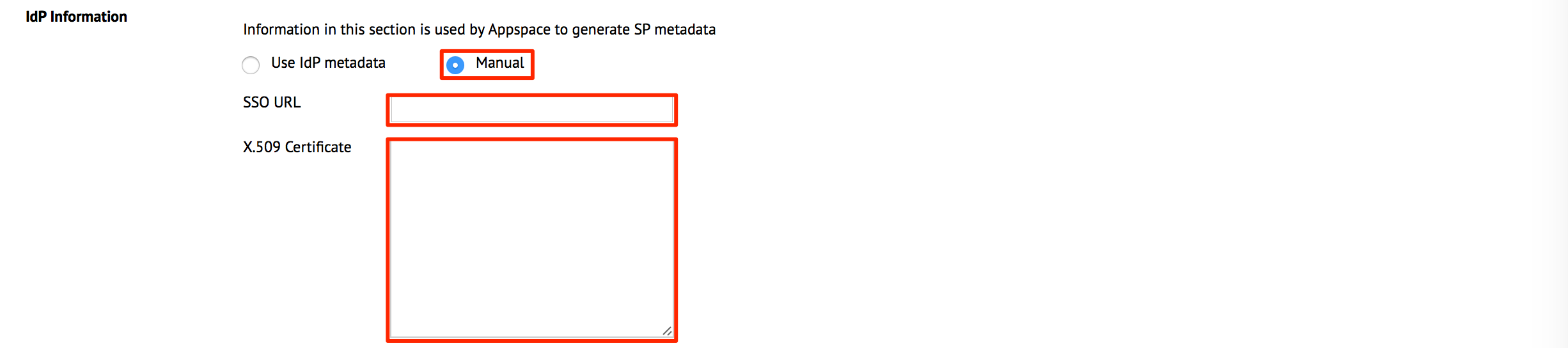
In the IdP Information section, select the ‘Use IdP metadata’ option, and upload the IdP Metadata XML file that was previously downloaded.
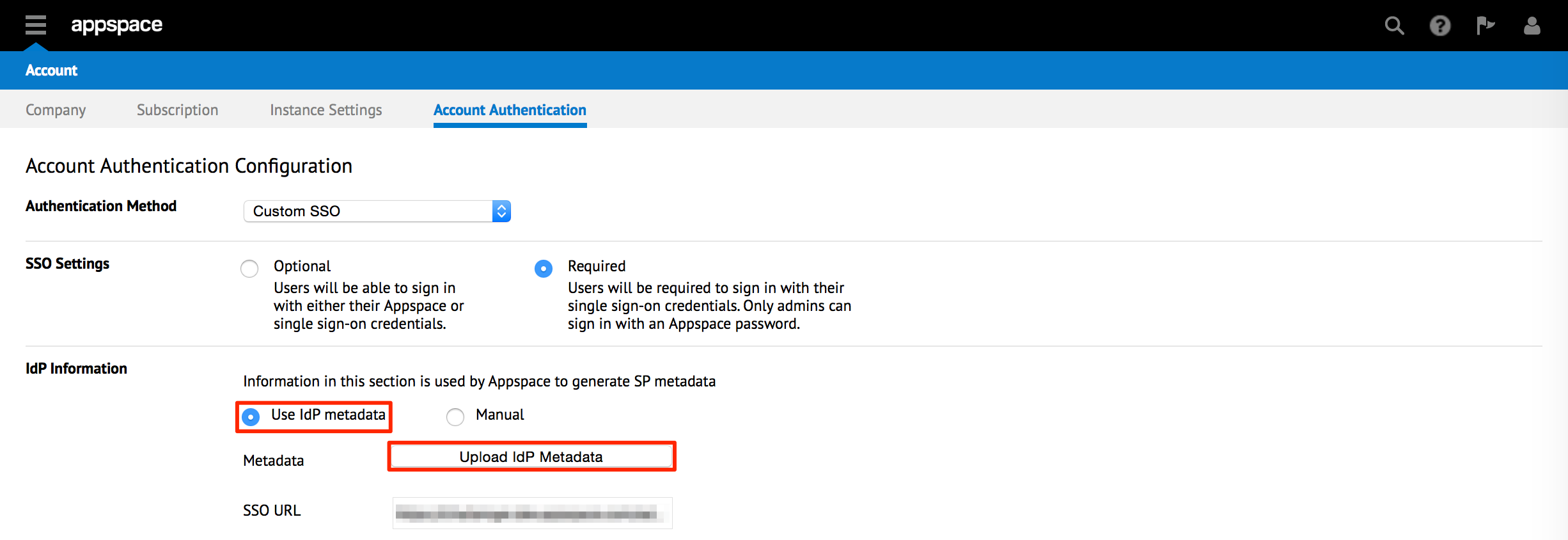
Alternatively, select the Manual option, and enter in the SSO URL and X.509 Certificate data manually in the fields.
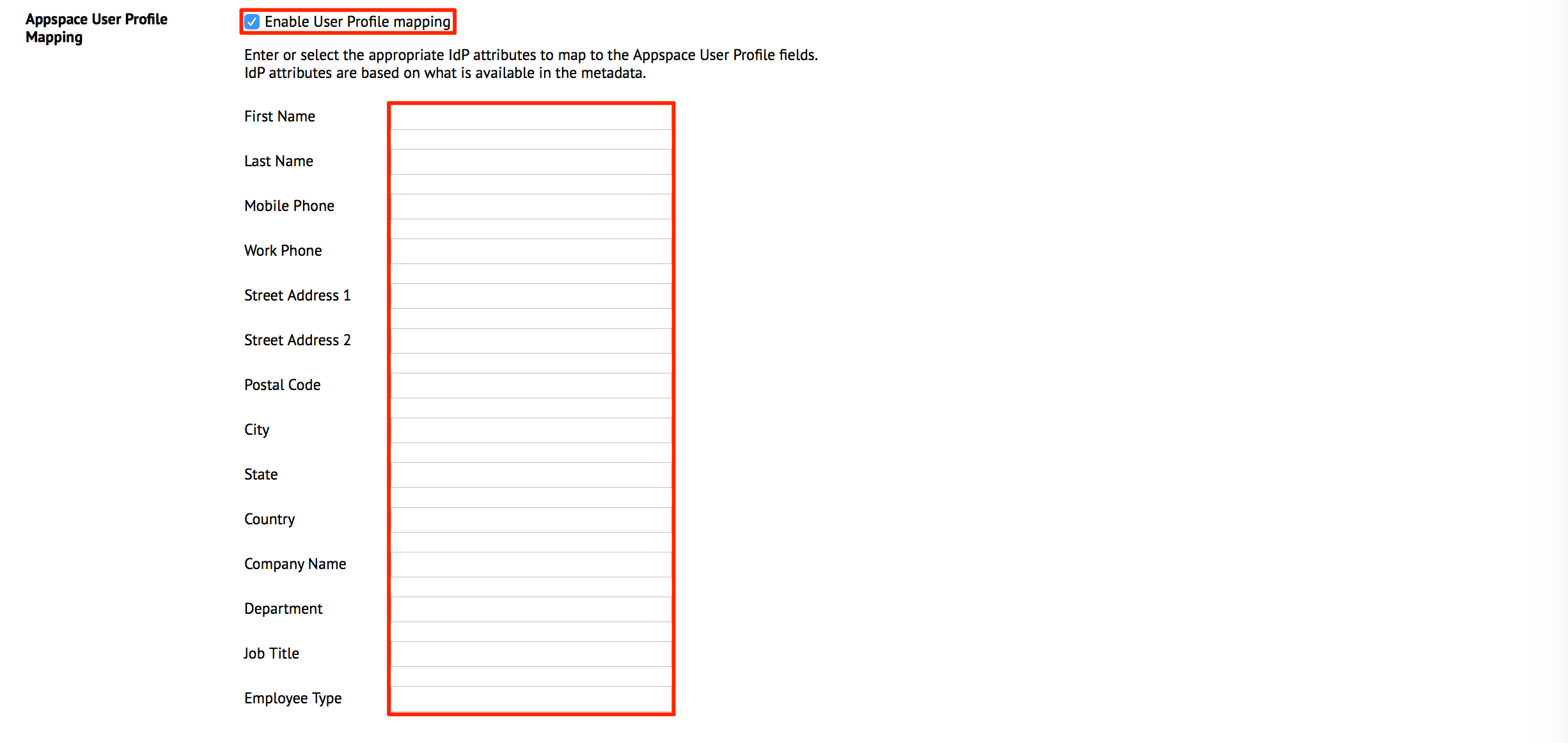
In the Appspace User Profile Mapping section, check the ‘Enable User Profile mapping’ checkbox to map the Appspace user fields to the corresponding fields existing in the Identity Provider. This is to ensure the user details on both providers match.
Note
If the IdP Metadata uploaded initially contained fields to be mapped, a drop-down menu of the fields available is displayed. A maximum of only 20 characters are allowed in each field.
In the Generate SP Metadata section, select Redirect or Post from the drop-down menu for Data Binding (IdP to SP). Check the Enable checkbox to enable Metadata Signing, or leave it unchecked depending on requirements.
- Redirect – Users will be redirected to the Identity Provider. SSO details will be passed in a query string with “?SAMLRequest=……” as part of the URL.
- Post – SSO details will not be passed through a query string but will be passed using the POST method. For this method to work, you must ensure that the Identity Provider has direct access to the Appspace Server.
- Metadata Signing - When enabled, the metadata file is generated in an encrypted format.
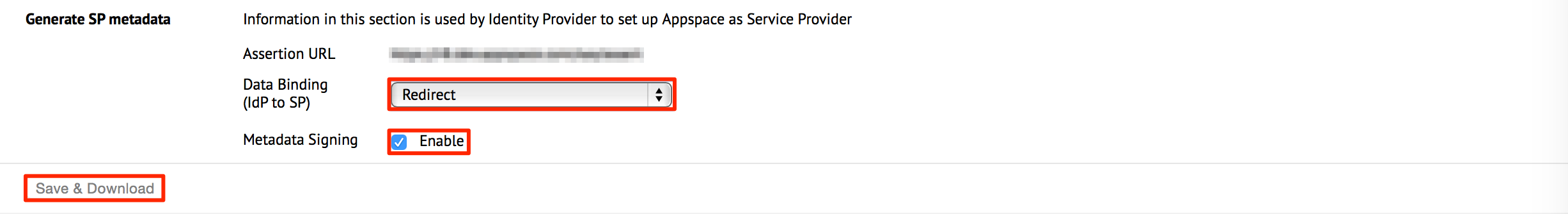
Click Save & Download to download the Service Provider XML file, that can be used to configure the Identity Provider.
Section 3: Configuring ADFS Relying Party Trust
Note
This section is performed on the Identity Provider (AD FS) server.
On the ADFS server, launch the AD FS 2.0 Management application.
In the AD FS 2.0 folder tree, expand the Trust Relationship folder and select the Relying Party Trusts folder. In the Actions pane, click the Add Relying Party Trust link to launch the wizard.
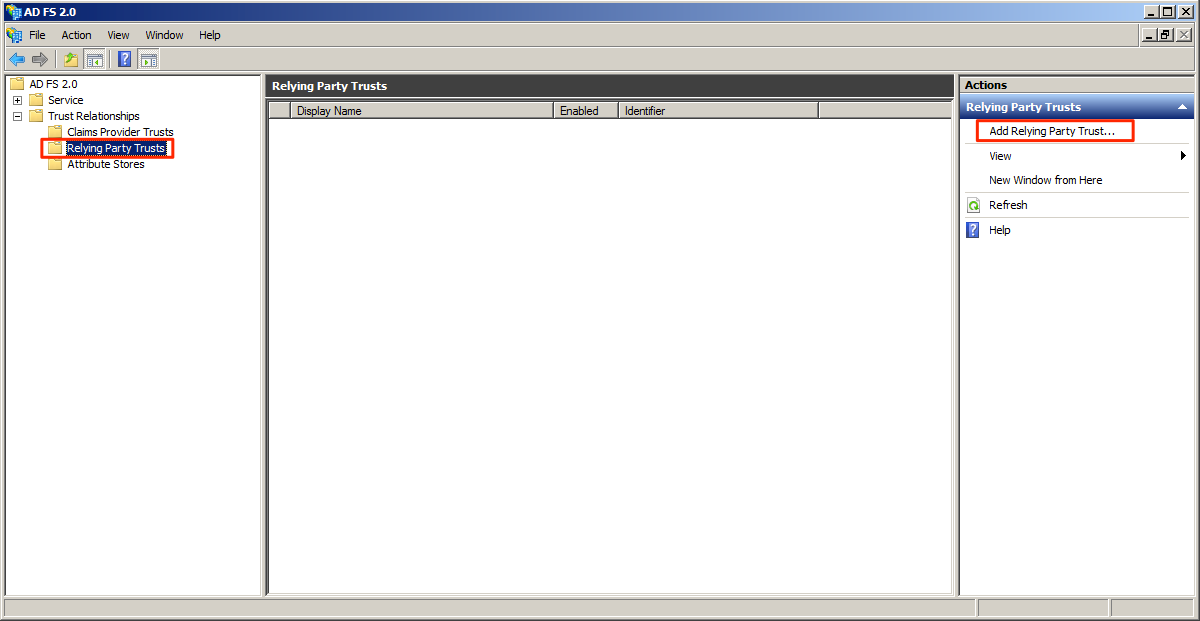
In the Add Relying Party Trust Wizard, Click Start.
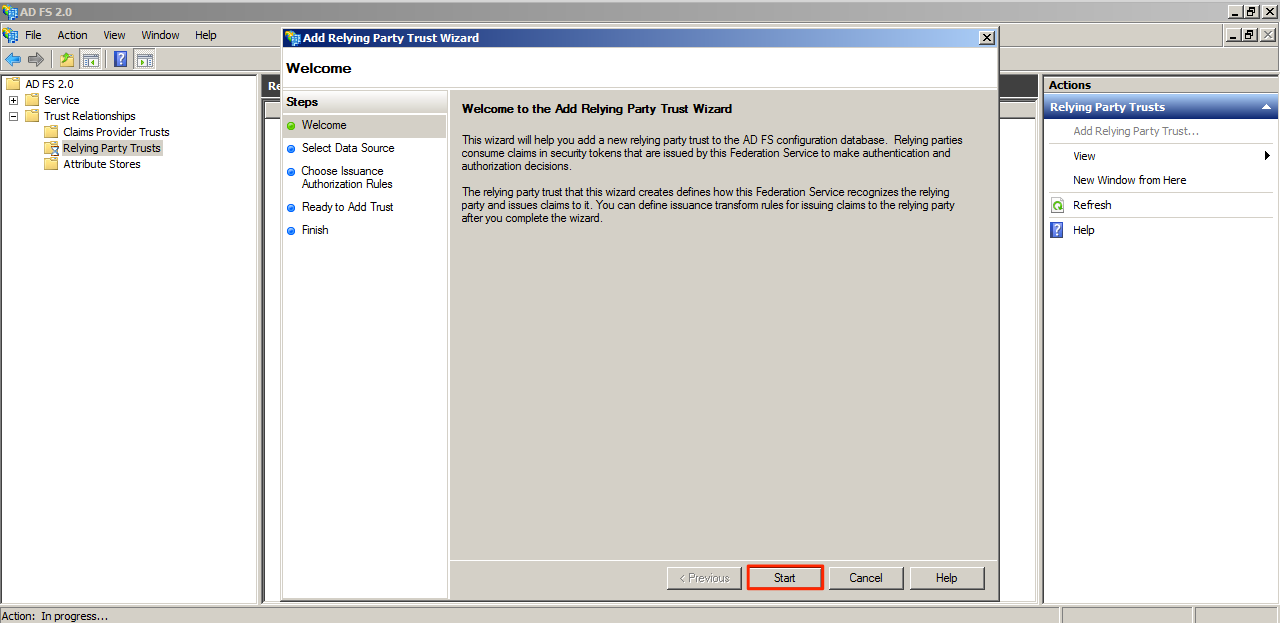
Select the “Import data about the relying party from a file” option, and click Browse.
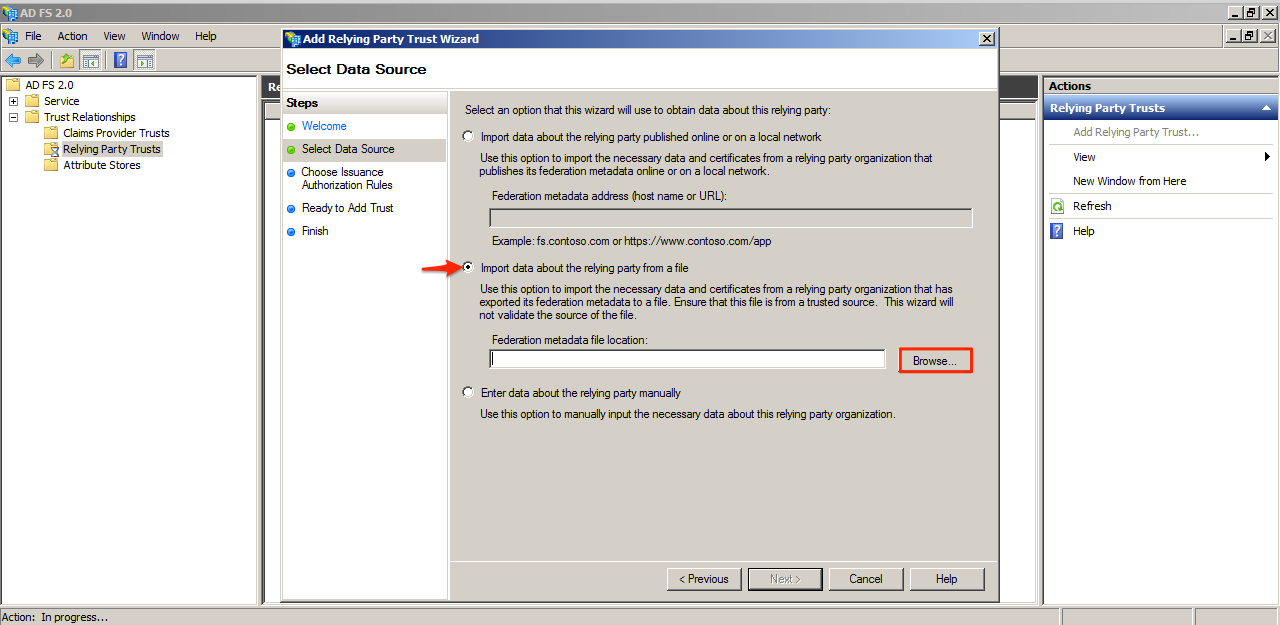
Locate and select the metadata file that was downloaded from Appspace, and click Next.
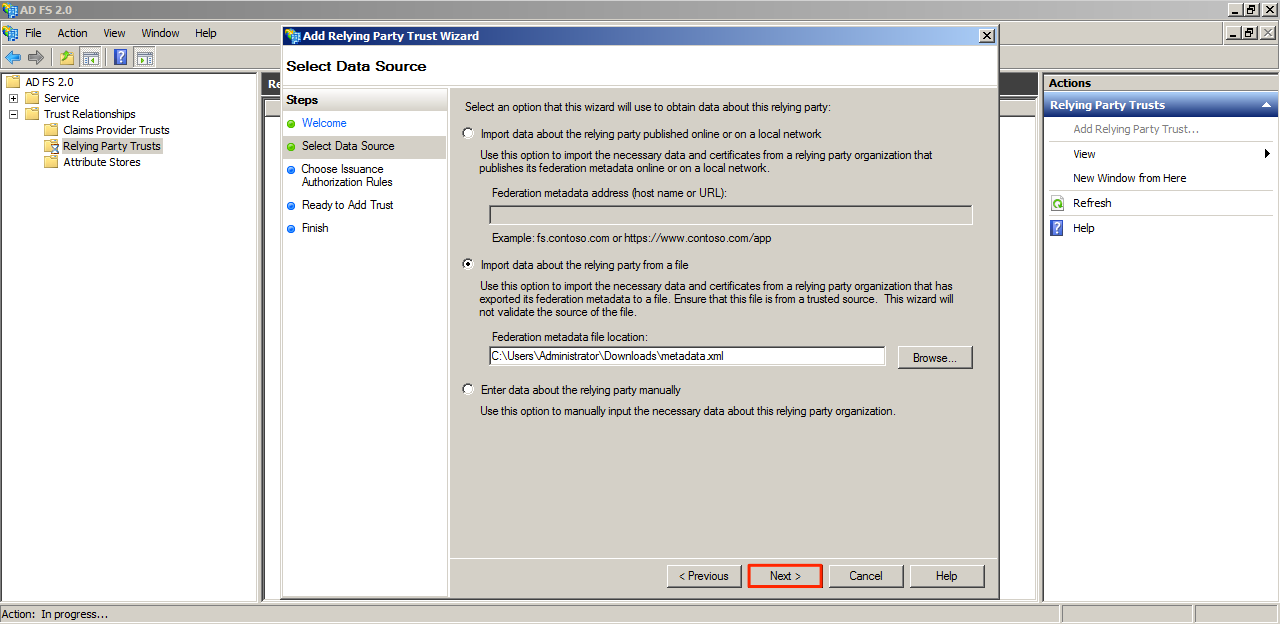
Give the Relying Party trust a name and click Next.
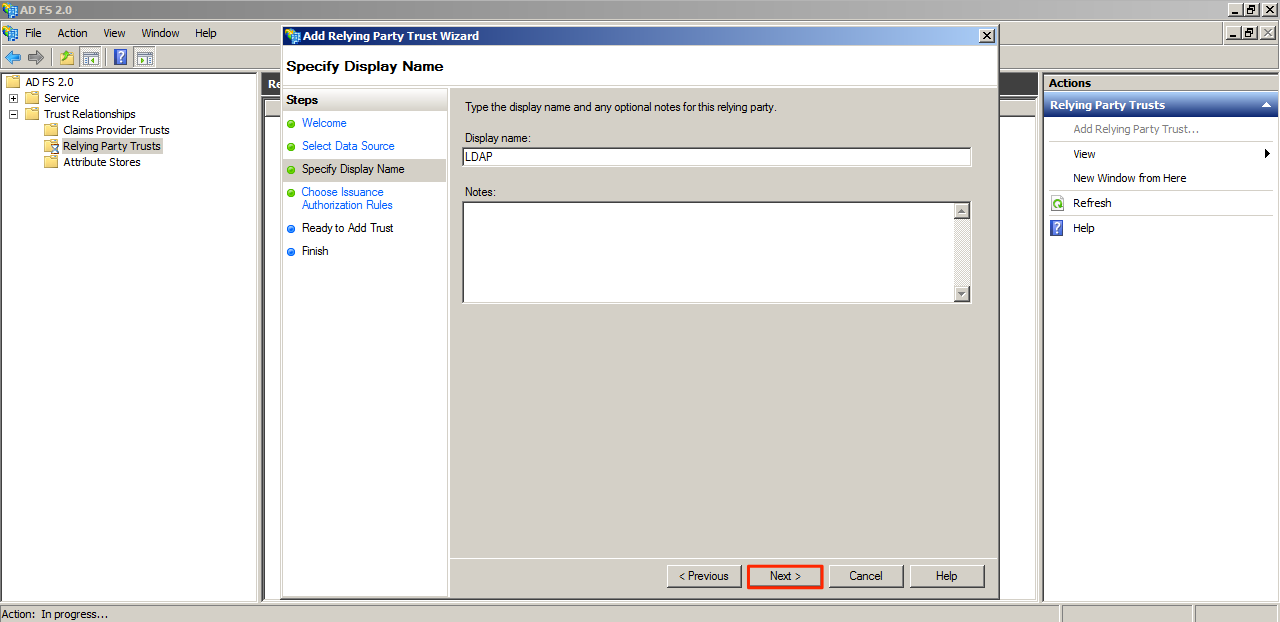
Select the “Permit all users to access this relying party” option, and click Next.
Click Next.
Check the “Open the Edit Claim Rules dialog for this relying party trust when the wizard closes” checkbox, and click Close.
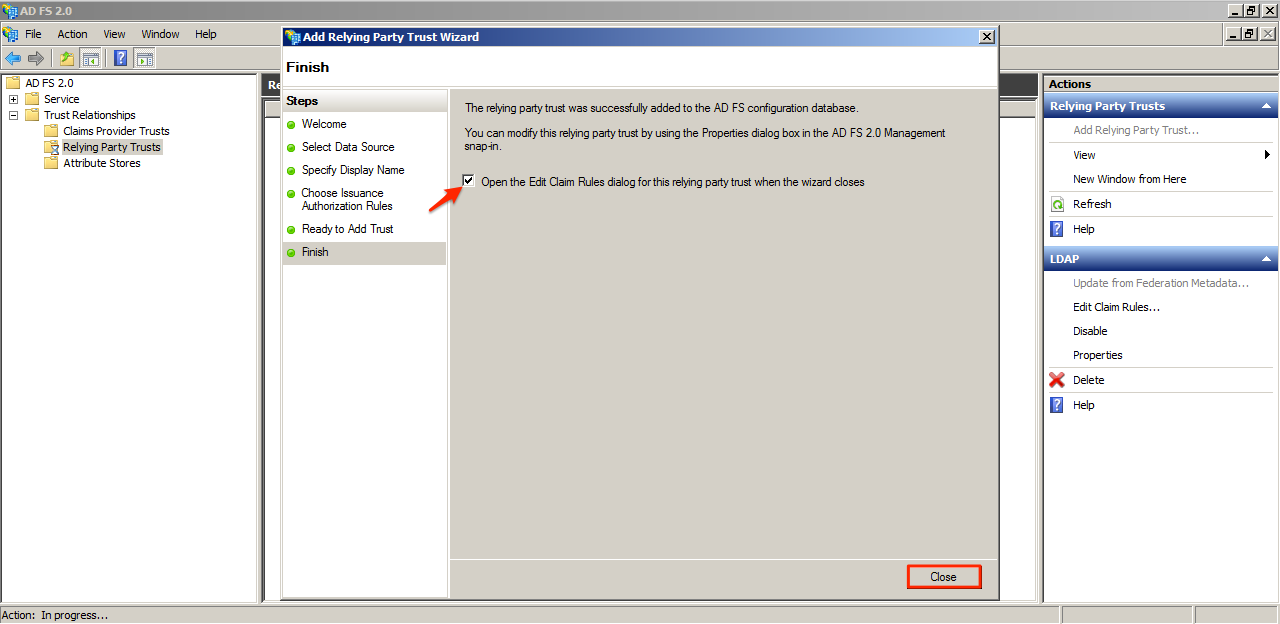
On the Edit Claim Rule window, click Add Rule.
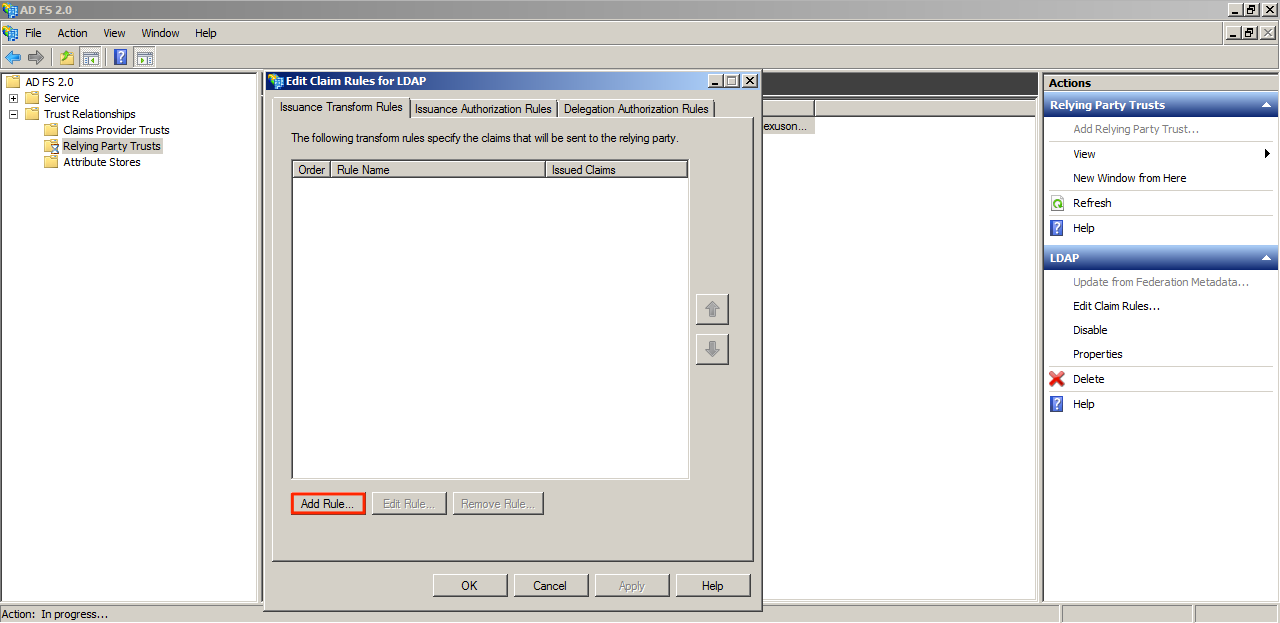
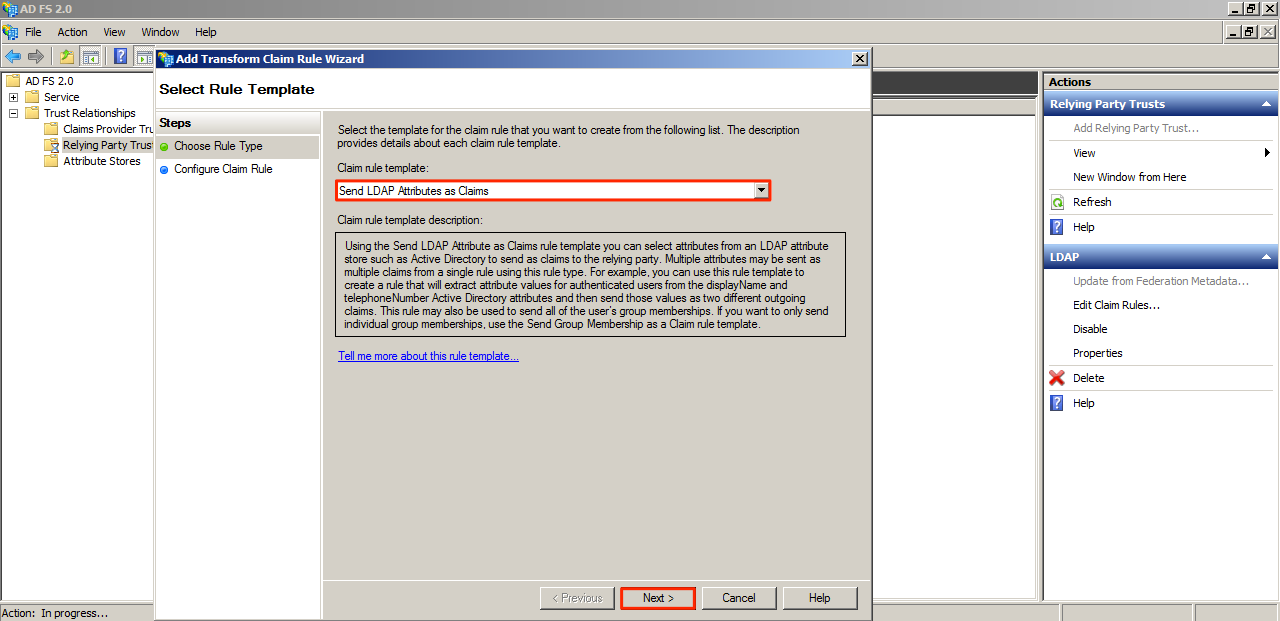
Select “Send LDAP Attributes as Claims” from the dropdown menu, and click Next.
Name the Claim Rule template, and select Active Directory as the Attribute store. Map the LDAP attributes to outgoing claims by referring to the image below. Click Finish once down.
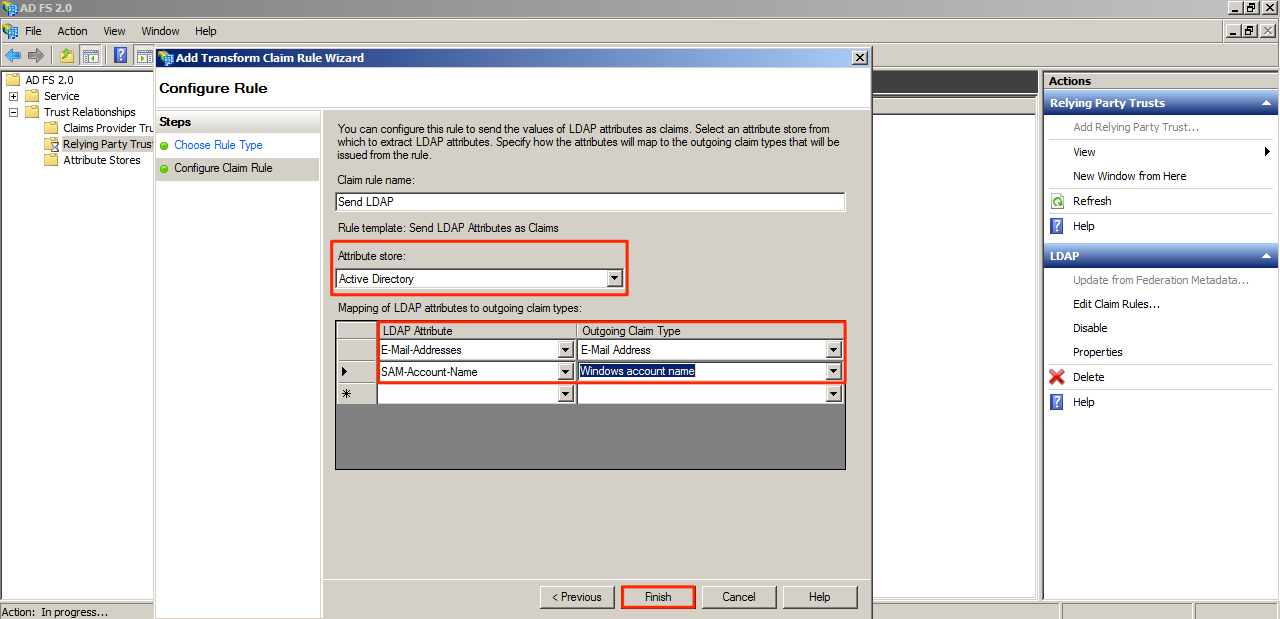
Note
This step mandates that all Appspace users (authenticating via SSO) are required to have email addresses (can be used as the usernames as well).
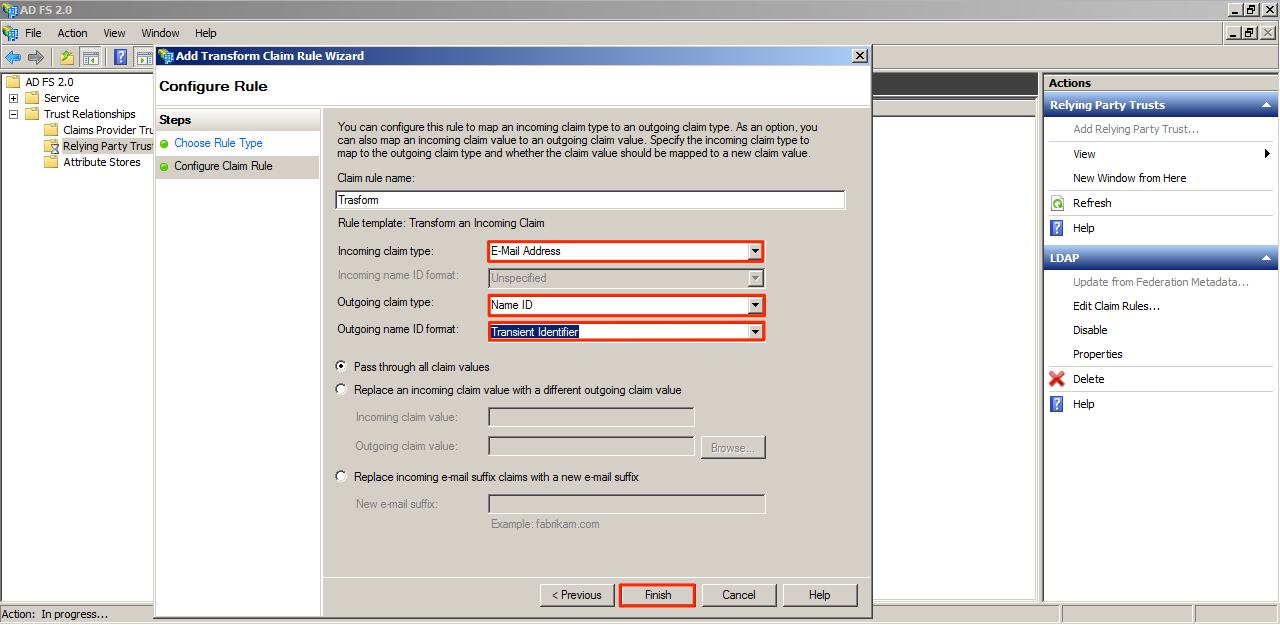
Click Add Rule, and select “Transform an Incoming Claim”. Click Next.
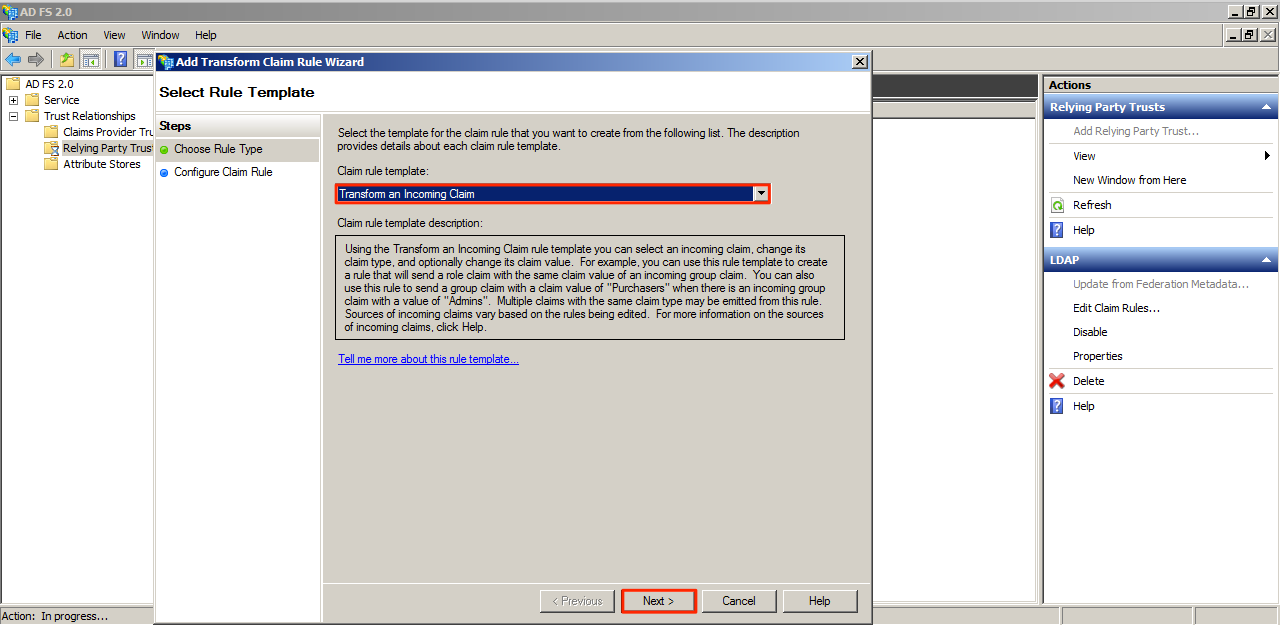
Name the Claim rule and configure the rest of the fields as shown in the image below. Click Finish when done.
Click Apply.
Click OK.
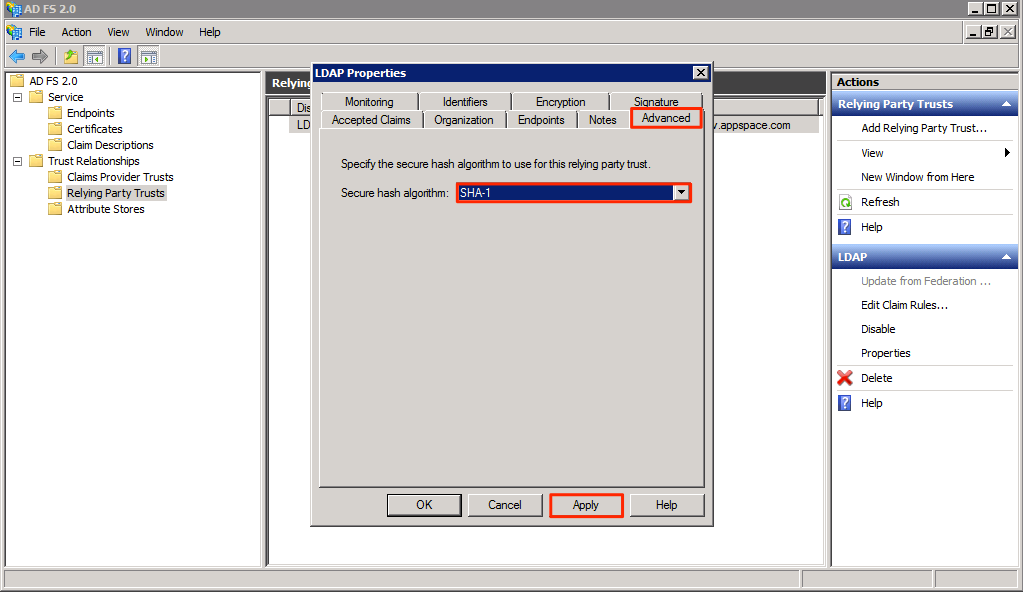
In the AD FS 2.0 folder tree, click the Relying Party Trusts folder, and select your display name.
Click Advanced and select SHA-1 as the secure hash algorithm. Click Apply when done.