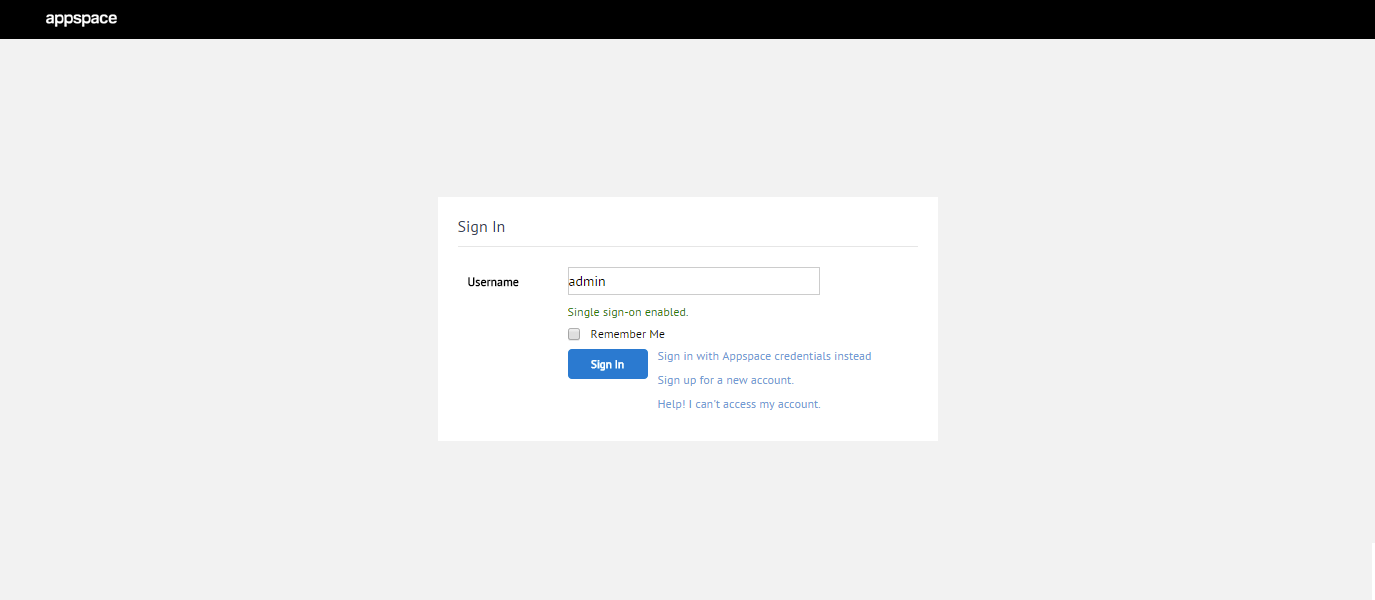
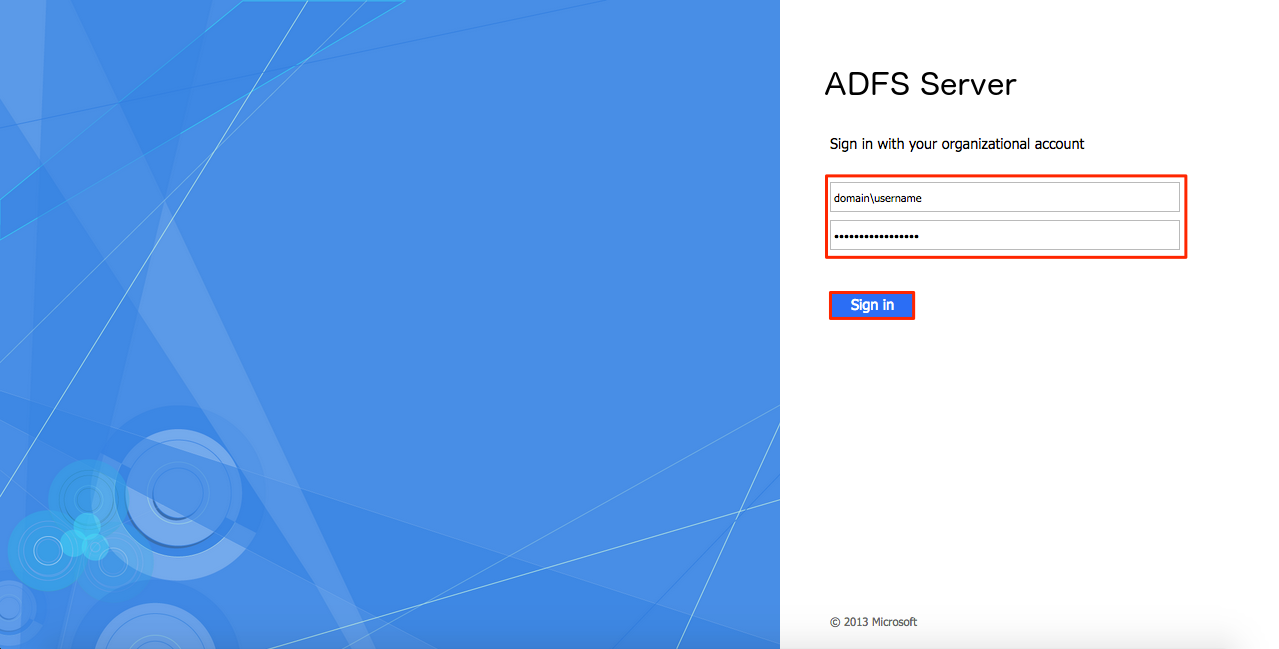
Single Sign On (SSO) for Single-Tenant Deployments
Introduction
Appspace 5.2 introduces our single sign on (SSO) integration feature for on-premise deployments. With SSO, Appspace allows users to seamlessly and securely connect to Appspace using a single set of credentials, simplifying username and password management.
This guide is based on ADFS being the Identity Provider and Appspace being the Service Provider. As this will be a complicated configuration/installation guide, we’ll break it down into smaller sections:
Section 4: Enabling and Configuring SSO
Section 1: Requirements
Active Directory Server
- Windows Server 2008 R2
- SSL configured
- Windows Server Administrator credentials
Active Directory Federation Services (ADFS)
- Can be installed on the Active Directory Server
- Version 2.0 for Windows Server 2008 R2
- SSL configured
- Windows Server Administrator credentials
Network
- All servers must belong to the same domain or sub domain
Appspace Server
- Version 5.2
- SSL configured
- Windows Server Administrator credentials
- Appspace Portal Administrator, Account Administrator or Account Owner role
- All users created on the Appspace server needs to have an email (can be used as the login as well)
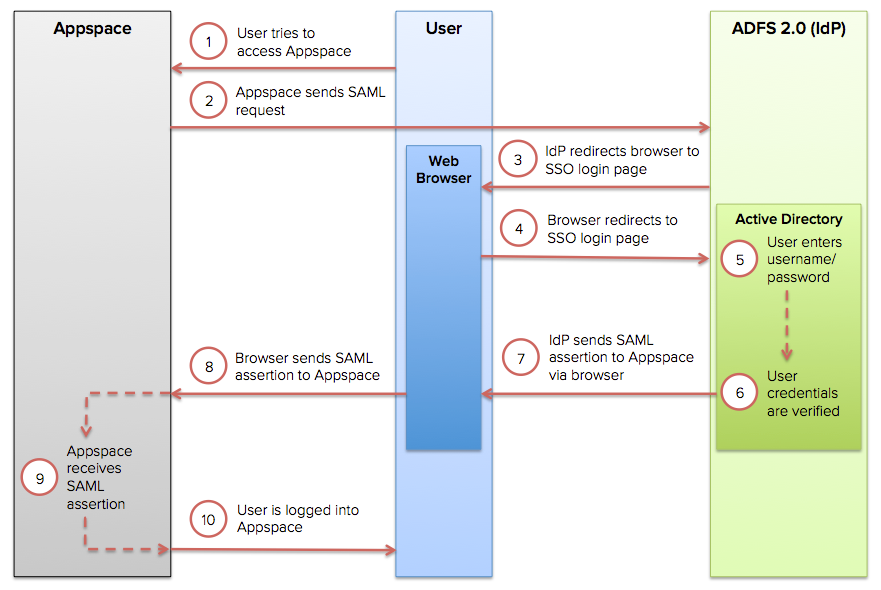
Section 2: How SSO Works
A user starts by trying to log into Appspace. Upon accessing the login page, the user will be redirected to an SSO login page. The user will then have to authenticate his/her login credentials against the Identity Provider. Upon successful authentication, the Identity Provider will send a SAML assertion to Appspace via the web browser to allow the user to log into Appspace.
Section 3: Installing ADFS
Note
This can be performed on the AD server or on a separate server.
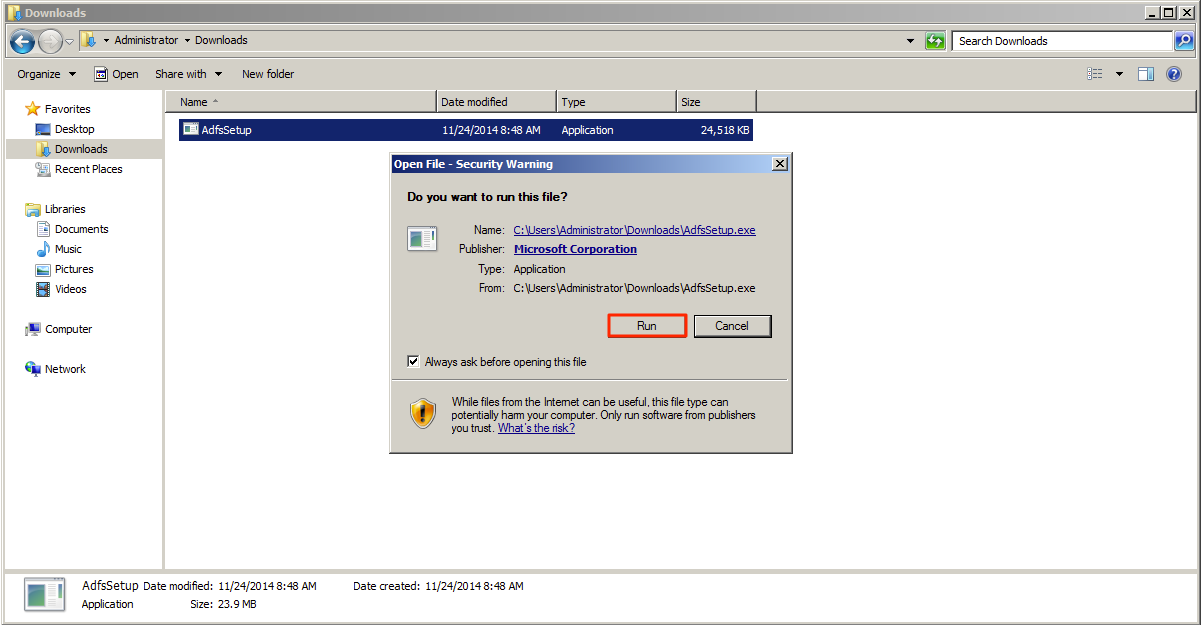
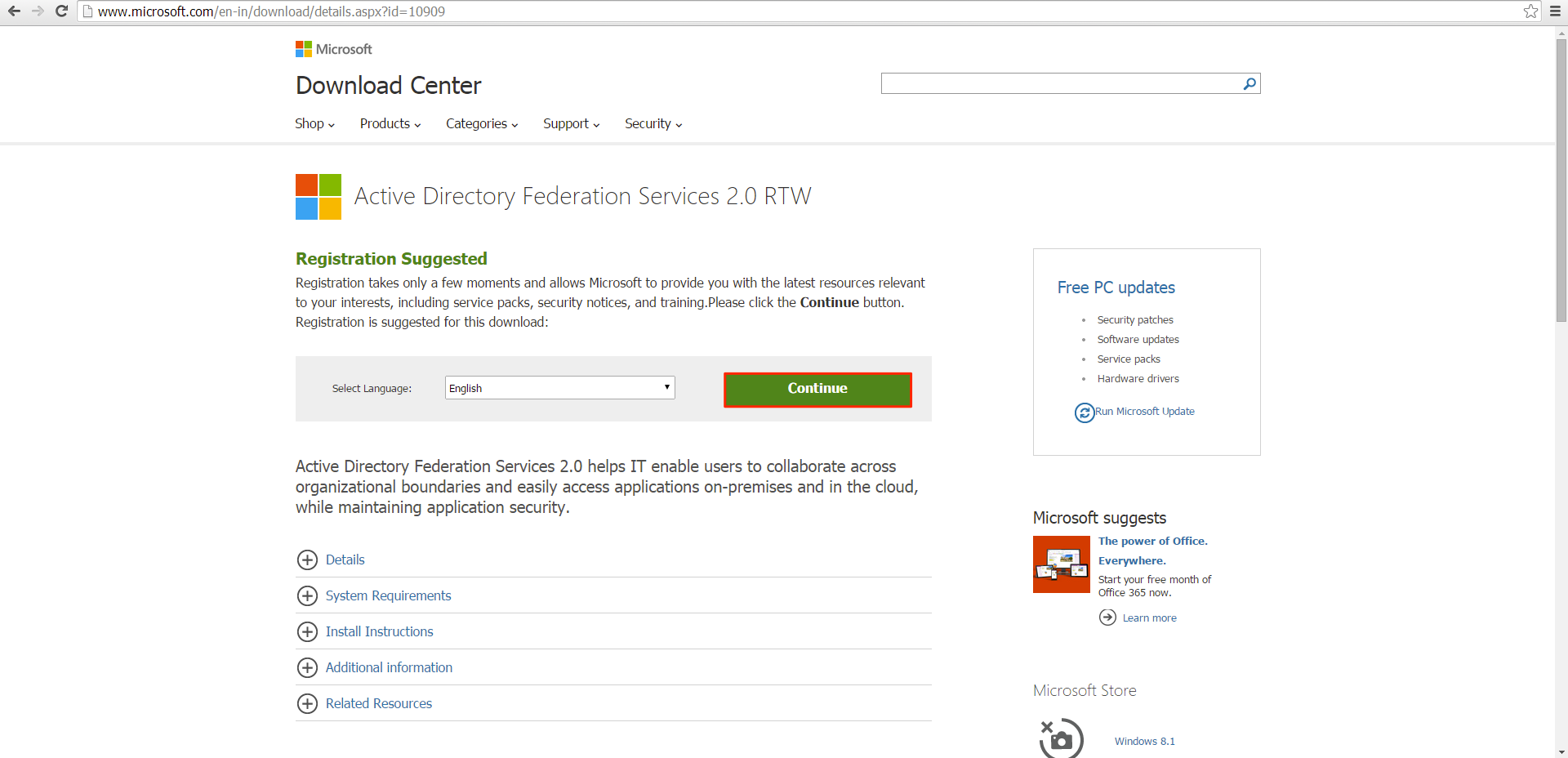
Step 1
Start by downloading Active Directory Federation Services 2.0. To do so, navigate to http://www.microsoft.com/en-in/download/details.aspx?id=10909 and click Continue.
Step 2
Choose the version based on your Windows Server version and click Next to start the download.
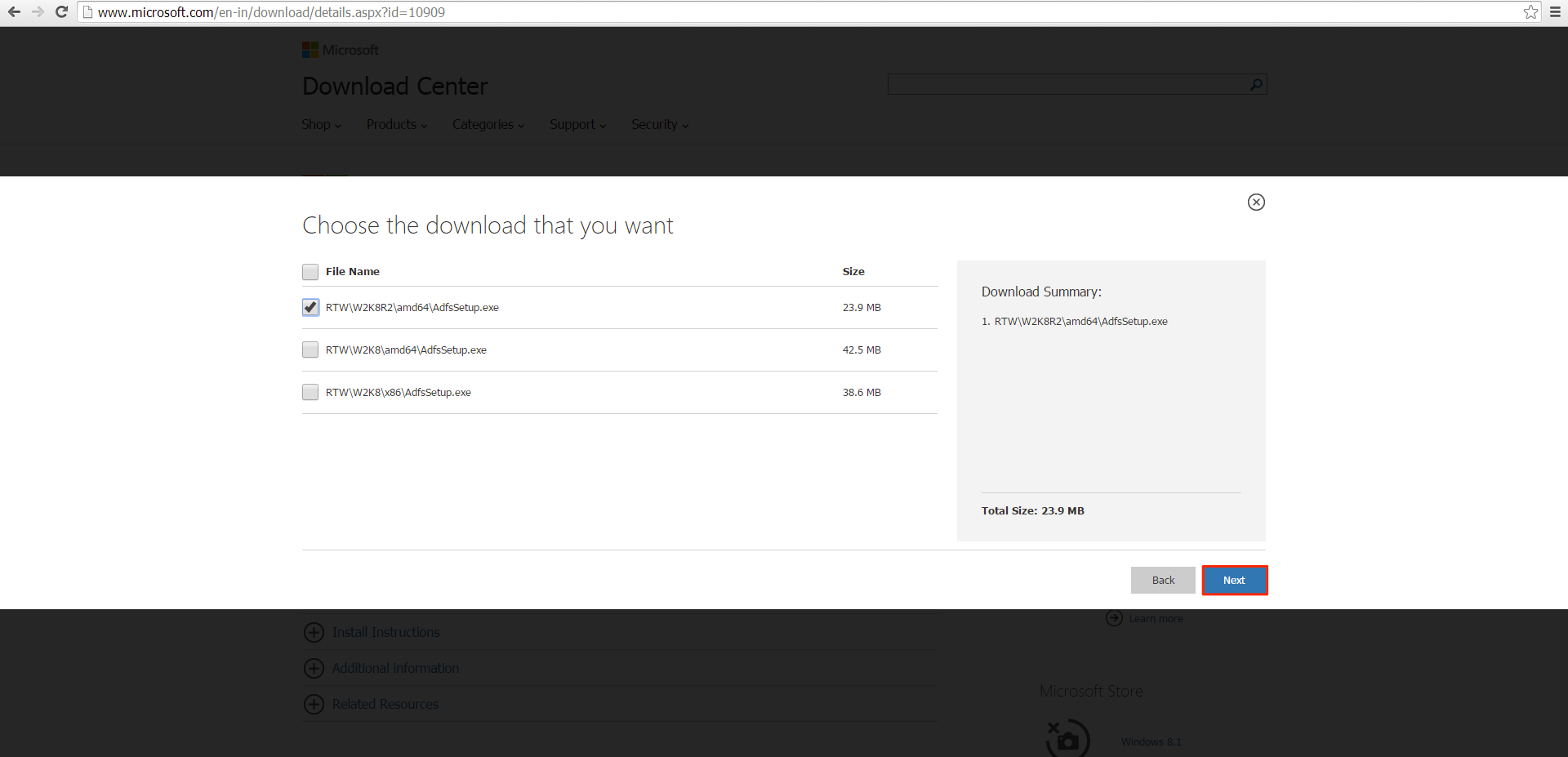
Note
RTW/W2K8R2/amd64/AdfsSetup.exe – This is for Windows Server 2008 R2 SP1
RTW/W2K8/amd64/AdfsSetup.exe – This is for Windows Server 2008 R1 SP2 64bit
RTW/W2K8/x86/AdfsSetup.exe – This is for Windows Server R1 SP2 32bit
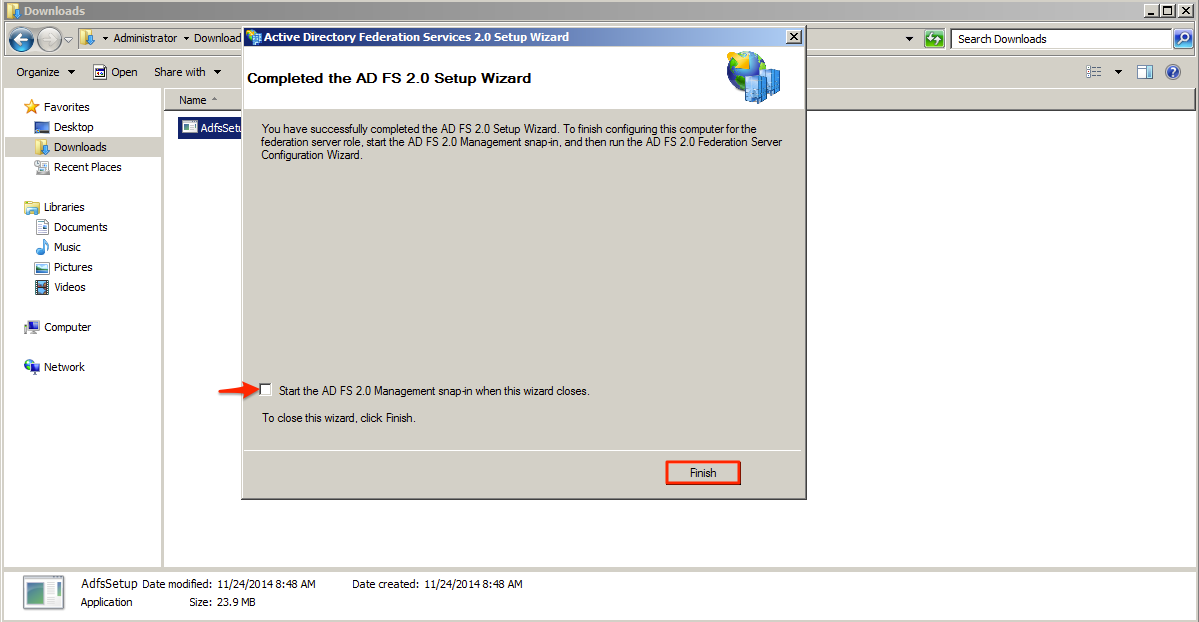
Step 9
Select the option to start the ADFS 2.0 Management snap-in when this wizard closes and click Finish.
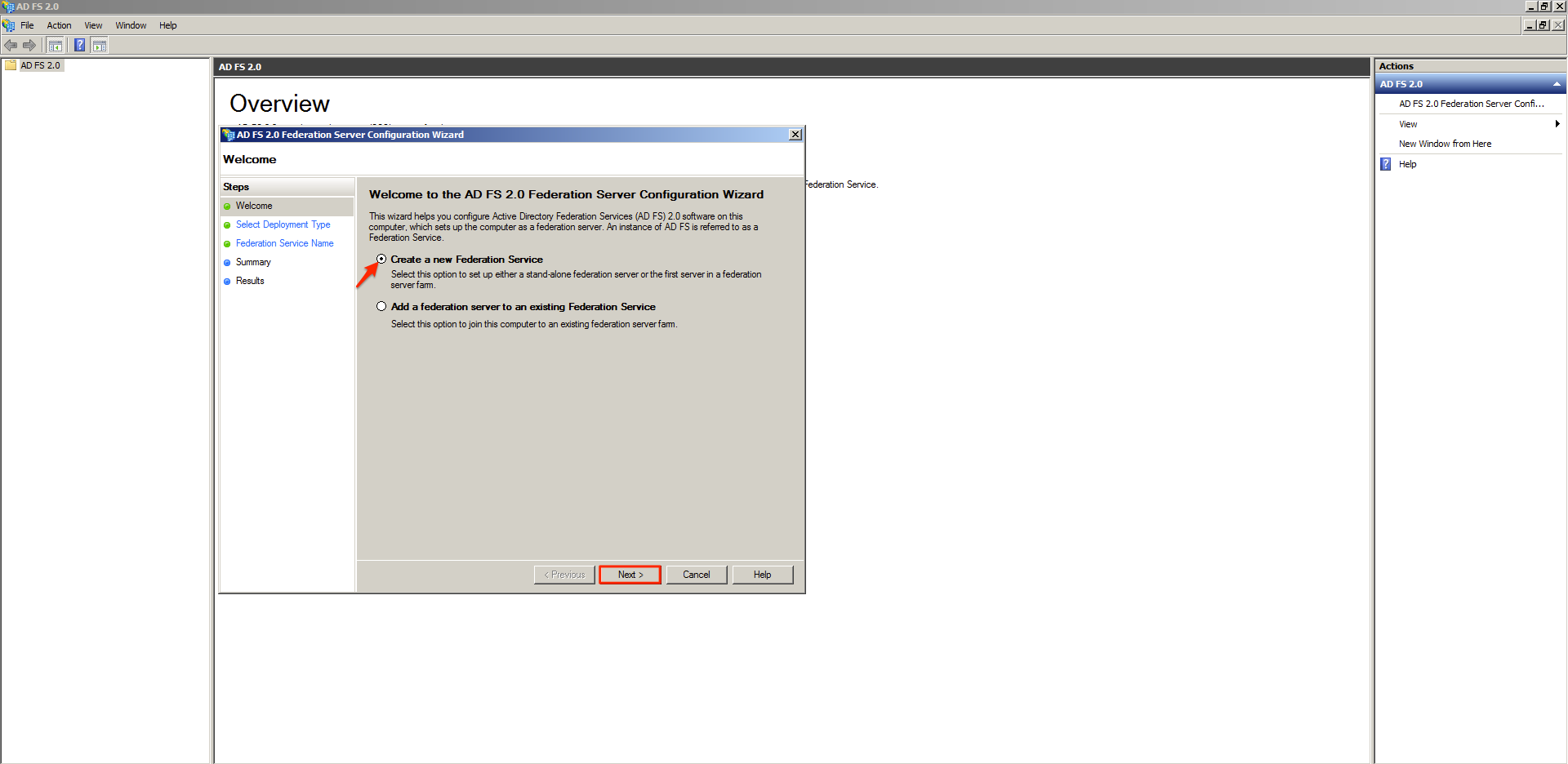
Step 10
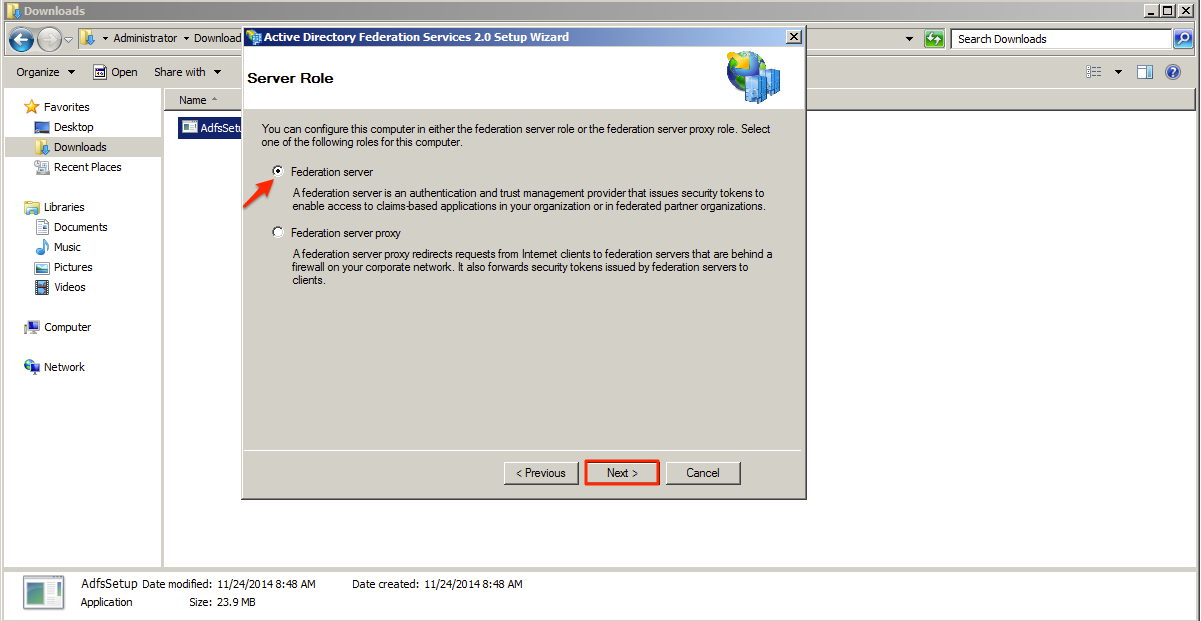
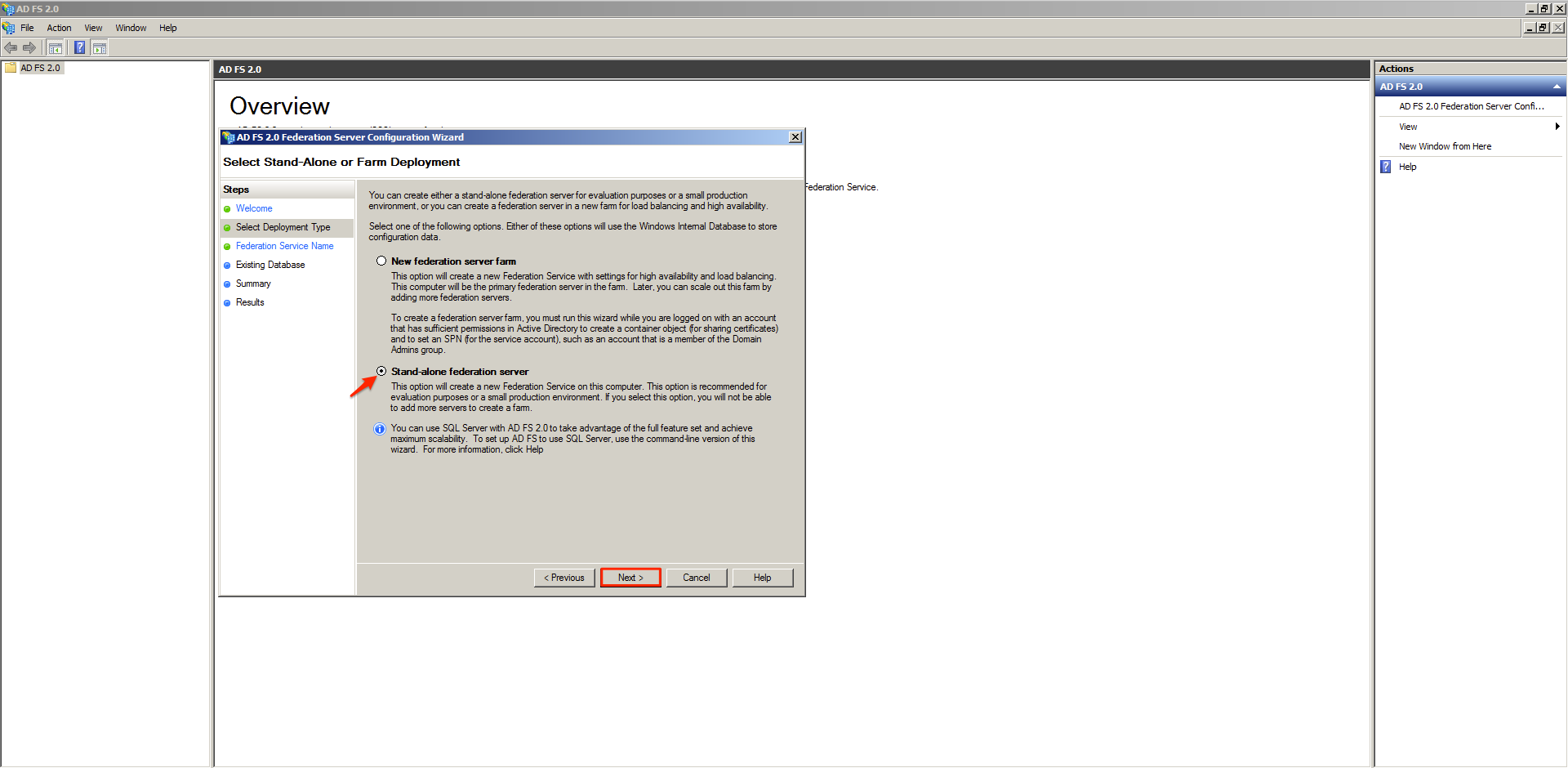
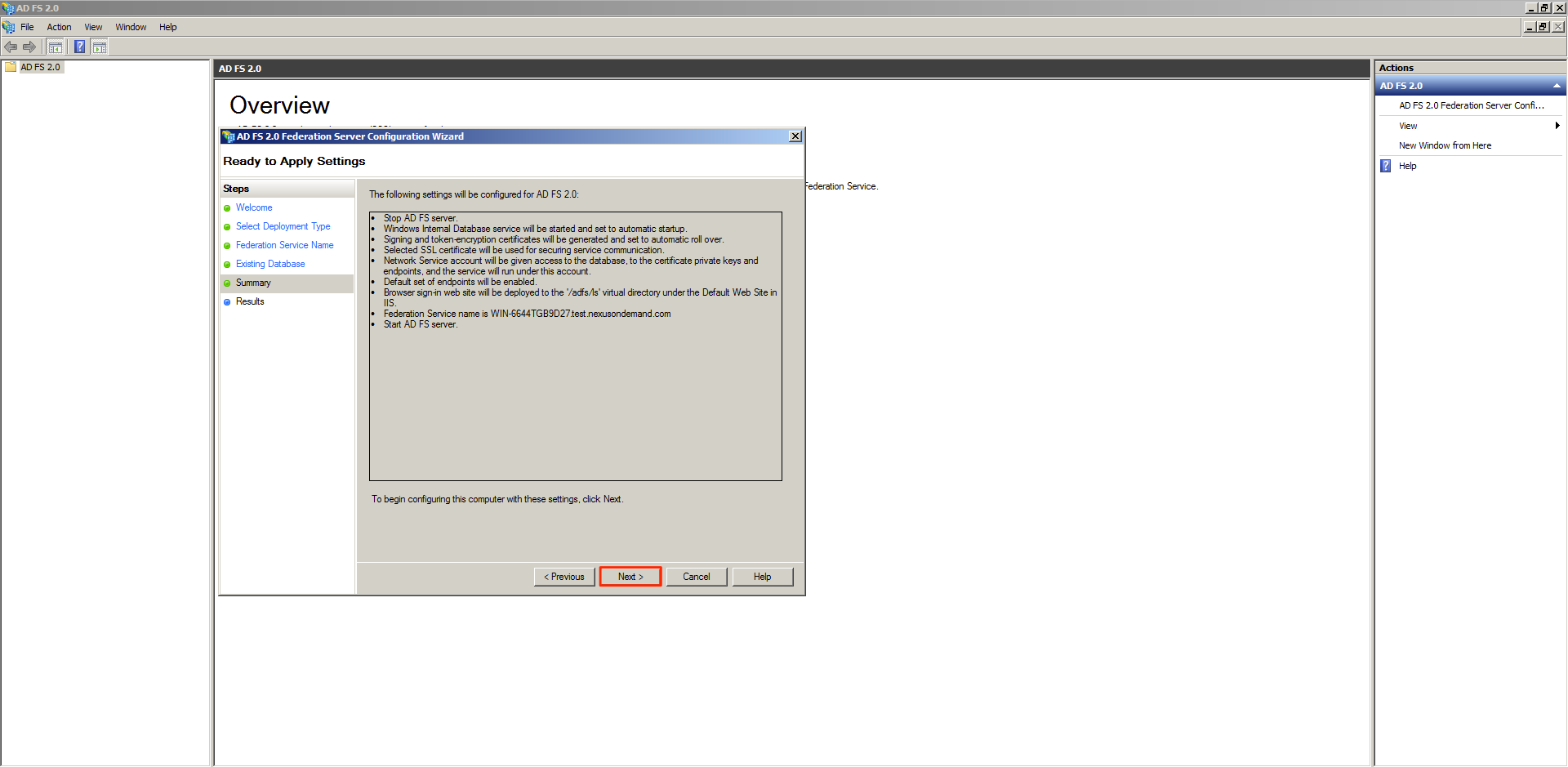
On the AD FS Server configuration wizard select the Create a new Federation Service option and click Next.
Section 4: Enabling and Configuring SSO
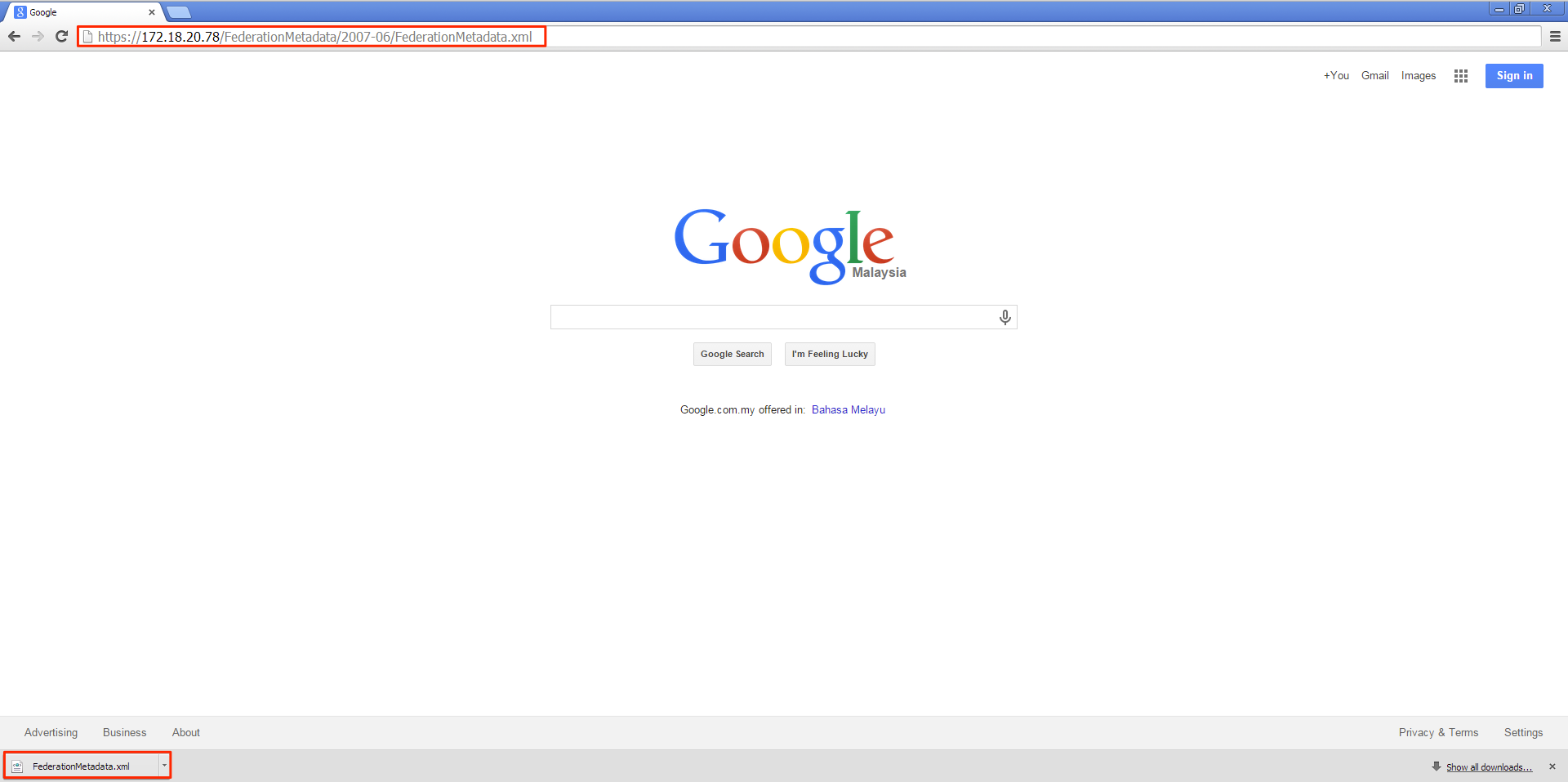
Step 1
To begin, we will need to download the Identity Provider (ADFS) metadata. Open a browser and key in the URL https://<ADFS FQDN or IP>/FederationMetadata/2007-06/FederationMetadata.xml to download the metadata.
Note
This metadata is used by the Identity Provider (ADFS) to recognise the Service Provider (Appspace). This process involves downloading the metadata in xml format, uploading to and re-downloading from Appspace and finally re-uploading it to the Identity Provider (ADFS).
Step 2
Log into your Appspace instance and click on the user button followed by System.
Note
You’ll have to be a Portal Administrator to access system settings.
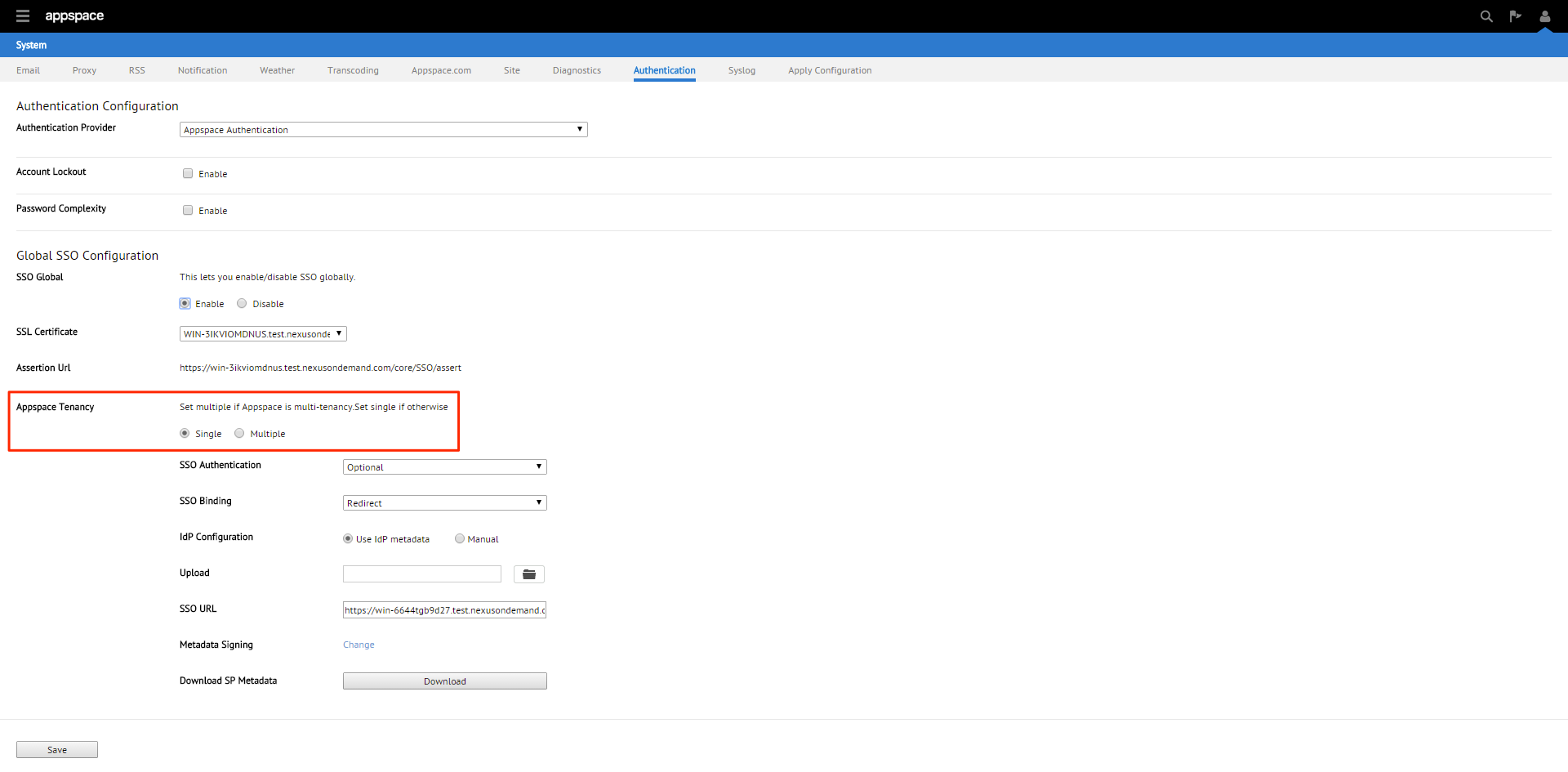
Step 5
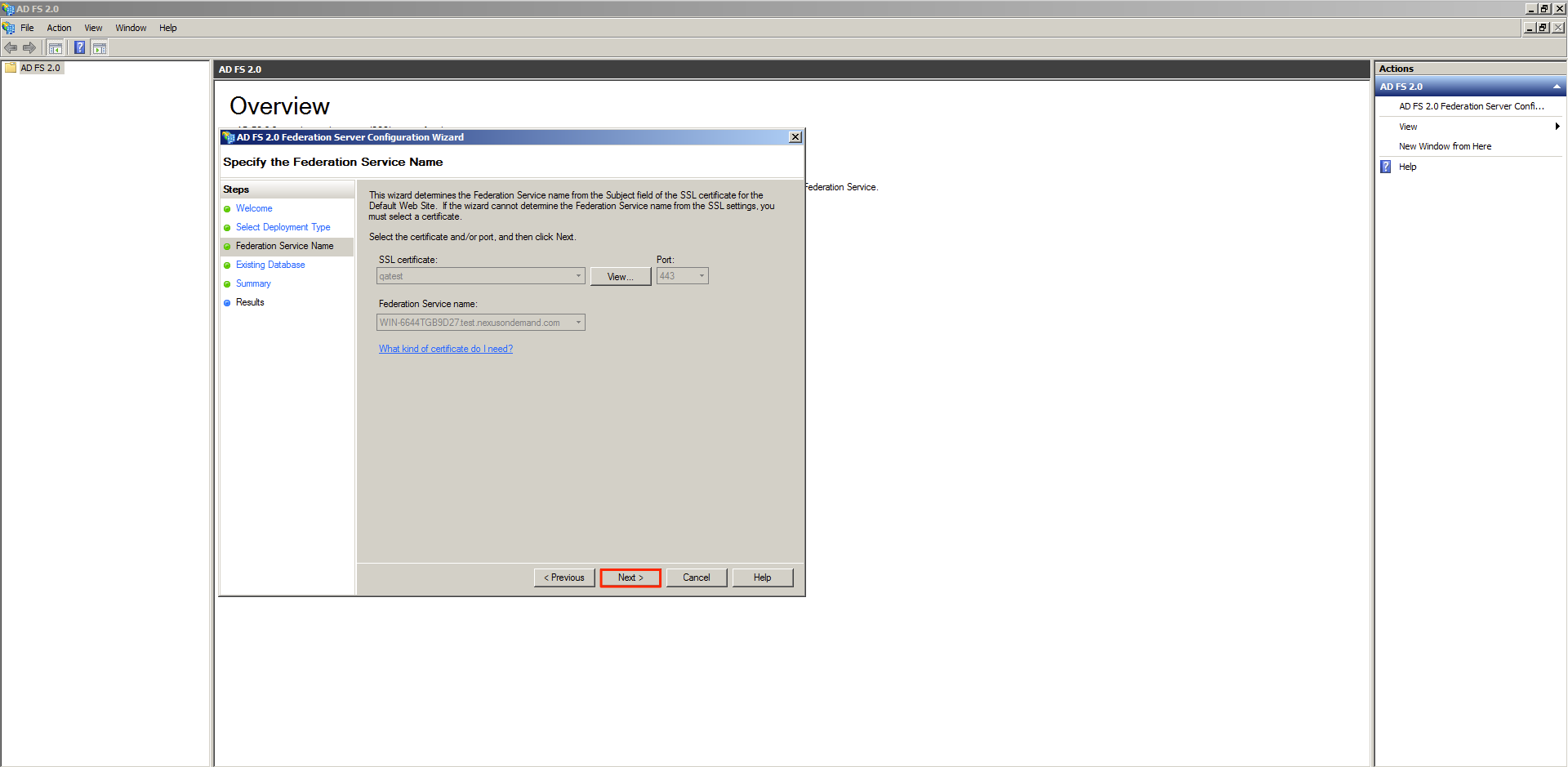
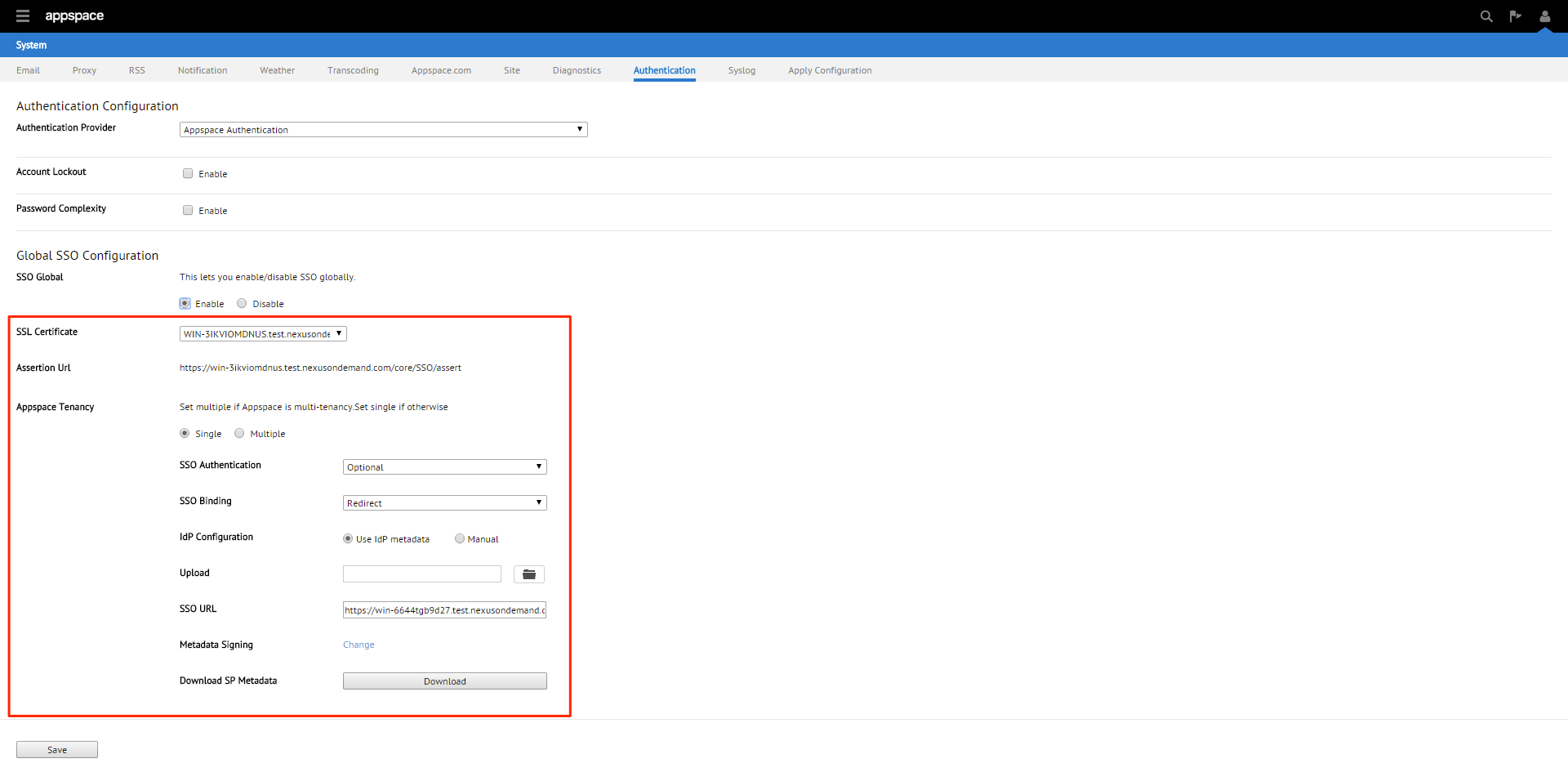
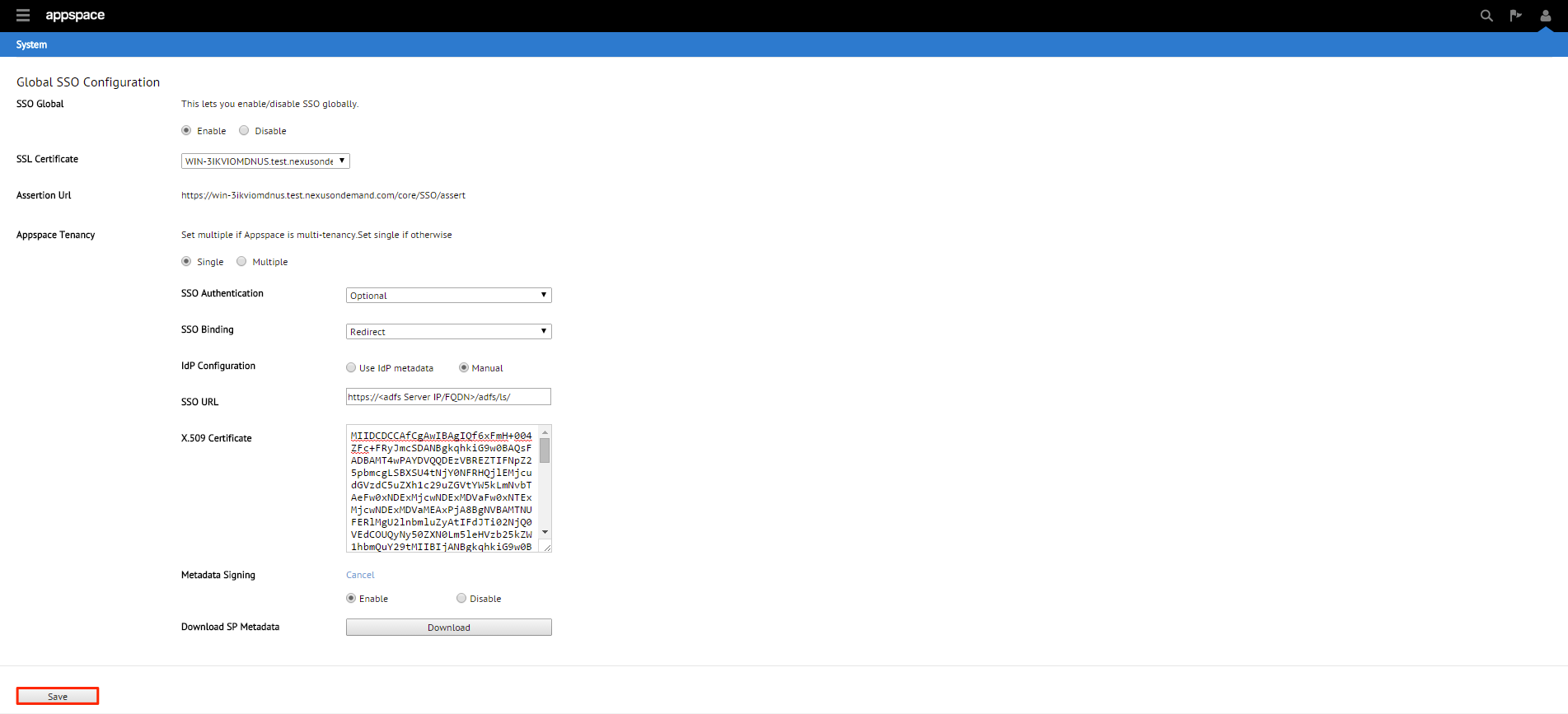
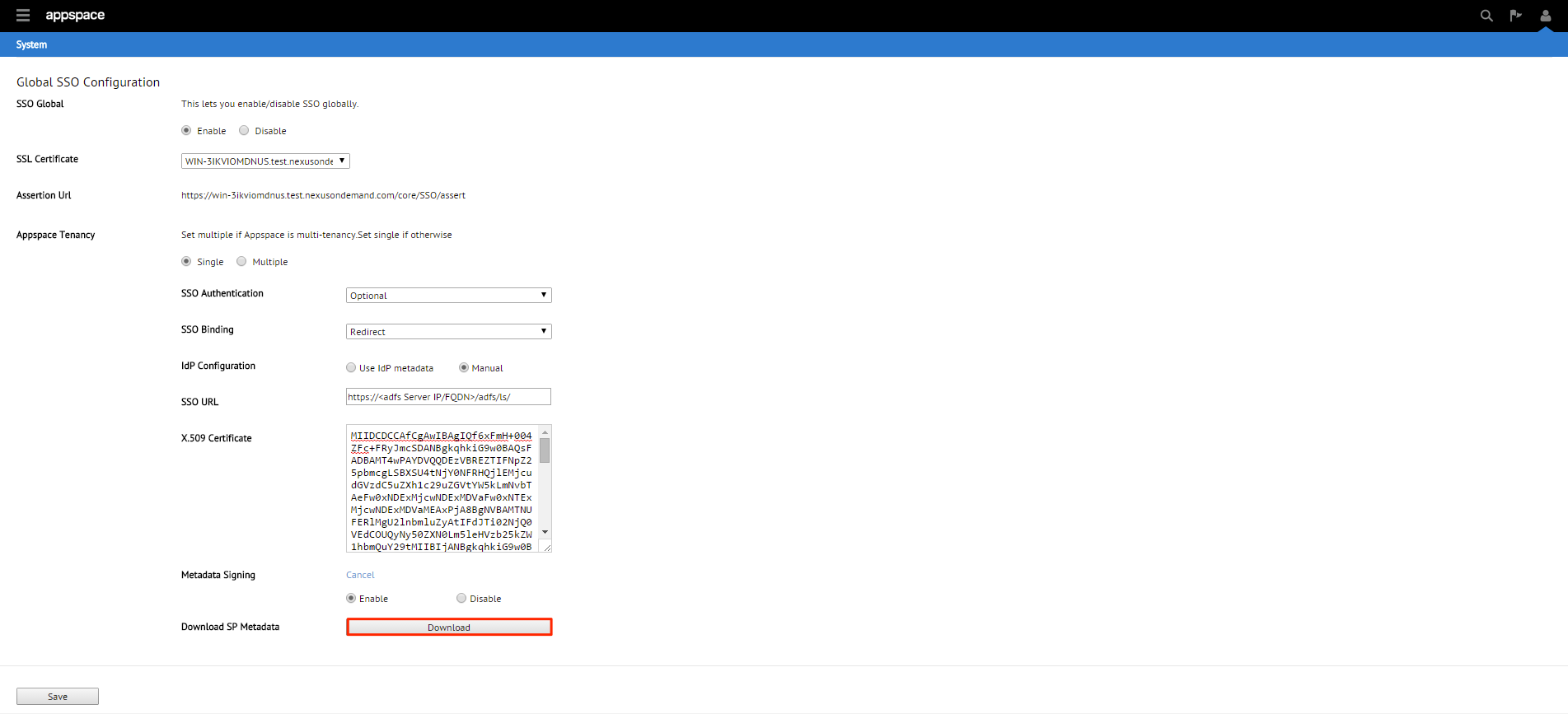
If the Appspace server has a valid SSL certificate installed , the SSL Certificate section will be populated automatically.

Step 7
You will be given three SSO authentication options: OFF, Optional or Required. We’ll be selecting Optional in this example.

Note
Optional – Users can select between using their Appspace login credentials or via SSO (AD credentials)
Required – Users can only login via SSO (AD credentials)
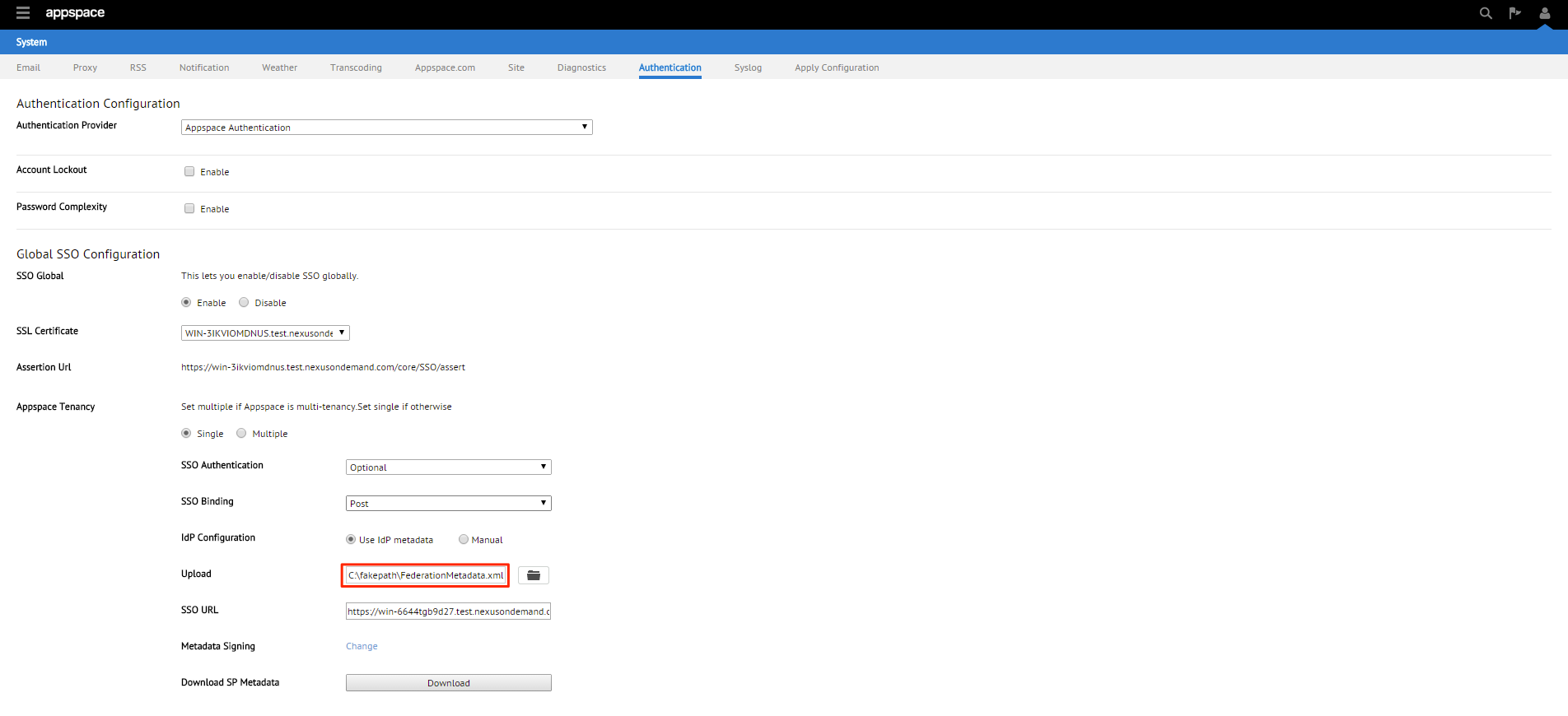
Step 8
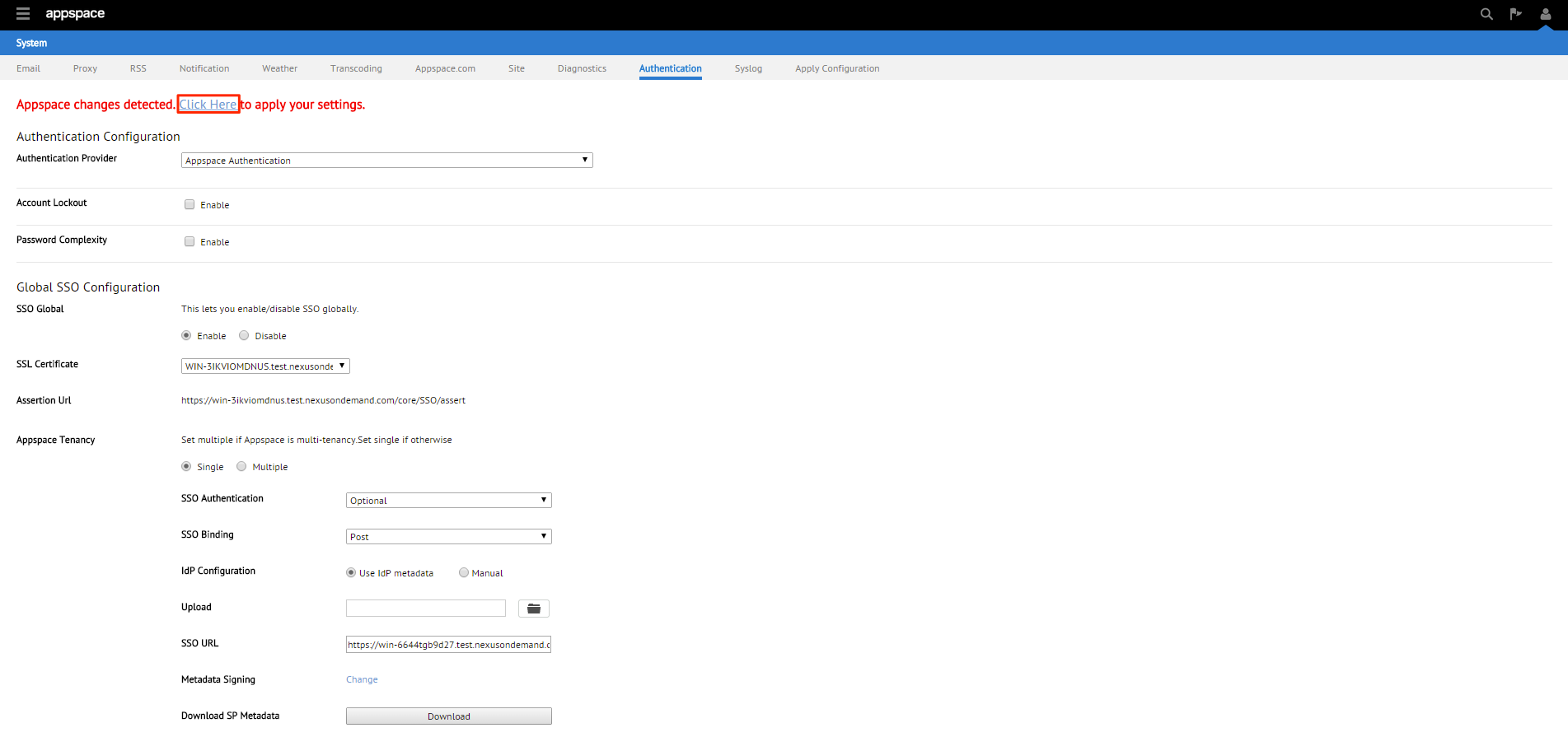
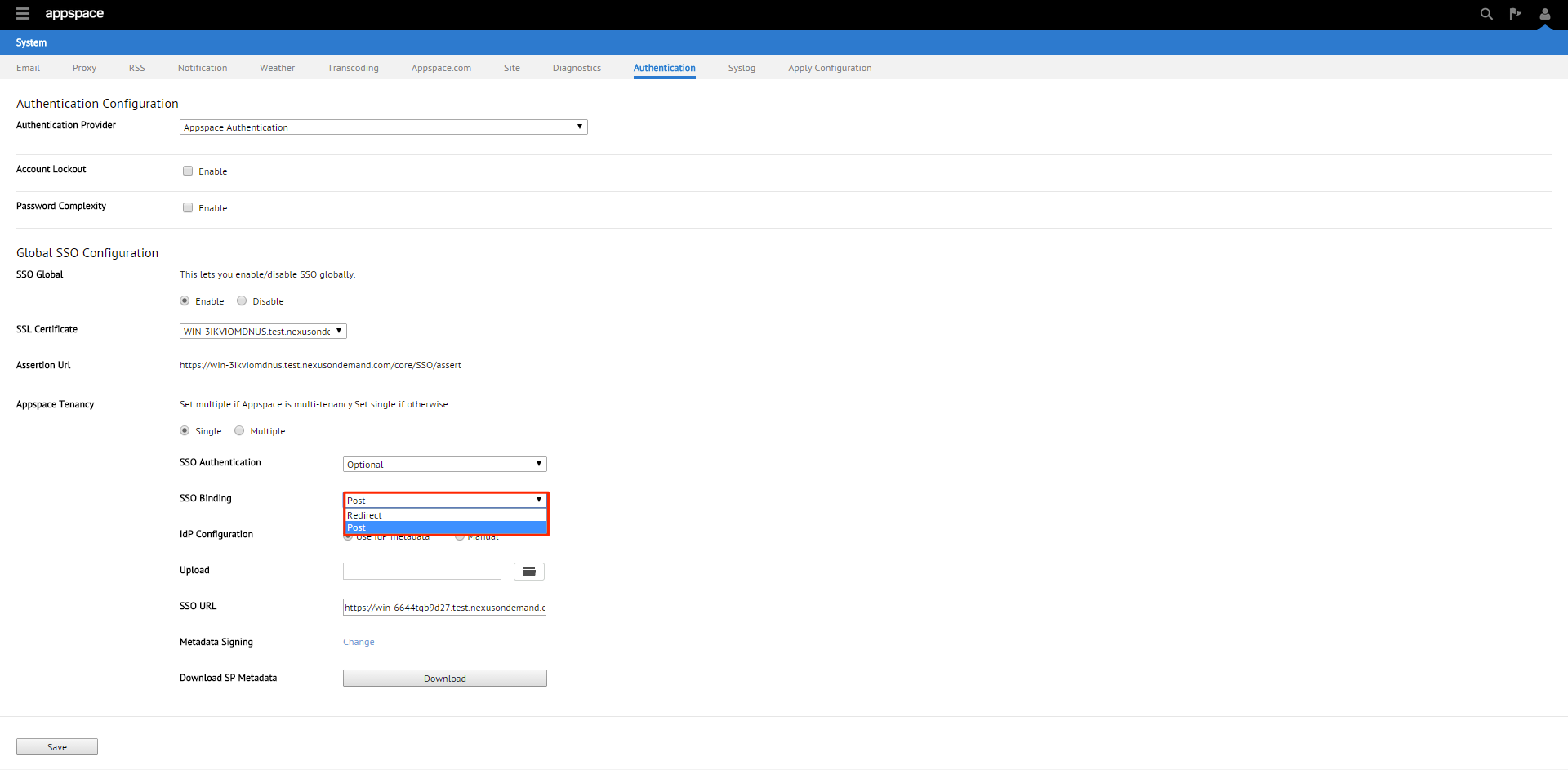
You will be given two SSO binding options; Redirect or POST. We’ll be using POST in this example.
Note
Redirect – Users will be redirected to the Identity Provider. SSO details will be passed in a query string with “?SAMLRequest=……” as part of the URL
Post – SSO details will not be passed through a query string but will be passed using the POST method. For this method to work, you must ensure that the Identity Provider has direct access to the Appspace Server.
Step 9
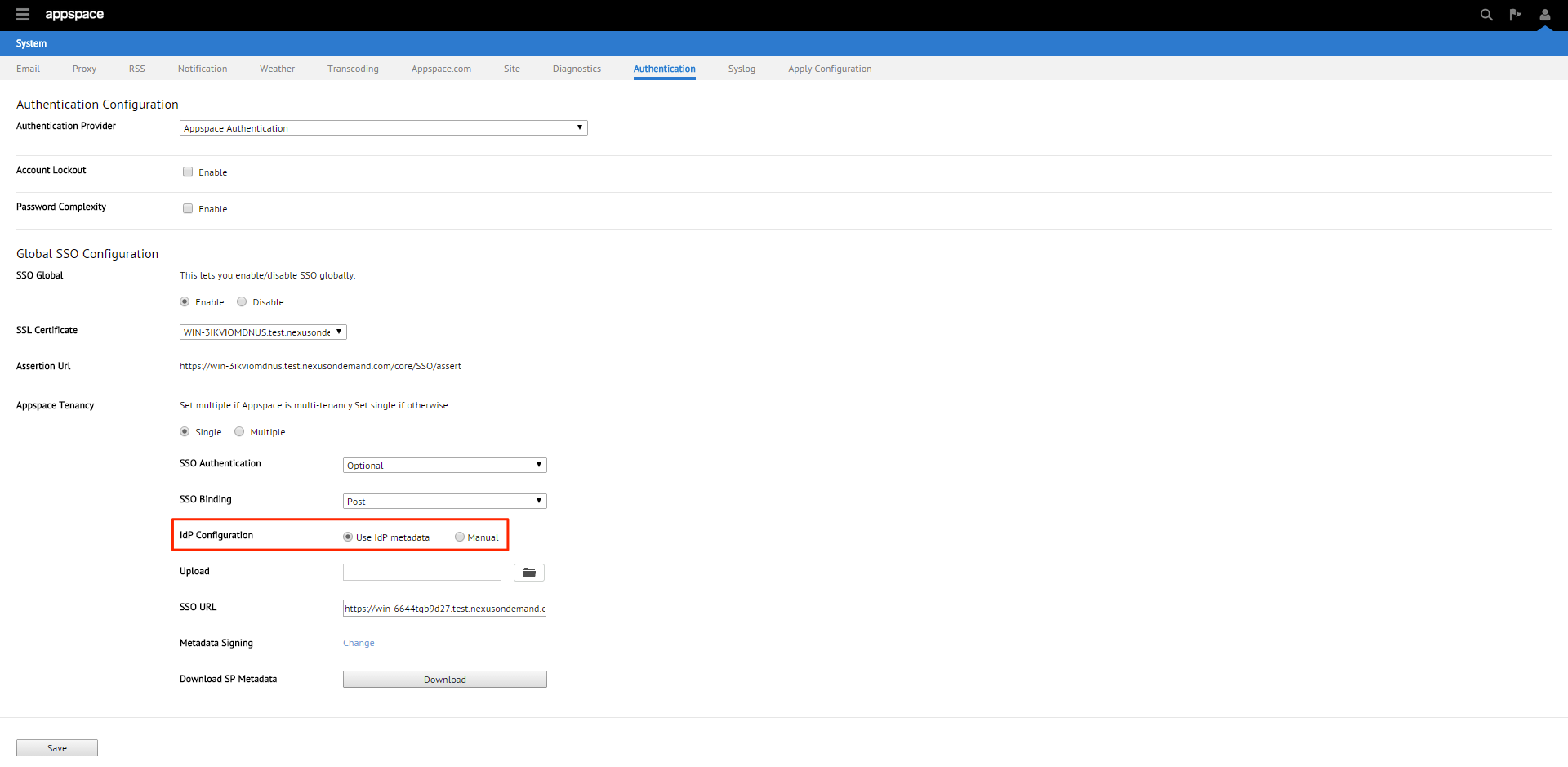
You will be given two Identity Provider (IdP) configuration methods; Use IdP Metadata or Manual. We’ll be using Use IdP Metadata in this example.
Step 10
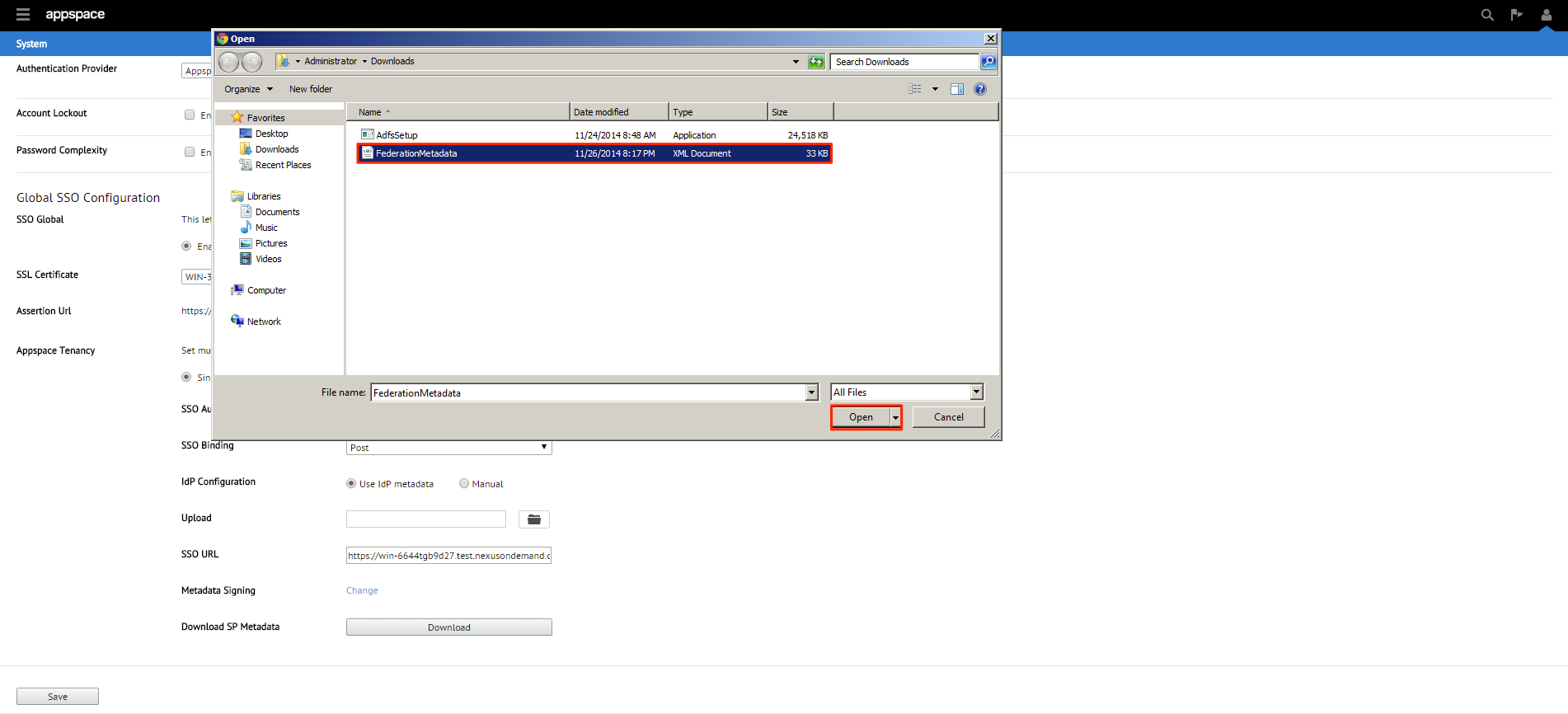
Upon selecting the Use IdP Metadata option, you’ll need to upload the metadata xml file downloaded in Step 1. Click browse and locate that file. Click Open to upload the metadata file to the Appspace server.

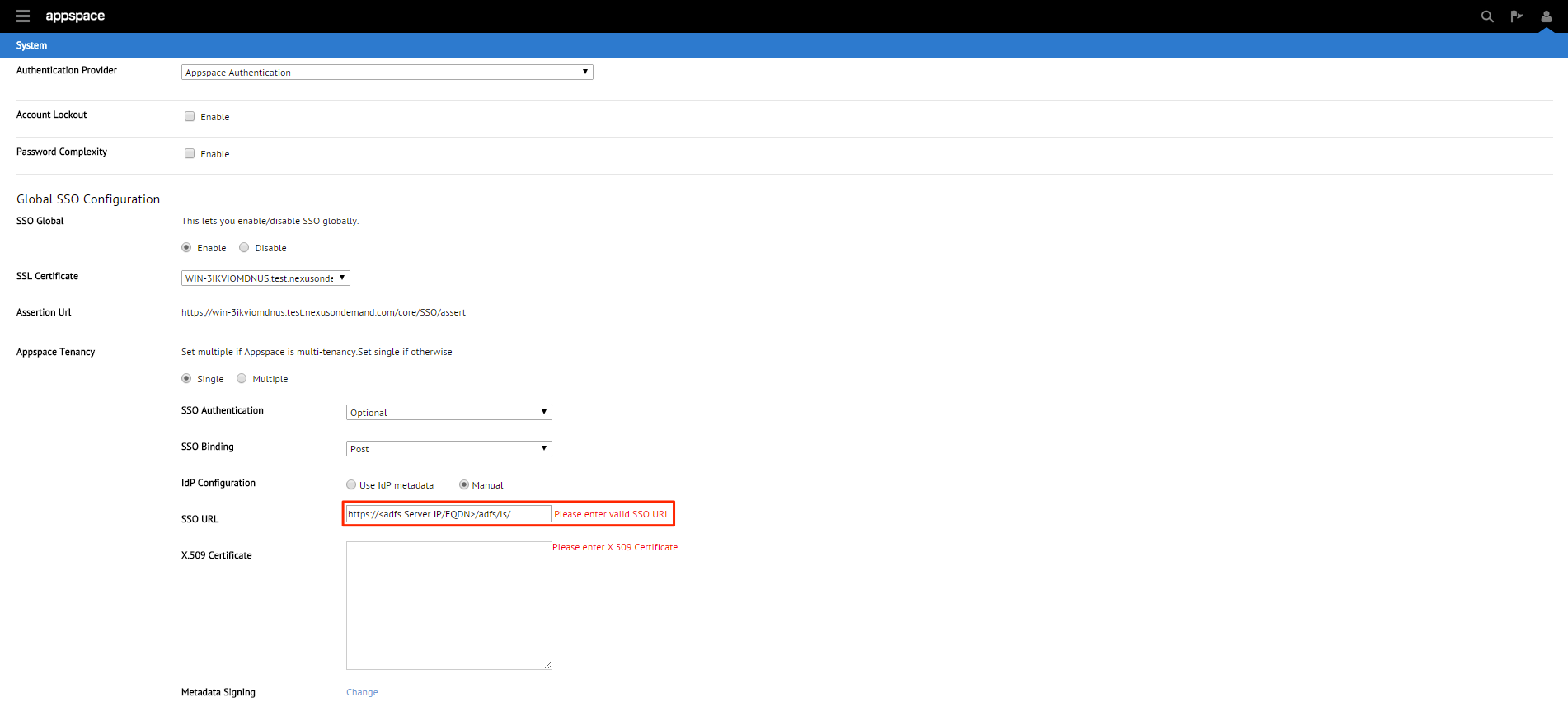
Step 12
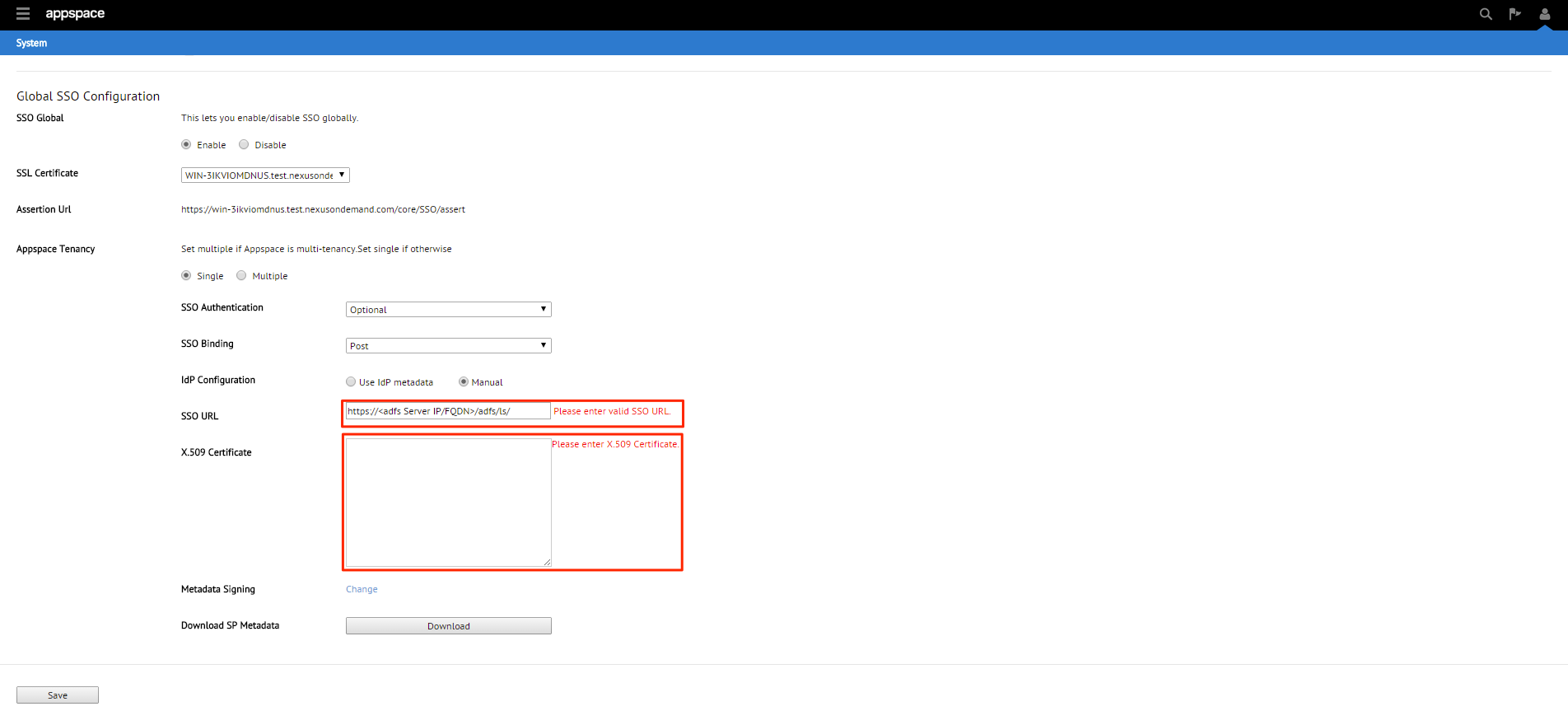
To use the Manual configuration method, you will need to fill in the SSO URL as well as the X.509 certificate.
Step 14
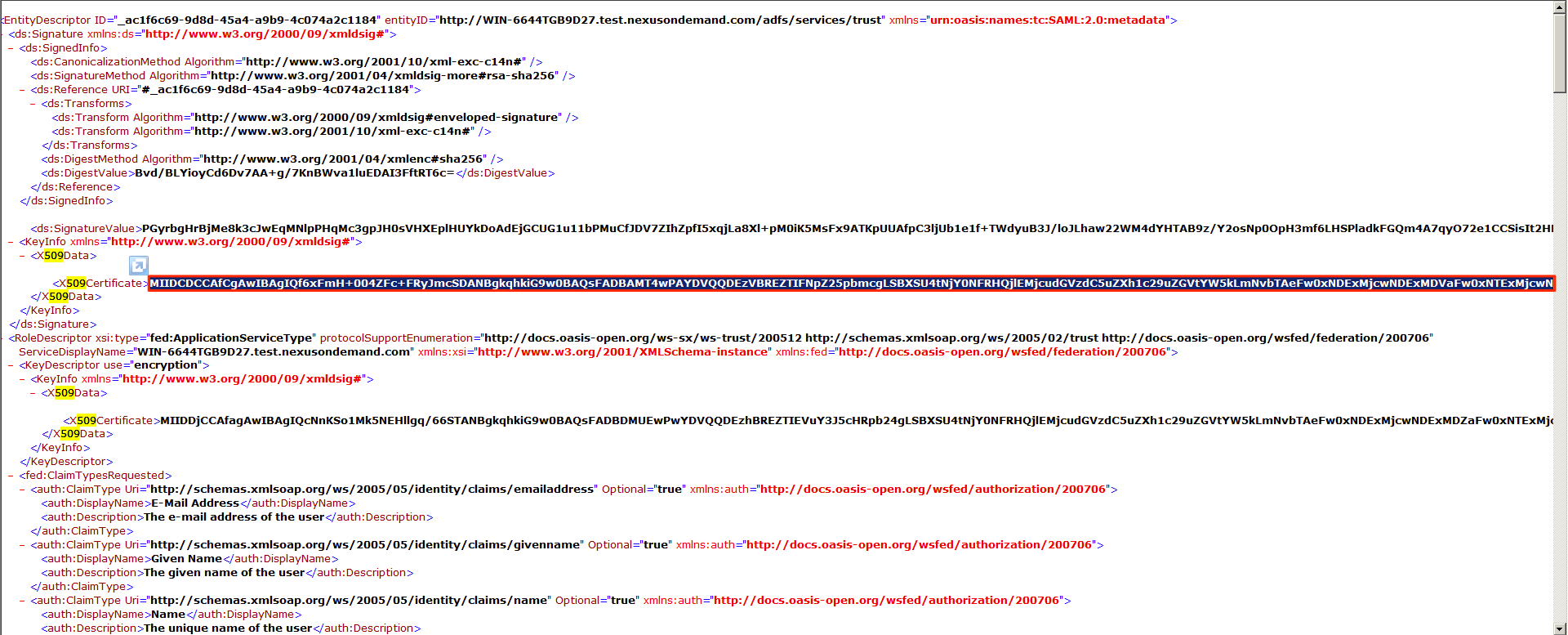
To fill in the X.509 certificate, locate the downloaded FederatedMetadata.xml in Step 1 and open it in a browser.
Step 17
You will finally be given the option to enable or disable Metadata Signing. Click Change to show the options. We’ll be disabling this feature in this example.
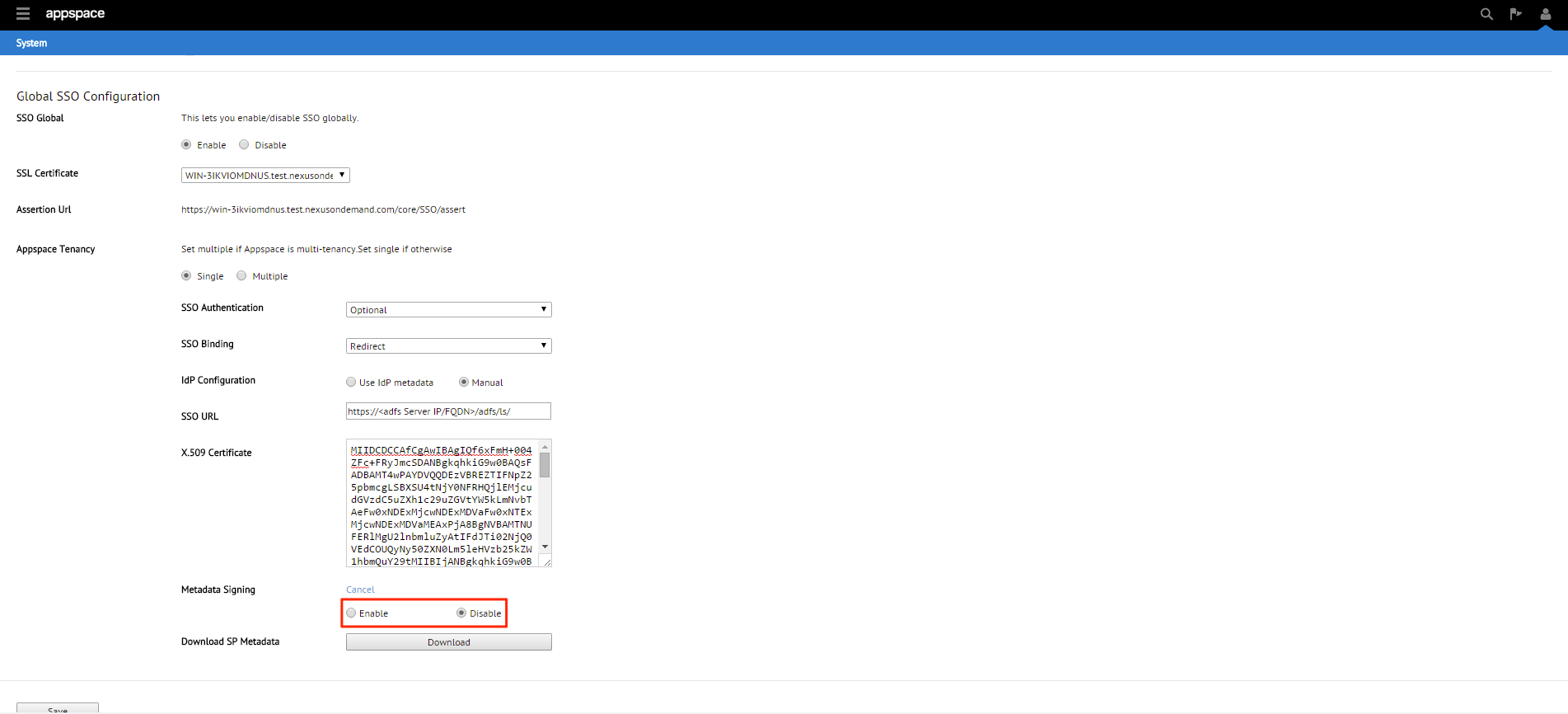
Note
Enabled – The SP metadata file will be generated in an ‘Encrypted’ format
Disabled – The SP metadata file will be generated in a ‘Plain text’ format
Section 5: Configuring ADFS Relying Party Trust
Note
This section is performed on the Identity Provider (ADFS) server.
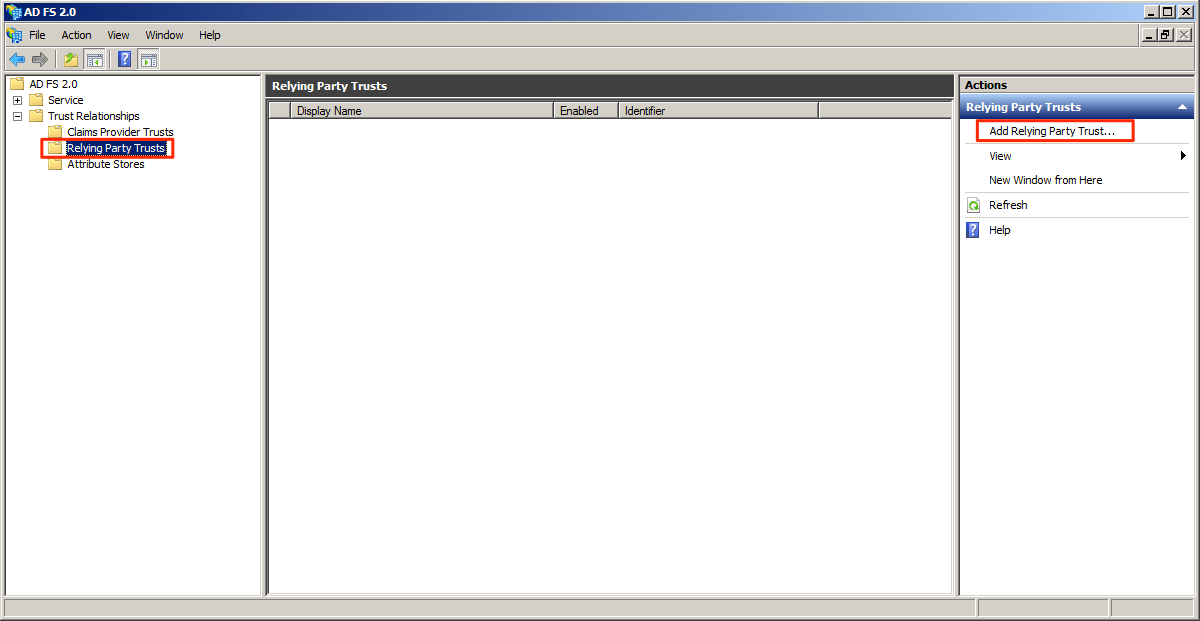
Step 2
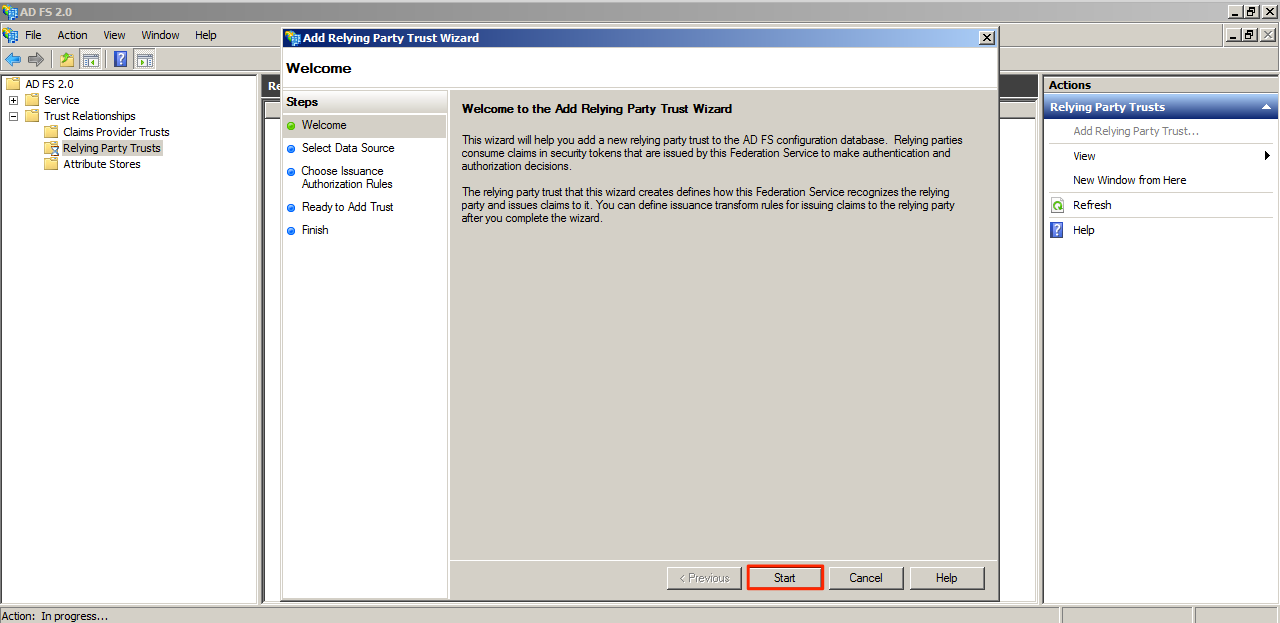
Expand the Trust Relationship folder and select the Relying Party Trusts folder. To add a Relying Party trust click Add Relying Party Trust under the Actions pane.
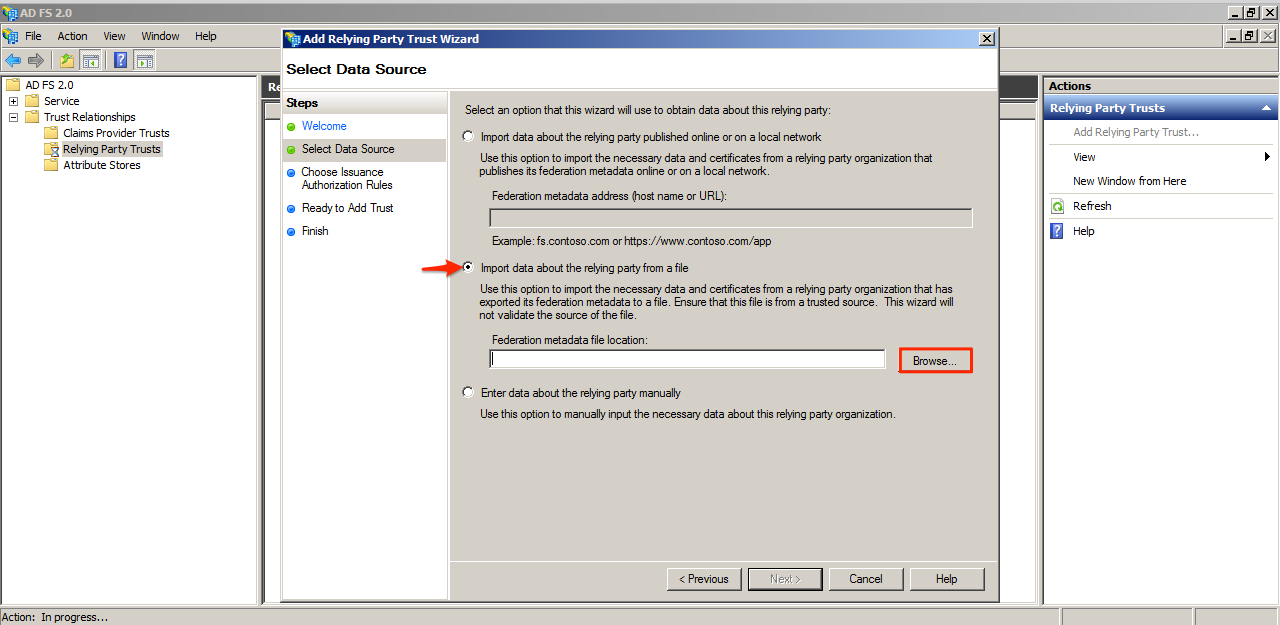
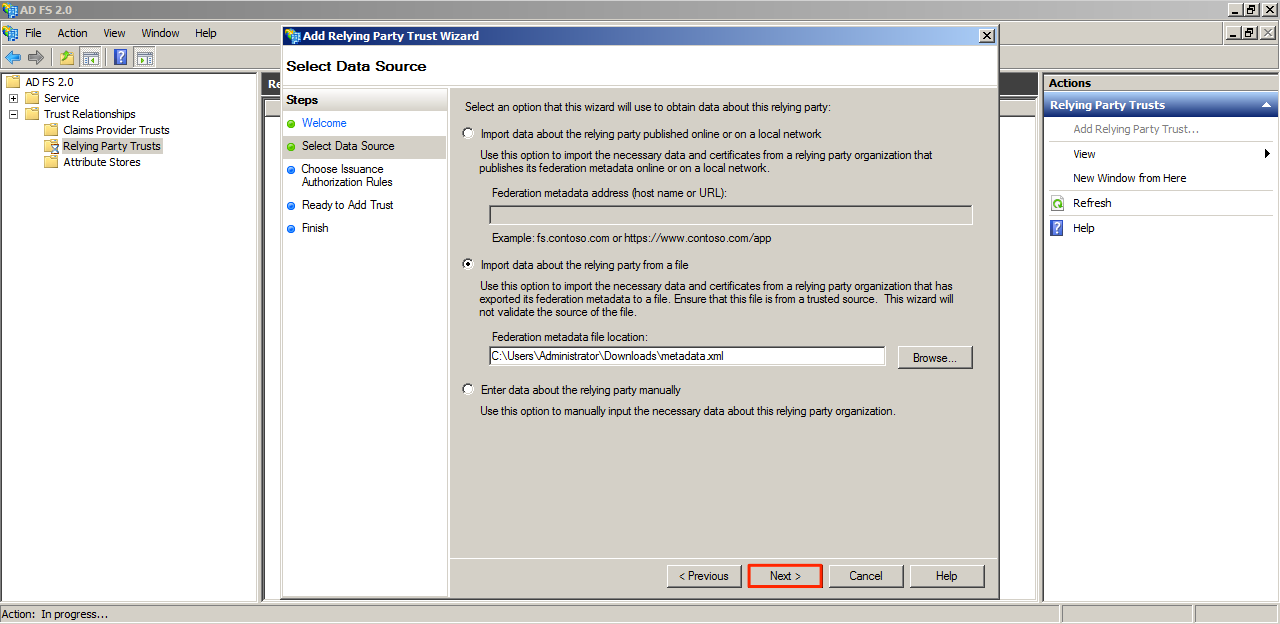
Step 5
Locate and select the metadata file that was downloaded from the Appspace server and click Next.
Step 9
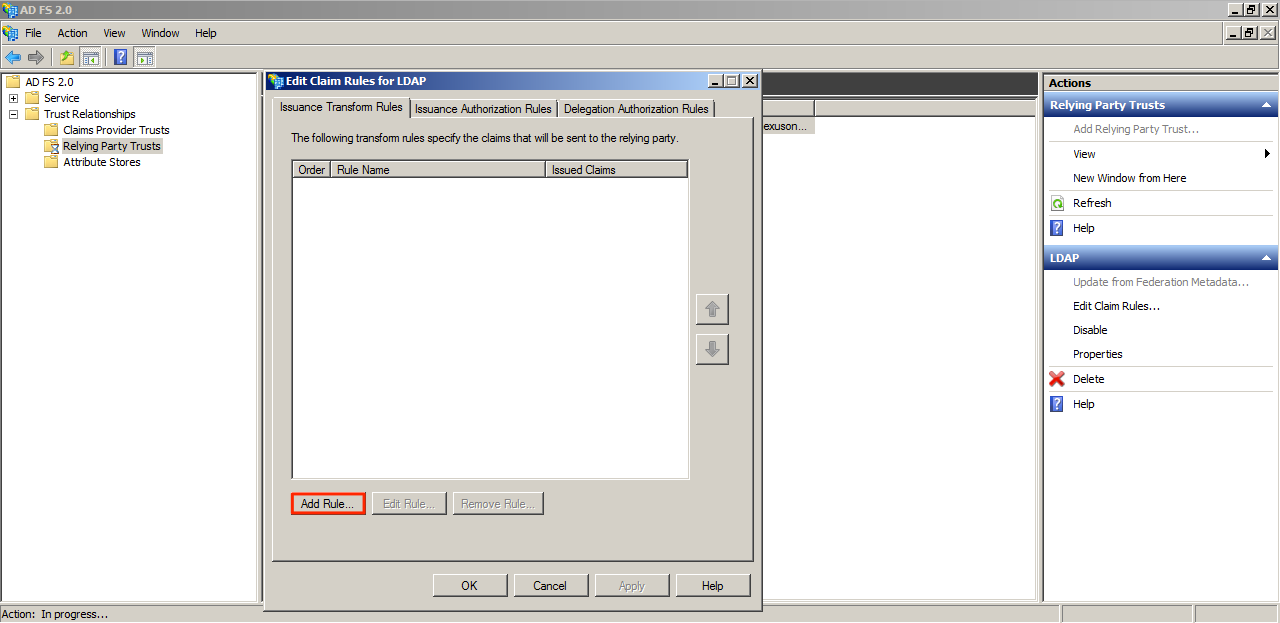
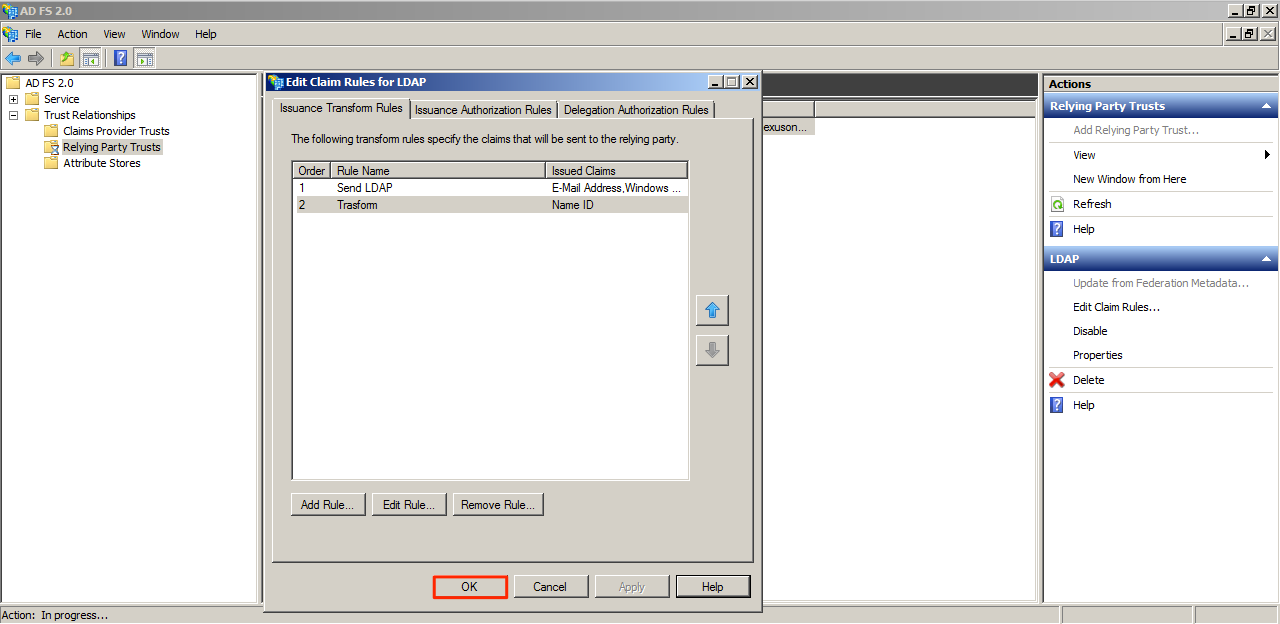
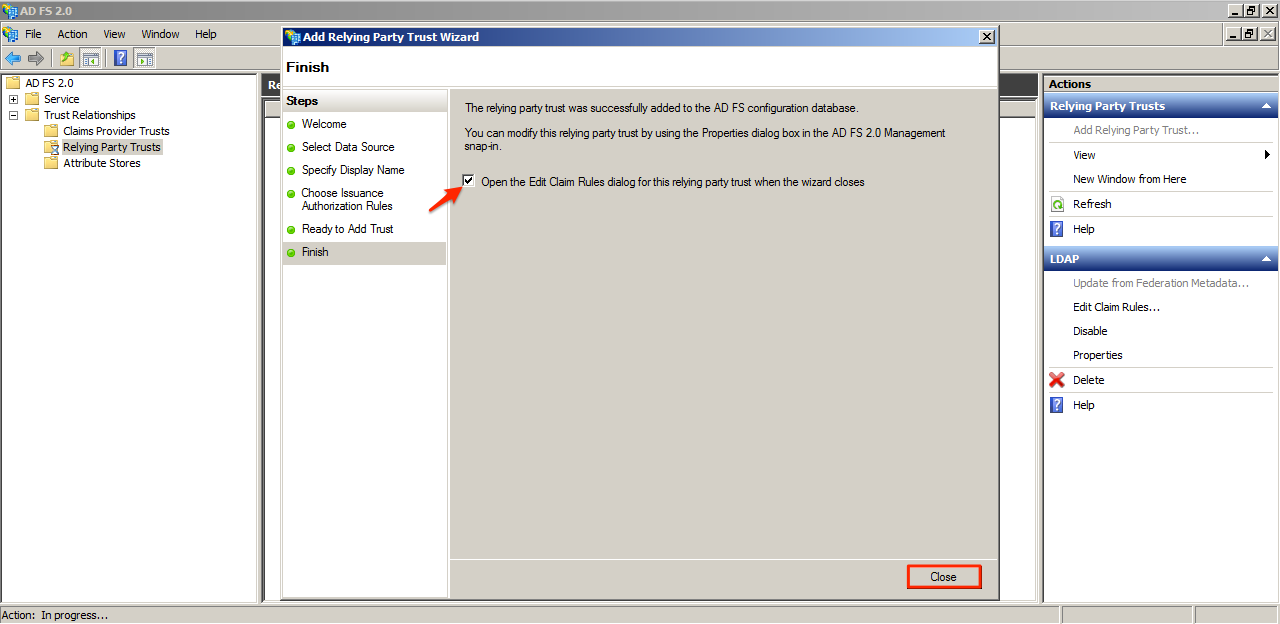
Ensure that the checkbox for “Open the Edit Claim Rules dialog for this relying party trust when the wizard closes” is ticked.
Step 12
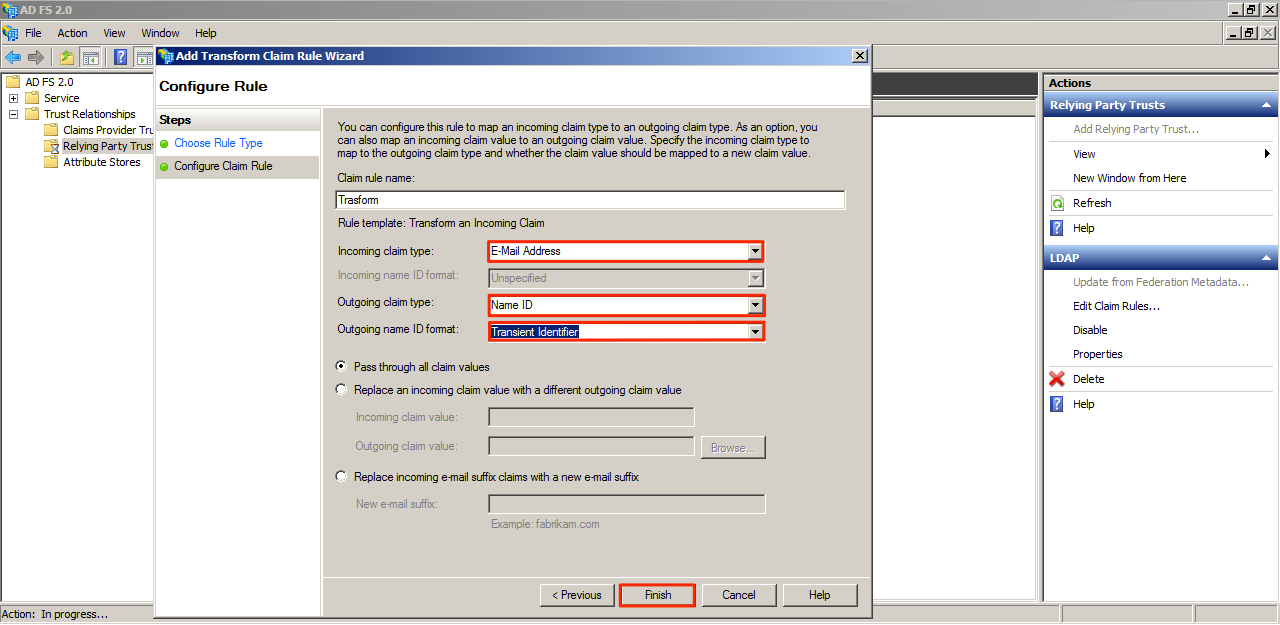
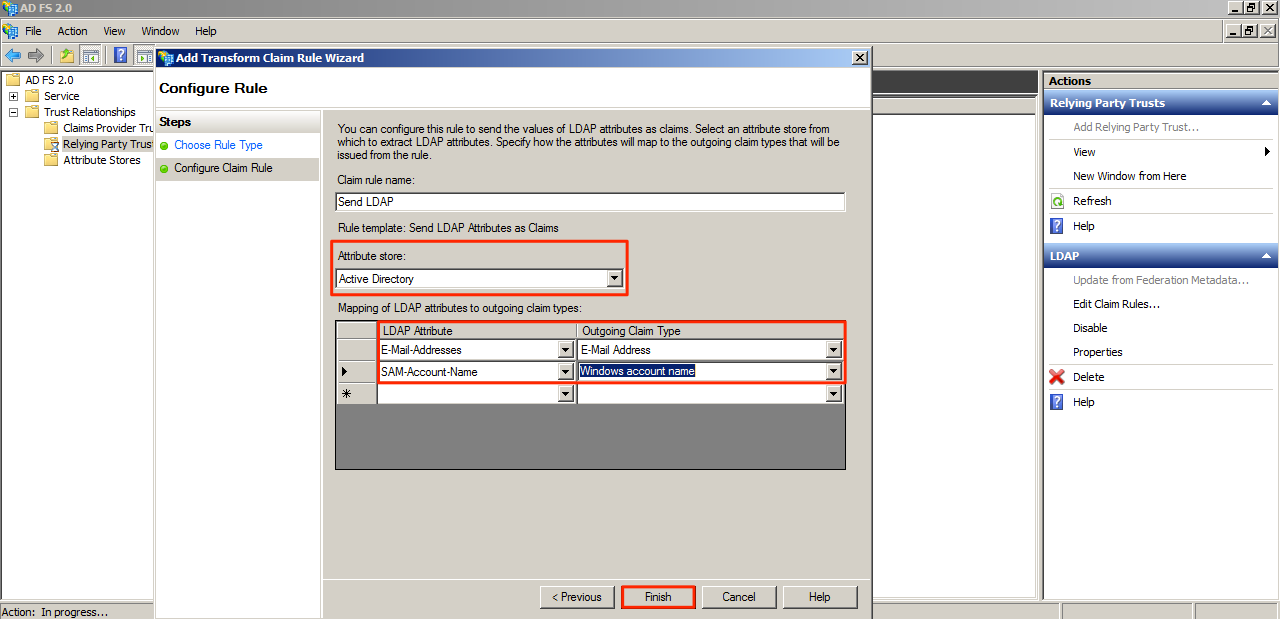
Name the Claim Rule and select Active Directory as the attribute store. Refer to the screenshot below for the Mapping of LDAP attributes to outgoing types value. Click Finish when done.
Note
This step mandates that all Appspace users (authenticating via SSO) are required to have email addresses (can be used as the usernames as well).