Audiences and networks in the application require access to the Active Directory to get information from AD groups. As in M365 there is no direct connection to Azure AD, we have to use the Microsoft Graph API to connect to it.
To use Microsoft Graph API it is necessary to create an app that will act as a proxy between Microsoft Graph and the Appspace SharePoint Intranet.
The following values from the Graph app will be needed in the application:
| Appspace SharePoint Intranet | Graph App |
| ADALRealm | Directory ID |
| ADALClientID | Application ID |
| ADALClientSecret | Key |
Create and configure
An account with administrative permissions (AD Global Administrator) in your Microsoft 365 AD is needed to configure the application. With the Microsoft 365 subscription, it comes by default an Azure AD tenant, so you can use your Microsoft 365 tenant admin user to create and configure the app to use this AD.
Go to Azure portal and log in with your Microsoft 365 tenant admin user.
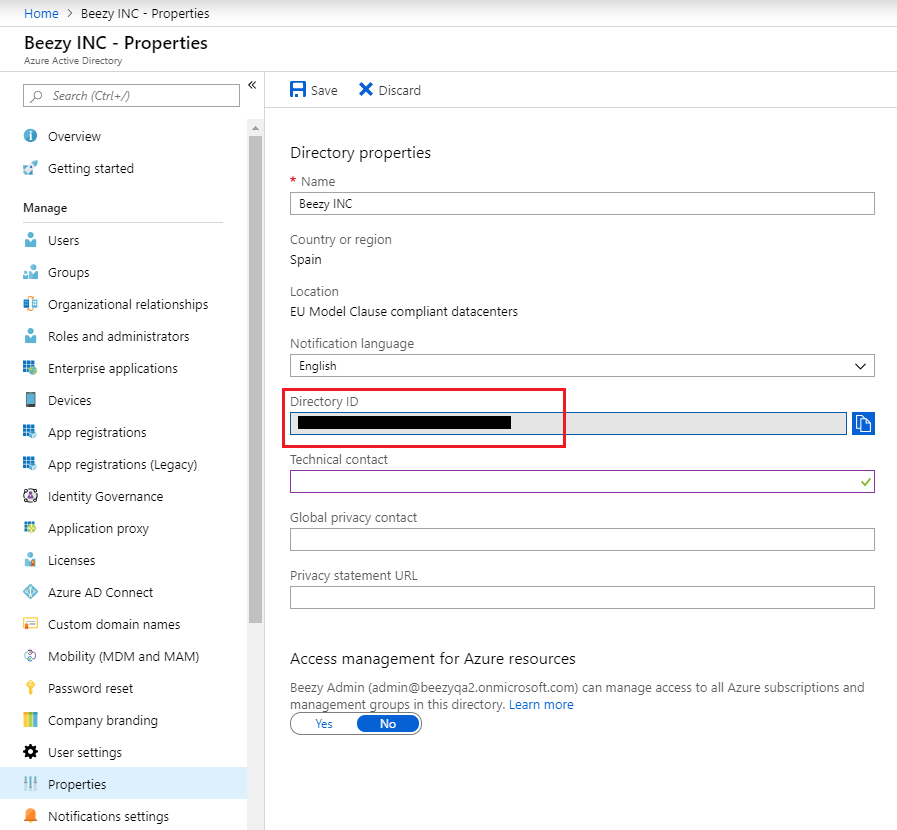
- Browse to “Azure Active Directory” and select the Properties option in the left menu. You can get the Directory ID (ADALRealm) from this page (copy and save):
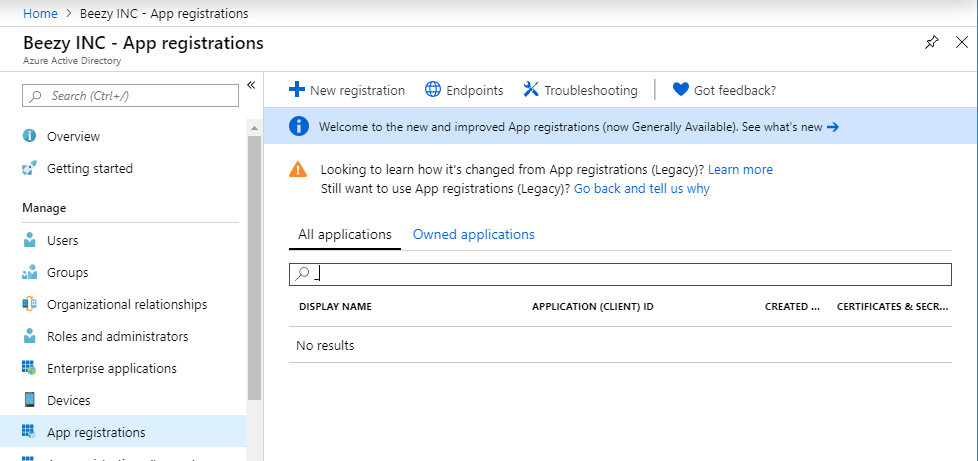
- Select the “App registrations” option in the left menu:
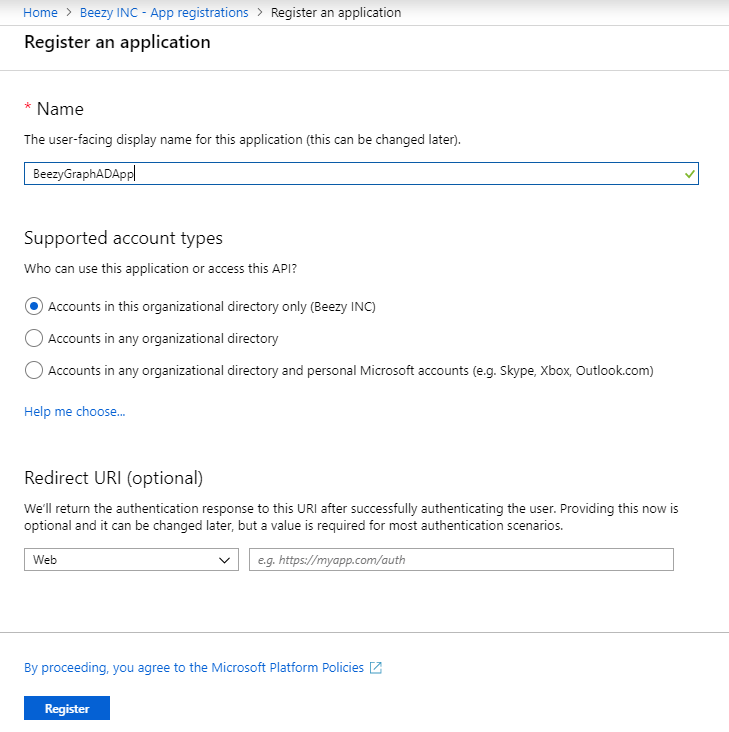
- Click on “New registration” to register the new application. Set the “Name” and check the option “Accounts in this organizational directory only” (default value). Click “Register”.
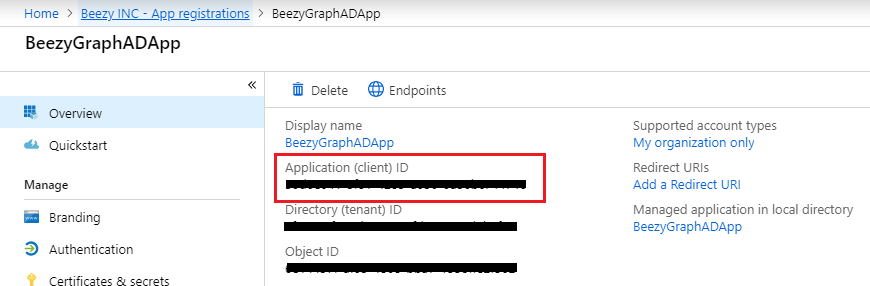
- The new registered app will be shown. You can get the Application ID (ADALClientID) from this page (copy and save):
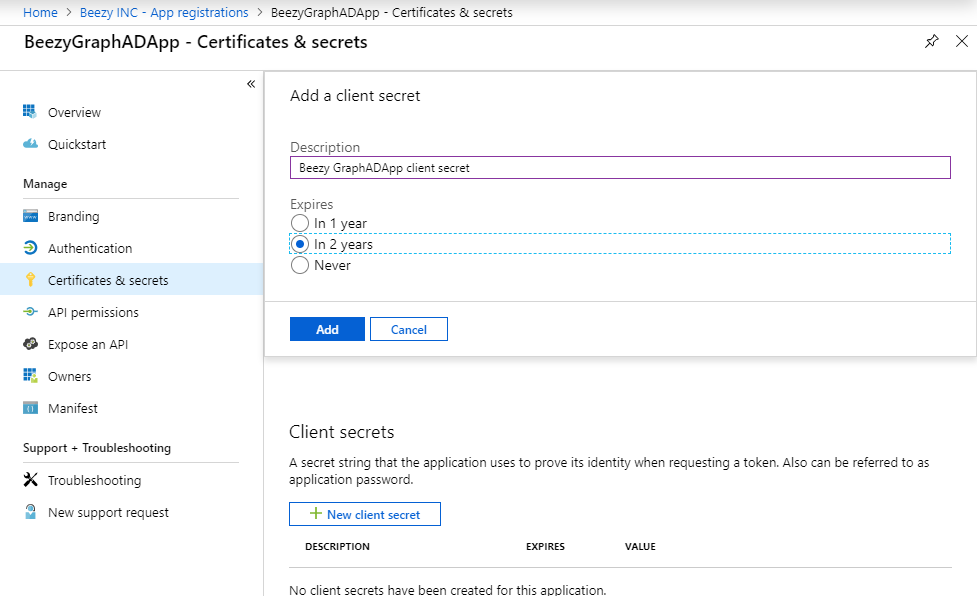
- Create a key to allow external applications to use it. Select “Certificates & secrets” from the left menu. Click “New client secret”, add a description and the time range that it will be valid (Graph API does NOT permit a Never expires secret, so make sure you pick 1 or 2 years expiry):
-
Important! Once the new key is saved, the Keys blade will show you the value of the key. Copy it and save in a safe place, because this is the only moment it will be shown. If you leave the blade, you won’t be able to retrieve it afterwards.
The ADALClientSecret key of Beezy is the value of this key.
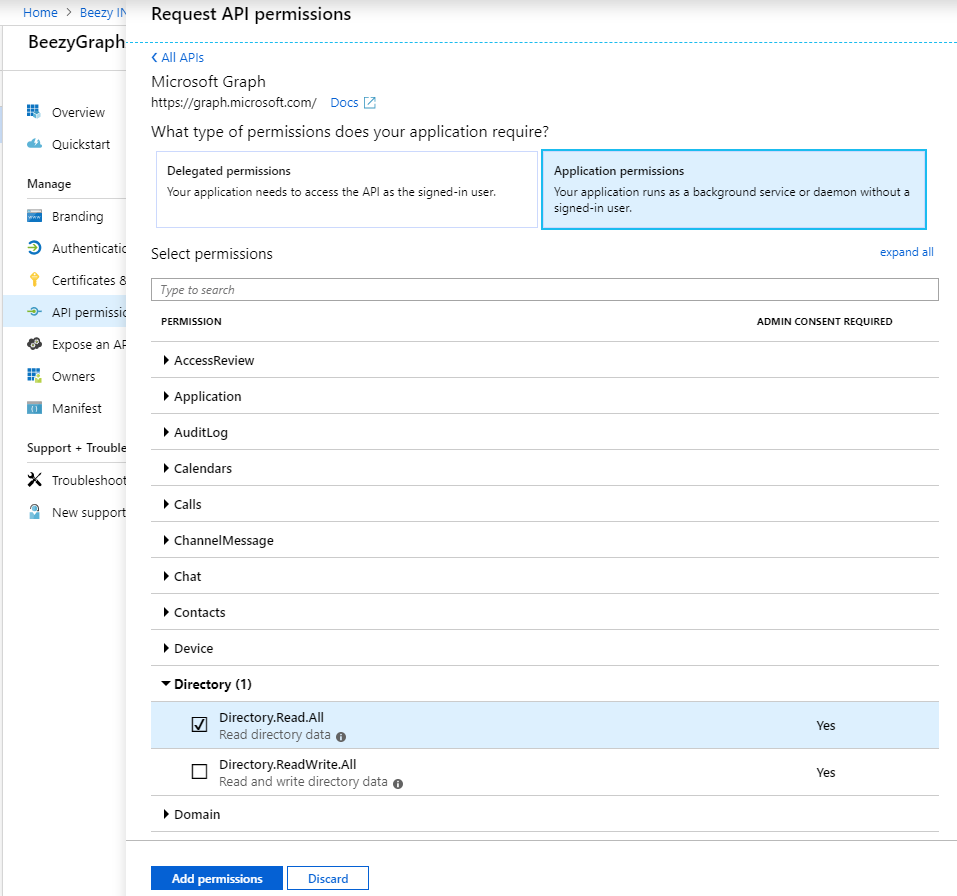
- Grant permissions to Microsoft Graph to the app created. Select the “API permissions” option and in the new blade, click on the “Add permission” button, “Microsoft APIs” and “Microsoft Graph”. Then “Application permissions” and check the “Directory à Directory.Read.All – Read directory data”.
-
Click the “Add permissions” button.
- You can delete the “User.Read” permission.
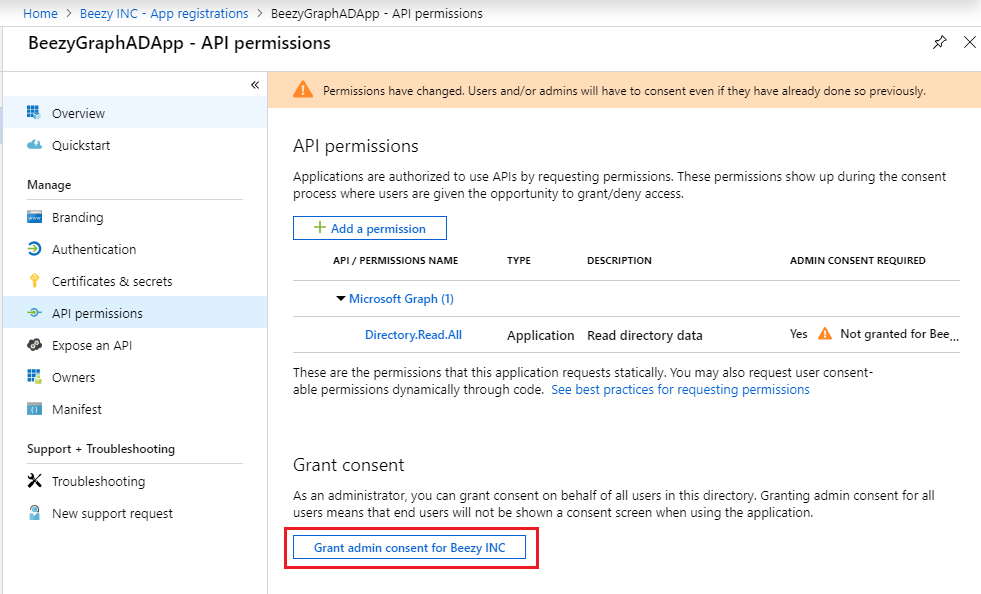
- Finally, click the “Grant admin consent” button to make effective these permissions.
Set app keys to App Service
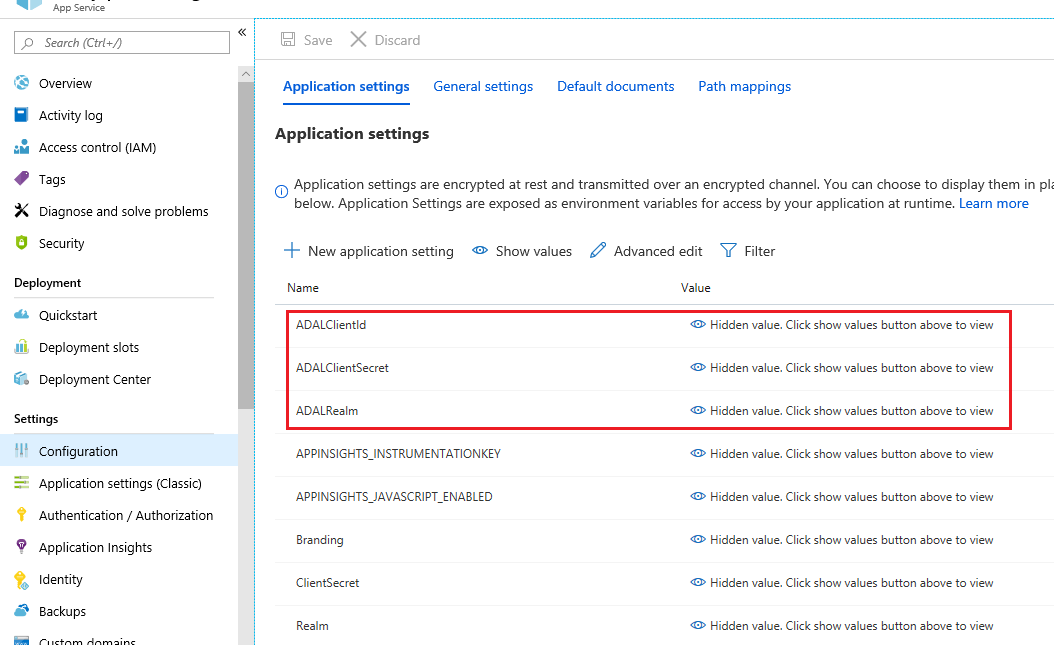
- The app to connect to Microsoft Graph is already configured and the values for the ADALRealm, ADALClientId, and ADALClientSecret have been obtained. We just need to set these values in the Beezy App Service settings as shown in the image below. From App Service, Configuration:
- You can test the connection to the Graph API with the following PowerShell from Install folder:.beezy-TestGraphApi.ps1 -ADALRealm “your_ADALRealm” -ADALClientId “your_ADALClientId” -ADALClientSecret “your_ADALClientSecret”If the connection to Graph API succeeds with the provided parameters, you’ll see the Azure AD groups of your tenant.
Was this article helpful?