- Article purpose: This document provides an introduction to configuring SSO with Appspace 7.1 and later for cloud and on-prem deployments.
- Business problem: Many enterprises would like to use cloud-based identity and access management tools to manage their employee’s Appspace credentials.
- Solution: Appspace provides several seamless SSO workflows for users with Appspace accounts.
- Conclusion: Appspace strives to support secure logins for implementing SSO with third-party identity providers and seamless collaboration with the Appspace platform.
WHAT’S IN THIS ARTICLE:
Introduction
An increase in the adoption of cloud-based enterprise solutions has resulted in the widespread usage of cloud-based identity and access management tools by enterprises. Thus, the demand for simplified password management with single sign-on (SSO) solutions for easy employee application logins, too has escalated.
Historically customers using third-party identity providers (IdP) for their enterprises have had to configure SSO and recreate users separately for Appspace, which was a cumbersome process. Appspace now supports Just-in-Time user creation, eliminating the need for these duplicate administration efforts.
Solution Overview
SSO enables users to access all their cloud-based enterprise solutions by using only one set of login credentials for access to all applications configured with the IdP. Appspace has a wide compatibility for all major identity providers that support SAML 2.0 (Security Assertion Markup Language).
As Appspace strives to make life easier for our customers, we have also improved our SSO offering with seamless integration with third-party identity provider vendors such as Okta and OneLogin for easy access logins.
Appspace provides the following two additional seamless SSO configuration options for users on an external IdP:
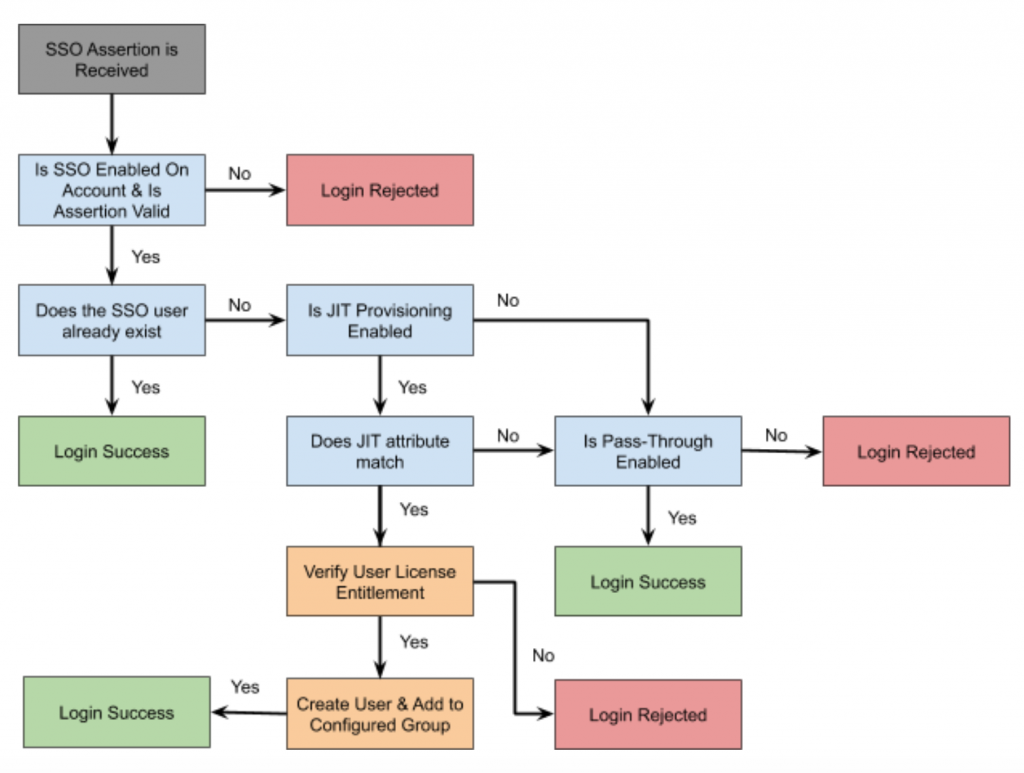
- Just-in-Time (JIT) provisioning: when a user already configured in an access management tool (i.e. Okta/OneLogin) signs-in to the Appspace console for the first time using SSO, JIT provisioning uses a SAML assertion to automatically create users on the Appspace account if they do not already exist. This eliminates the need to create user accounts separately for Appspace. This feature is available for cloud-only.
- Pass-through authentication: (Only for on-prem deployments) users in an organization with an external IdP are automatically authenticated via SSO/LDAP and automatically created in the Appspace platform and assigned Appspace’s Basic IDs. However, they cannot access the Appspace console; they can only view channels assigned to them using the channel browser. Pass-through authentication allows users to log on to applications in domains in which they do not have a valid user account. This feature is ideal for on-prem deployments, and is disabled by default on cloud.
SSO Authentication Workflows
There are four distinct SSO authentication scenarios for users of an Appspace account:
- Only SSO is enabled. Neither JIT provisioning or pass-through authentication is enabled.
- SSO with JIT provisioning is enabled, but pass-through authentication is not enabled.
- SSO with pass-through authentication is enabled, but JIT provisioning is not enabled.
- SSO with both JIT provisioning and pass-through authentication is enabled.
Below is the SSO account authentication workflow:
Requirements
JIT Provisioning
- An Identity Provider that is SAML 2.0 compliant.
- IdP metadata, or the SSO URL and x.509 certificate.
- Appspace account with Account Owner credentials to configure SSO settings.
- An Appspace User Group to act as the default user group for newly created JIT-provisioned users.
- Configure a SAML identification attribute flag to identify an IdP user as one that should be created in Appspace. This attribute can be selected by the IdP administrator and should be configured in both the IdP and in Appspace.
- Configure the IdP to pass the correct JIT-related attributes to Appspace such as attribute mappings for the First Name and Last Name fields.
- Configure JIT as per the specific access management tool (i.e. Okta/OneLogin) and ensure that any Appspace-specific attributes are created and passed with each assertion.
- Make Appspace available in the IdP-specific App Store catalog.
Pass-Through Authentication
- An Identity Provider that is SAML 2.0 compliant.
- IdP metadata, or the SSO URL and x.509 certificate.
- Appspace account with Account Owner credentials to configure SSO settings.
Configuration
Please refer to this article for instructions to Configure Single Sign-On (SSO) and Just-inTime (JIT) for Appspace Cloud.
Conclusion
Appspace provides SSO support with a wide compatibility of all major Identity Providers that support SAML 2.0. SAML is a versatile and complex protocol allowing for a number of possible configurations, as are the different access management tools. As such each customer setup can be unique and challenges can arise during configuration. ContactAppspace Support for assistance and guidance.
Was this article helpful?