The Appspace platform can be configured to integrate with Security Assertion Markup Languages (SAML) 2.0 compliant identity providers (IdP), allowing for seamless and secure connections using a single set of credentials, simplifying username and password management with Single Sign-On (SSO). When you log in to Appspace, your credentials are authenticated by the IdP, and a SAML 2.0 assertion is sent to Appspace via the web browser to allow access to Appspace. Additionally, Appspace provides the following seamless SSO configuration options for organizations utilizing an external IdP:
- Just-in-Time (JIT) provisioning: when a user already configured in an access management tool (i.e. Okta/OneLogin) signs in to the Appspace console for the first time using SSO, JIT provisioning uses a SAML assertion to automatically create users on the Appspace account if they do not already exist. This eliminates the need to create user accounts separately for Appspace.
This article provides the instructions to enable and configure Single Sign-On (SSO) on an Appspace 8.0 on-prem deployment, while providing the option to enable Just-in-Time (JIT) provisioning:
Prerequisites
- An Identity Provider that is SAML 2.0 compliant.
- IdP metadata, or the SSO URL and the x.509 certificate. ImportantPlease ensure the NameID in the SAML assertion is the email address of the user.
Appspace uses the following NameID format: urn:oasis:names:tc:SAML:1.1:nameid-format:emailAddress - Appspace account with Account Owner credentials to configure SSO settings.
- Make Appspace available in the IdP-specific App Store catalog.
JIT Provisioning
- An Appspace User Group to act as the default user group for newly created JIT-provisioned users.
- Configure a SAML identification attribute flag to identify an IdP user as one that should be created in Appspace. This attribute can be selected by the IdP administrator and should be configured in both the IdP and in Appspace.
- Configure the IdP to pass the correct JIT-related attributes to Appspace such as attribute mappings for the First Name and Last Name fields.
- Configure JIT as per the specific access management tool (i.e. Okta/OneLogin) and ensure that any Appspace-specific attributes are created and passed with each assertion.
Enable and Configure Single Sign-On (SSO) Authentication
Follow the instructions below to enable and configure SSO (Single Sign-On) authentication for Appspace.
- Log into your Appspace console.
- Click Users from the ☰ Appspace menu.
- Click ⚙ Settings, and click Account Authentication from the side-panel menu.
- Select Single Sign-On (SSO) from the Authentication Method from the drop-down menu to enable and configure SSO.

- Select the Login Method:
- SSO only – Users will be required to sign in with their single sign-on credentials. Only Account Owners can sign in with an Appspace password.
- SSO or Appspace Credentials – Account Owners and users will be able to sign in with either their Appspace or single sign-on credentials.
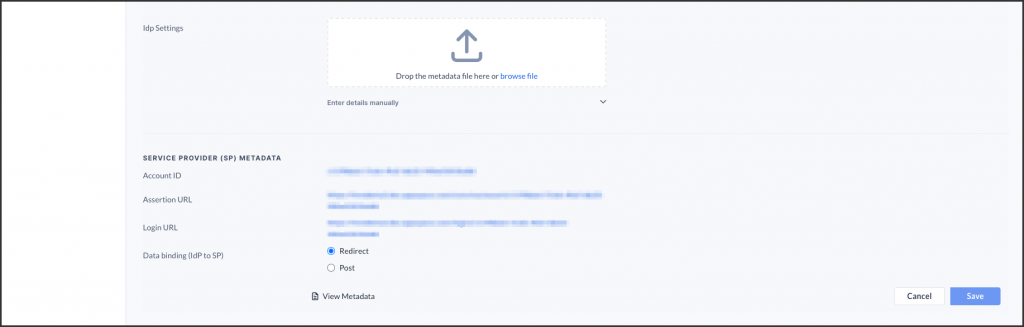
- Configure the IdP settings using one of the following methods:
 ImportantPlease ensure the NameID in the SAML assertion is the email address of the user. Appspace uses the following NameID format: urn:oasis:names:tc:SAML:1.1:nameid-format:emailAddress
ImportantPlease ensure the NameID in the SAML assertion is the email address of the user. Appspace uses the following NameID format: urn:oasis:names:tc:SAML:1.1:nameid-format:emailAddress- Drop or upload the IdP metadata XML file.
- Manually enter the SSO URL and X.509 Certificate details in the relevant fields.
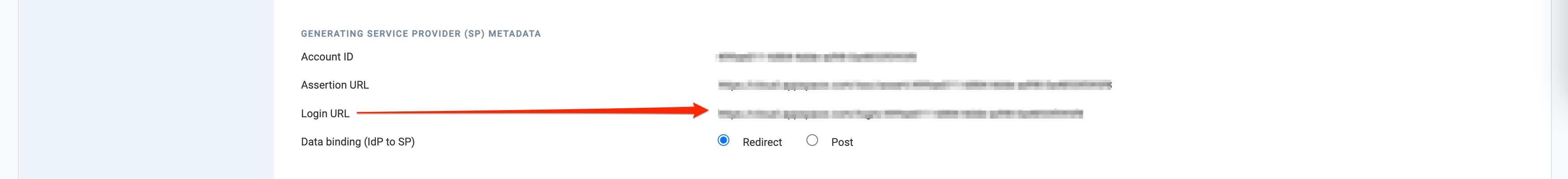
- In the SERVICE PROVIDER (SP) METADATA section, select the desired Data binding (IdP to SP) option:
- Redirect – Users are redirected to the Identity Provider. SSO details will be passed in a query string with “?SAMLRequest=……” as part of the URL.
- Post – SSO details are passed using the POST method. Ensure the Identity Provider has direct access to the Appspace Server for this method to work.
- Click Save once all SSO configurations have been made.
Configure Just-In-Time (JIT) User Provisioning
- Log into your Appspace console.
- Click Users from the ☰ Appspace menu.
- Click ⚙ Settings, and click User Provisioning from the side-panel menu.
- Select the JIT (VIA SAML) radio button from the User Provisioning options to display the JIT settings.
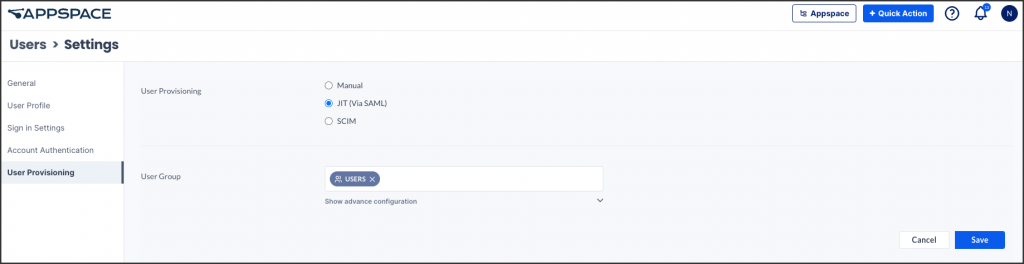
- Enter the User Group to which new users will be assigned to, in the text field.NoteBy default, the SAML attributes are mapped to first name and last name of the IdP configuration.
- Optionally, click the Show advanced configuration link, if you would like to map the SAML attributes to a value that matches your IdP implementation.
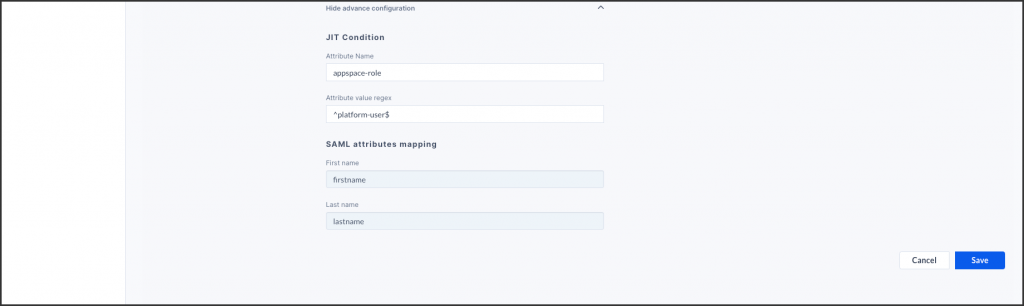
- Enter in the JIT condition Attribute Name and Attribute Value Regex. NoteThe SAML identification attribute flag, Attribute=”appspace-role” and Value=”^platform-user$”.
This value is a regular expression. If the attribute value matches this regular expression then the user is provisioned via JIT. Regular expressions allow very flexible matching for the wide array of IdP configurations.
This allows you to only provision platform users for some employees, while allowing for pass-through access. By default, this looks for an attribute called “appspace-role” with a value of “platform-user$”, however this is designed to be flexible and has a regex match. You could also make it match all users by setting it to something like attribute = ‘mail’ value = ‘.*’ (regex wildcard that will match any email value). - Enter in the SAML attributes mapping for the First name and Last name.
- Enter in the JIT condition Attribute Name and Attribute Value Regex.
- Once done, click Save to complete the JIT configuration settings.
Was this article helpful?