This article provides the instructions to configure Active Directory or LDAP (Lightweight Directory Access Protocol) for single, and multiple domains. Note that this configuration is portal-wide and affects all tenant accounts within Appspace.
Prerequisites
- Portal Administrator privileges on your Appspace on-prem server.
- Active Directory enabled with administrator-level credentials
This feature has been designed to work with a flat Active Directory structure.Important
Configure Active Directory Authentication
Important
You MUST setup the Active Directory in your server with an Administrator-level account BEFORE going through this authentication process.
- Navigate to System > Configuration from the Appspace menu.
- Click the Authentication tab, and select AD Authentication from Authentication Provider the drop-down menu.
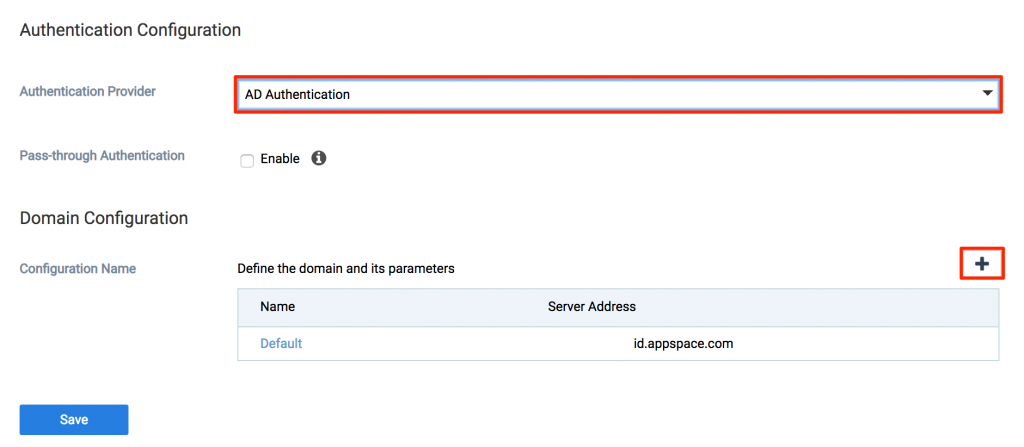
- Click the Add icon in the Configuration Name section to add a domain.
- Optionally, you may enable Pass-through Authentication, by checking the Enable option, and entering the e-mail domain. Note
Pass-through authentication enables you to utilize an external IdP so that your users can access channels through the Appspace App without using Premium User IDs. - Complete the relevant details in the AD Authentication Parameters section, including Server Address, Port, Username, Password, Default Account and Base DN. Click on Validate Connection to verify connection is successful to the AD. Warning
Please create an Administrator-level account (in this case, Superuser) in your Active Directory BEFORE proceeding with this step to avoid Appspace system lock-outs. This user will replace the default portal administrator.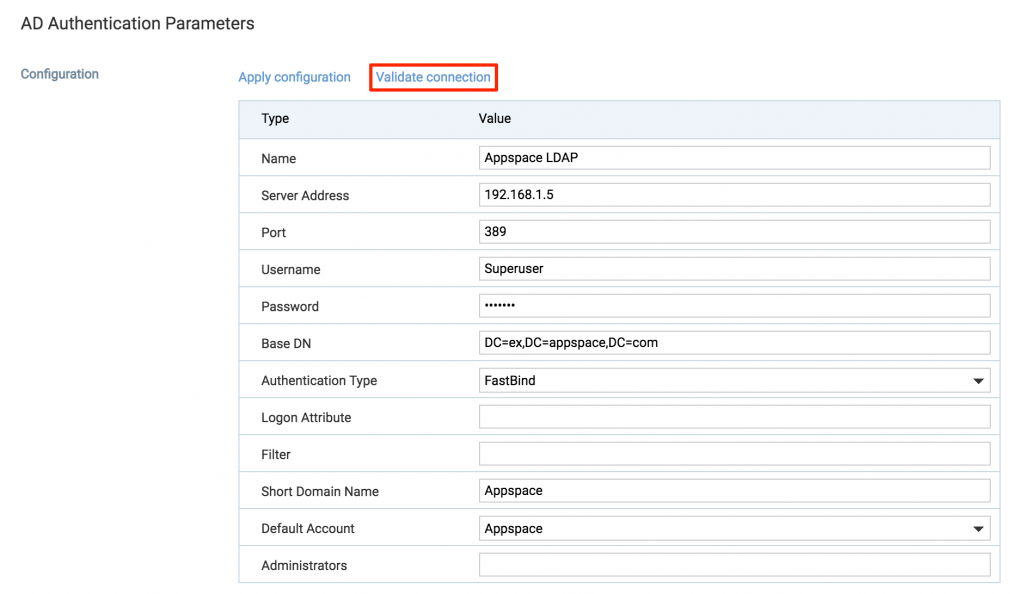 Important
Important
The credentials shown in the screenshot are provided only as an example. For more information on obtaining Active Directory credentials, please consult your organization’s IT Department or personnel.- Requires the full CN name of users
- Ports: 389 (Non-SSL) / 636 (SSL)
- Server Address: The AD server’s IP should never be used when deploying with SSL
- Authentication Type: FastBind (Case sensitive)
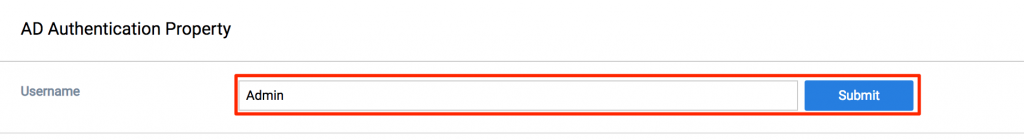
- To validate the configuration, enter in any username that belongs to the domain in the Username field, and click Submit. A successful validation will display a property table of the user.
 Note
Note
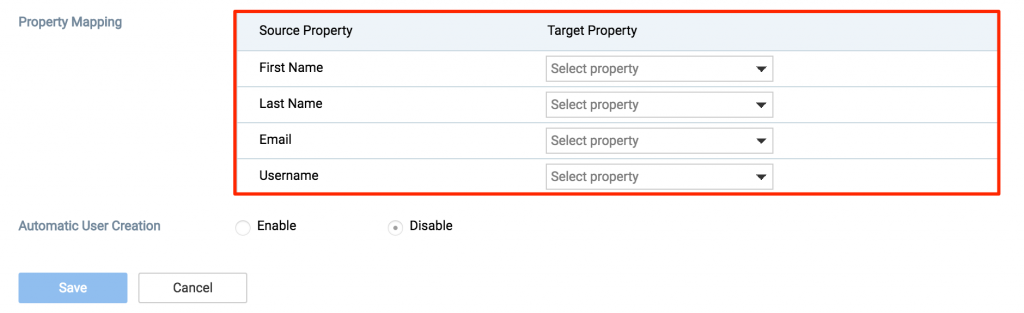
If validation fails please ensure that the username belongs to a user that belongs to the Domain in question and also confirm the AD configurations are populated correctly. - Once connection is validated proceed to the Property Mapping section to map the Source Property of the user to the Target Property available from the drop-down list. Sample default values:
- FirstName: givenname
- LastName: sn
- Email: mail
- Username: samaccountname
- Set the Automatic User Creation to Enable or Disable.
- The Enable option will allow users who do not have an existing Appspace login to log in and it will automatically create a login for the user. Setting this option however disables the pass-through authentication.
- The Disable option will allow Administrator to manually Import users however Property mapping must be setup prior to this.
- Click Save once complete, and Yes to confirm settings.
- The system should automatically detect a change to the Appspace settings and prompt you with a notification at the top of the page. Click the Click Here link.
- You will automatically be taken to the Apply Configuration tab. To finish applying the changes to the system settings, enter your Windows Server credentials and click Apply. Warning
You must input your Windows Server Administrator credentials or an account with local administrator privileges to make and apply changes to server settings.
This is NOT your Appspace on-prem server administrator credentials or your Appspace Cloud user credentials.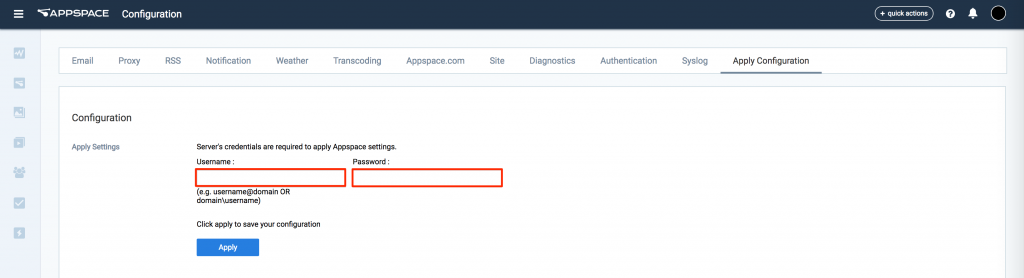 Note
Note
In the event of an error message, please verify your authentication settings and credentials. Press the OK button to try again. - Click Yes to confirm and to restart your Appspace server. You should see a message indicating the server restart progress.
If all the details and credentials were entered correctly, allow a few moments of inactivity while the system restarts itself. click OK to complete the process. - Once Appspace has restarted, verify that the AD authentication has been processed by logging out of your Appspace account and logging in again using the AD username (Superuser) and password credentials.
- If Automatic Creation is enabled it will automatically create the user and upon successful creation user will be presented with the EULA. Click Accept to proceed.
Roll Back Active Directory Authentication
In some deployments (such as an On-Prem installation), you may need to roll back AD Authentication and revert back to Appspace Authentication. The following guide explains the necessary steps to perform this task.
- On your Windows server computer, locate the Appspace installation folder. Browse to the MediaNetConfig folder (by default it is located at C:/Nexus/MediaNetFTP/FastNetV2/MediaNetConfig).
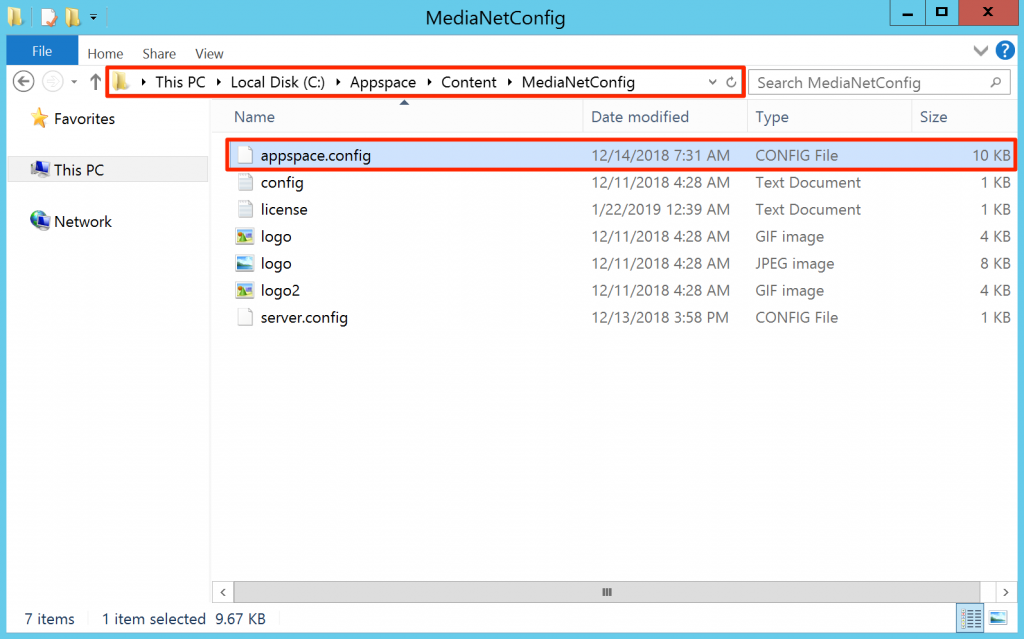
- Open the appspace.config file as a text file. Locate the key=”defaultAuthenticationProvider” line, and change the value to “NCSMySqlAuthenticationService” and save your changes.

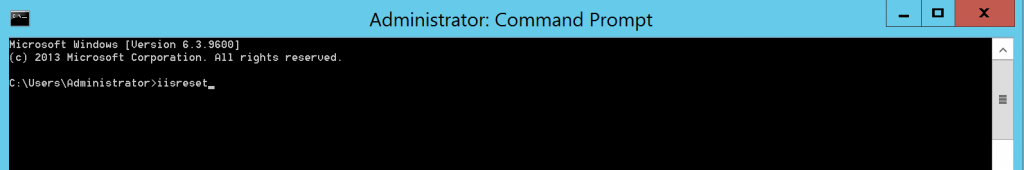
- Open the command prompt, and key in IISReset to reset your settings. You may now log in to Appspace using the default Appspace Authentication credentials.
Was this article helpful?